North Korean Threat Actors Exploit LinkedIn for Malware Distribution
- North Korean hackers post fake job offers on the recruitment website LinkedIn to trick people adjacent to the crypto sector.
- Bogus coding challenges and VP roles are used as a lure, eventually making the targets download malware on their devices.
- ZIP archives and PDFs the threat actors send actually contain the COVERTCATCH malware strain.
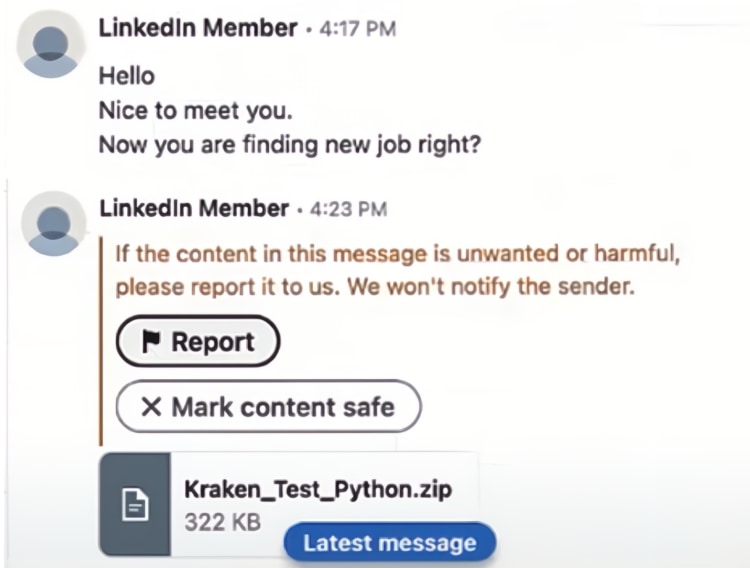
Threat actors affiliated with North Korea have been seen deploying the COVERTCATCH malware through deceptive job recruitment schemes via LinkedIn, targeting developers in decentralized finance (DeFi) and the wider Web3 sector.
According to a report by Google-owned Mandiant, these attacks begin with social engineering methods utilizing LinkedIn to initiate contact under the guise of legitimate job offers. Once communication is established, the attackers send a ZIP file containing the COVERTCATCH malware disguised as a Python coding challenge.
Upon execution, the malware compromises the target's macOS system by downloading a second-stage payload, ensuring persistence via Launch Agents and Launch Daemons.
COVERTCATCH is just one part of various North Korean operations, such as Operation Dream Job and Contagious Interview, which use job-related decoys to infect targets. These operations have previously employed other malware strains like RustBucket and KANDYKORN.
A notable incident involved a malicious PDF mimicking a job description for a VP role at a cryptocurrency exchange, which dropped RustBucket malware—a backdoor written in Rust capable of harvesting system information and maintaining persistence as a fake "Safari Update."
Beyond social engineering, these threat actors have engaged in software supply chain attacks targeting entities like 3CX and JumpCloud. Once a foothold is established, they exploit password managers to steal credentials, conduct internal reconnaissance, and access cloud-hosted environments to exfiltrate crypto funds.
The FBI recently warned about North Korea's sophisticated social engineering campaigns targeting the cryptocurrency industry. These campaigns often involve impersonating known entities and extensive pre-operational research to craft personalized and credible scenarios that lure victims.
Numerous unsolicited messages, pretending to represent LinkedIn and others, are received by targets over apps such as WhatsApp in various countries worldwide.
In June, the FBI issued a warning about scammers promoting fake work-from-home jobs. The scammers pose as legitimate businesses, such as recruiting agencies, and usually contact victims via unsolicited calls or messages inviting them to rate restaurants or repeatedly click a button in exchange for attractive remuneration.