Newly Unearthed APT Group “XDSpy” Has Been Around Since 2011
- ESET discovered a novel APT group that has been carefully operating for the past nine years.
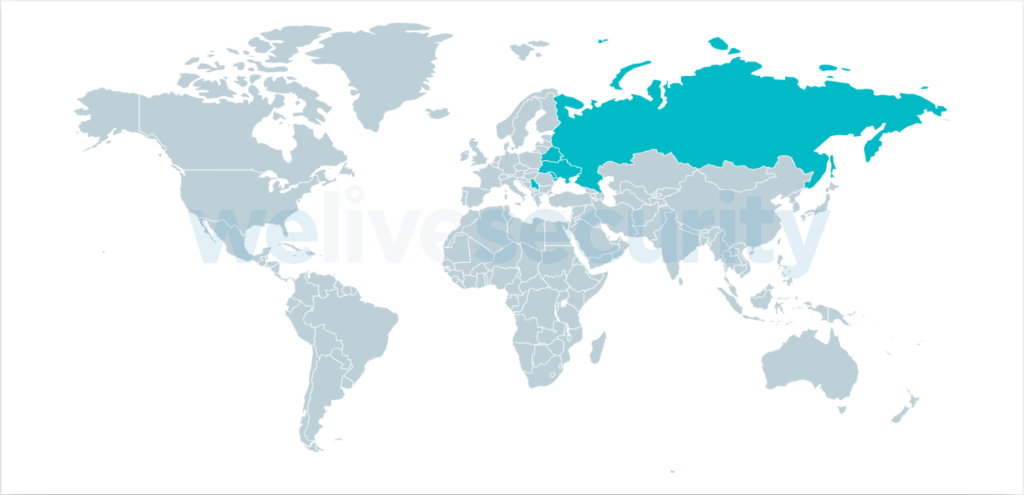
- The group called “XDSpy” is targeting Easter European countries and their governments in particular.
- The attack vector involves spear-phishing messages and the exploitation of new vulnerabilities.
ESET researchers have uncovered a previously unknown APT group that was stealing and selling highly sensitive data from Easter European governments for the past decade. Named “XDSpy,” this group managed to fly under the radar since 2011 and was mentioned for the first time in February 2020 in an announcement by the Belarusian National Response Center.
As ESET explains now, XDSpy wasn’t limited to spying Belarusian ministries but also several countries in the area such as Russia, Ukraine, Moldova, and Serbia.
The team that analyzed the details of the activity of the XDSpy concluded that it’s a new group since there are no code similarities with other known malware families, there are no overlaps with malicious network infrastructure, and the targets are somewhat unusual.
Also, considering that XDSpy has been around for nine years now, researchers would have already discovered it if there was a link with anyone else.
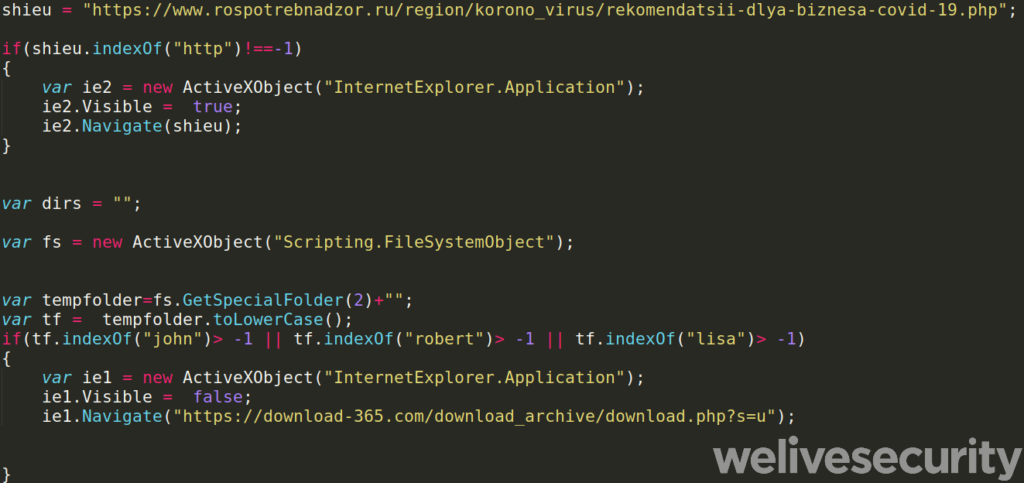
The hackers work Monday to Friday in time zones that match those of their targets, so there is a professional approach to their campaigns. Their ways mainly involve spearphishing emails that come with malicious ZIP and RAR attachments, so the only thing that changes is the theme and the targeted vulnerabilities. ESET confirmed exploits of CVE-2020-0968 being distributed from June 2020 and onwards, targeting systems with specially crafted HTML files.
Notably, this vulnerability was patched by Microsoft in April 2020, so the exploit's development came in a very short period. This indicates that XDSpy is a group of very capable hackers, or that they bought the exploit from a broker. In fact, ESET mentions that XDSpy could be using the same broker as DarkHotel, as some signs are pointing to this assumption.
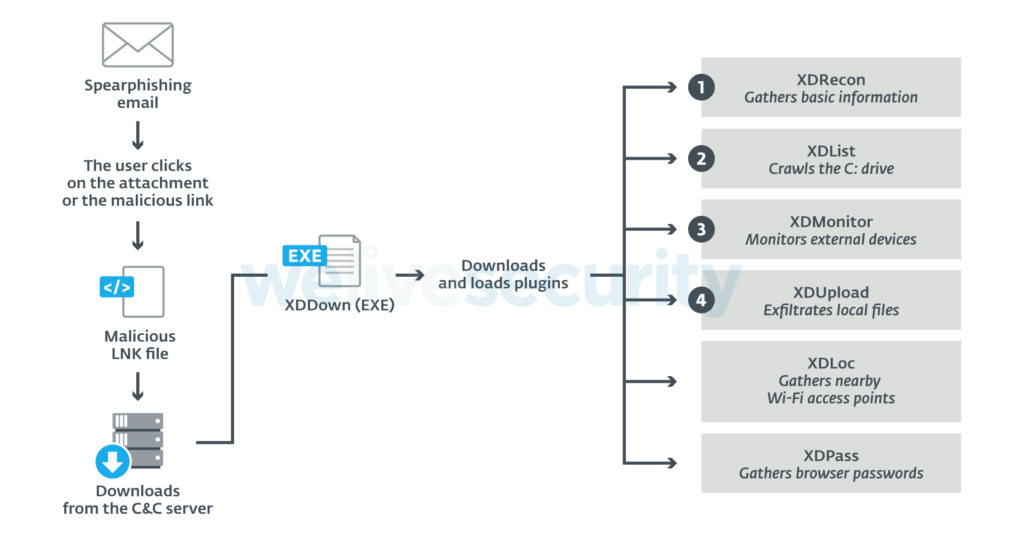
As for what the malware can do once it's dropped on the target system, that would depend on what plugins are fetched and loaded. The researchers have recorded six individual plugins which can do the following:
- XDRecon – gather basic system information
- XDList – crawl the C: drive
- XDMonitor – monitor external devices
- XDUpload – exfiltrate local files
- XDLoc – gather Wi-Fi access points in range
- XDPass – gather passwords stored in the browser cache
The activity of XDSpy has reached new levels during the past few months, and maybe this is what blew their cover after all these years. Now that the compromise indicators are known and publicly available, the APT group will have to prove how flexible and capable they are, as they have sent mixed messages on that part.