Nokia Report Reveals Android Phones Are More Prone to Malware Infections Than iPhones
- Nokia issued an insightful report on the malware infection trends of 2018, and how they compare to the past.
- Android tops as the most insecure platform out there, with cybercriminals targeting it ferociously now.
- Apple’s iOS is the least infected platform, partly due to its closed source nature and small userbase.
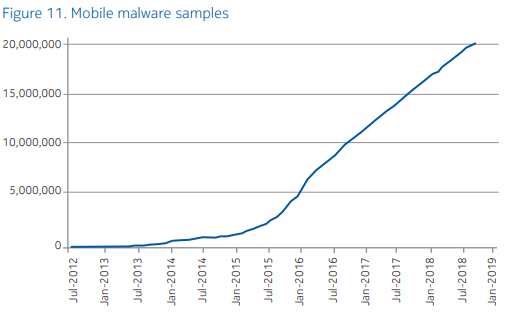
Nokia’s 2019 threat intelligence report is out, containing several interesting findings that reflect the current situation of malware propagation and infection in the world of mobile software. The white paper highlights rapid growth in IoT botnet attacks, increasing by 3.5% compared to last year, and accounting for an impressive 78% of the total malware network activity that was detected. As for the findings that concern the OSes, Android was deemed as the most vulnerable to malware infections, taking the 47.15% of the allotment, Windows PCs coming second with 35.82%, IoT devices placed third with 16.17%, and finally iOS accounting for less than 1% of the total share.
This comes as yet another affirmation of Apple’s claims on superior security, and as Nokia is currently a close collaborator with Google and an active participant of the Android One program, their report does not support their position. However, the underlying factors of the much larger market share that Android enjoys against iOS, as well as the fact that it is open source and frequently modified by smartphone manufacturers is making it a more lucrative target and often an easier one. The top position in the table of infections is occupied by a new malware named “Android.Adware.AdultSwine”, so ad-pushing and click-frauds remain the primary issue.
From the Nokia white paper
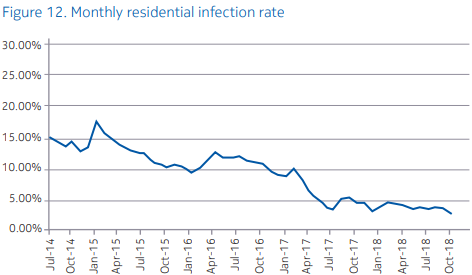
PCs are seemingly better protected nowadays, as the infection rates steadily drop since 2014. Nokia attributes this to new and advanced firewall features that are built into consumer routers, the much more robust operation systems of today, and the shifting of the cybercriminals focus to other platforms that are easier to exploit, and can potentially yield more profit. Nokia reports that according to their observations and data analysis, each home has a chance of approximately 3.88% of getting infected by malware over the period of a month.
From the Nokia white paper
Coin mining is another emerging category of malicious exploitation, and according to Nokia’s findings, miners have found ways to infect smartphones and even browser users with simplified mining algorithms that make them money often without the victim even realizing it. Crypto-miners are putting their malware to run on the infected devices, so they are taking up resources that can make a browser or a smartphone run slower than usual and have its battery drained faster. This can draw the attention of the suspicious user, so a trend to target IoT devices instead has also grown. This makes smart TVs, set-top boxes, and AI devices an ideal target, as it will take their owners even longer to realize that someone is remotely eating up their resources.
To extenuate a bit, not all of their findings, however, were negative, as their report on the Spectre/Meltdown vulnerabilities indicates that there have been no incidents that demonstrate any leveraging of these long-standing CPU security holes. This is seen as a success for all the patching that took place in 2018, but as we have analyzed in a previous post, we cannot be flaccid with these vulnerabilities as we head into 2019.
How do you see the above report and its findings? Let us know in the comments below, and feel free to like and share this story by visiting our socials on Facebook and Twitter.