Nissan Server Misconfiguration Leads to Source Code Leak
- Nissan has leaked a rich set of its own source code due to a configuration mistake.
- Someone has copied the data and shared it with a researcher who hosts leaked data.
- The incident is bound to bring a lasting headache for Nissan, opening the door to multiple problems.
The North American department of Nissan has blundered hugely by leaving a Git server exposed online while using default access credentials (admin/admin). Someone figured it out and downloaded the entire collection of its contents, totaling 20GB of software source code for Nissan’s diagnostic tools and mobile apps, the ‘NissanConnect’ services, as well as data relevant to client acquisition and market research.
As soon as researcher Tillie Kottmann published the copied data on his own special “leaked source code” repository, Nissan secured their server, but it was already too late.
Here’s the full list of what has been exposed and which is freely shared with anyone interested right now:
- Source for the Nissan NA Mobile apps
- Source for some parts of the ASIST diagnostics tool
- Source for the Dealer Business Systems / Dealer Portal
- Source for Nissan internal core mobile library
- Source for Nissan/Infiniti NCAR/ICAR services
- Source for client acquisition and retention tools
- Source for sale/market research tools + data
- Source for various marketing tools
- Source for the vehicle logistics portal
- Source for vehicle connected services / NissanConnect things
- Source for various other backends and internal tools
The incident creates a host of serious problems for Nissan, like having its tools copied by competitors or smaller companies who won’t have to invest in the development of their own, equally good solutions.
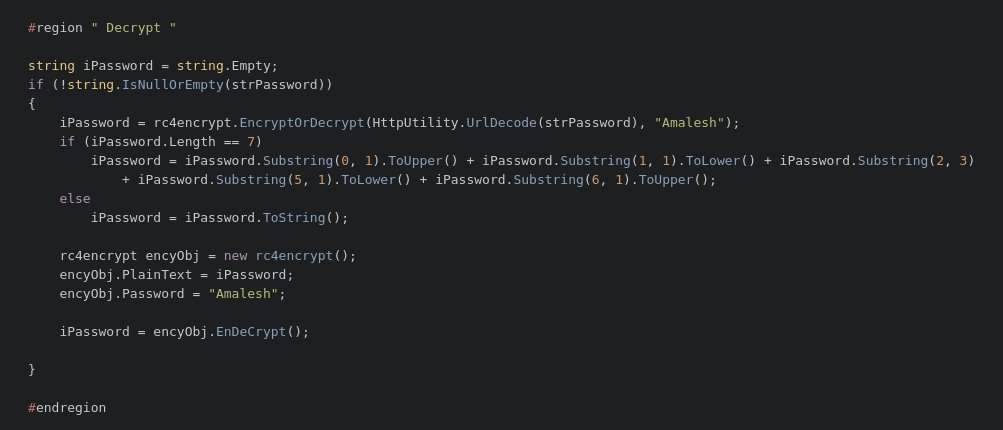
Additionally, source code leaks reveal the way things work, oftentimes helping hackers figure out ways to crack into software tools or systems. An example given by T. Kottmann is the part that shows how the password is handled by the ASIST diagnostics tool.
For automakers, locked down diagnostics is a way to ensure that clients are visiting authorized dealers for their car’s service. If technicians can use ASIST clones sold at a fraction of the real thing’s cost, Nissan will face problems extending on multiple levels.
If you’re interested in the above, T. Kottmann has set up a Telegram channel where you may find the download links to the leaked data. Beware that these are shared for research purposes or for satisfying curiosity if you prefer. Copying proprietary code could incur legal charges, as this code is still considered the intellectual property of Nissan released under the proprietary license.