North Korean APT-C-28 Launches Sophisticated RokRat Fileless Malware Campaign
- A North Korea-aligned threat actor shows a change in tactics, adopting an improved RokRat strain.
- APT37 mainly deploys malware used for persistent infiltration and data exfiltration.
- The 2024 RokRat version adds enhanced anti-forensics, dynamic payload retrieval, and process hollowing.
A new cyber espionage campaign linked to the North Korean threat group APT-C-28, also known as ScarCruft or APT37, leverages fileless RokRat malware to target government personnel and corporations in South Korea and across Asia.
This spear-phishing email campaign containing malicious files impersonating government entities marks a notable evolution in the group’s tactics, according to a 360 Advanced Threat Research Institute security report.
Active since 2012, APT-C-28 specializes in targeting strategic industries such as aerospace, chemicals, and healthcare. Central to their operations is RokRat, a malware used for persistent infiltration and data exfiltration.
While previous versions of RokRat relied on cloud services for payload delivery, the latest iteration takes a different approach.
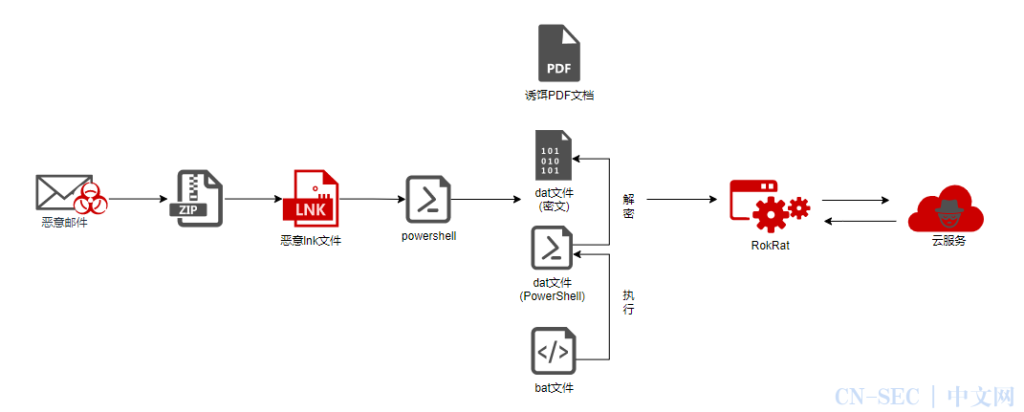
The group now embeds encrypted Shellcode within malicious LNK (shortcut) files attached to phishing emails. This fileless delivery method significantly reduces reliance on external servers, improving the malware's ability to evade detection by modern security defenses.
APT-C-28’s phishing campaigns are highly tailored, using legitimate-looking emails to lure targets. These emails often imitate credible sources, such as government memos or diplomatic policy documents.
Attached ZIP files containing malicious LNK files are disguised as relevant documents related to North Korean affairs. When a recipient opens the LNK file, a multi-stage attack is triggered.
The LNK file runs a PowerShell script, extracting various components, including decoy documents and encrypted RokRat shellcode, and a second PowerShell script uses XOR decryption to reveal the RokRat shellcode in memory, avoiding any disk activity.
The decrypted RokRat payload establishes a command-and-control (C2) connection using Googlebot user agent disguises to mimic legitimate network traffic.
The 2024 version of RokRat introduces several advancements in attack paths and strategies. New cleanup scripts remove registry keys, startup entries, and batch files more comprehensively, and modular commands enable attackers to fetch additional payloads dynamically during operations.
This campaign appears to align with North Korea’s ongoing intelligence-gathering efforts amid diplomatic tensions. Last year, the APT43 hacking group targeted German missiles and ammunition producer Diehl Defence.