Newly-Discovered Glove Stealer Malware Bypasses Chrome’s App-Bound Encryption to Steal Cookies
- Glove Stealer is a freshly-found infostealer focusing on exfiltrating cookies from Firefox and Chromium-based browsers.
- Its main capability is bypassing Google Chrome’s Application-Bound encryption.
- The campaign’s social engineering techniques overlap with the recent ClickFix variant infection.
The new Glove Stealer malware can bypass Google Chrome’s Application-Bound (App-Bound) encryption to steal browser cookies. Glove Stealer targets cookies from Firefox and Chromium-based browsers, including Chrome, Edge, Brave, Yandex, and Opera.
Recently identified by security researchers from Gen Digital during an investigation into a phishing campaign, the Glove Stealer is described as “relatively simple” with minimal obfuscation, indicating an early developmental stage.
The malware employs social engineering techniques – which security researchers said are similar to the ClickFix infection – to deceive victims into executing malicious payloads through fake error messages embedded in HTML email attachments.
Its impact goes beyond cookie theft, extending to the exfiltration of cryptocurrency wallets, 2FA session tokens from services like Google and Microsoft, and password data from password managers such as Bitwarden, LastPass, and KeePass.
Furthermore, it is capable of extracting sensitive information from a broad array of 280 browser extensions and over 80 locally installed applications, many of which involve cryptocurrency wallets and 2FA authenticators.
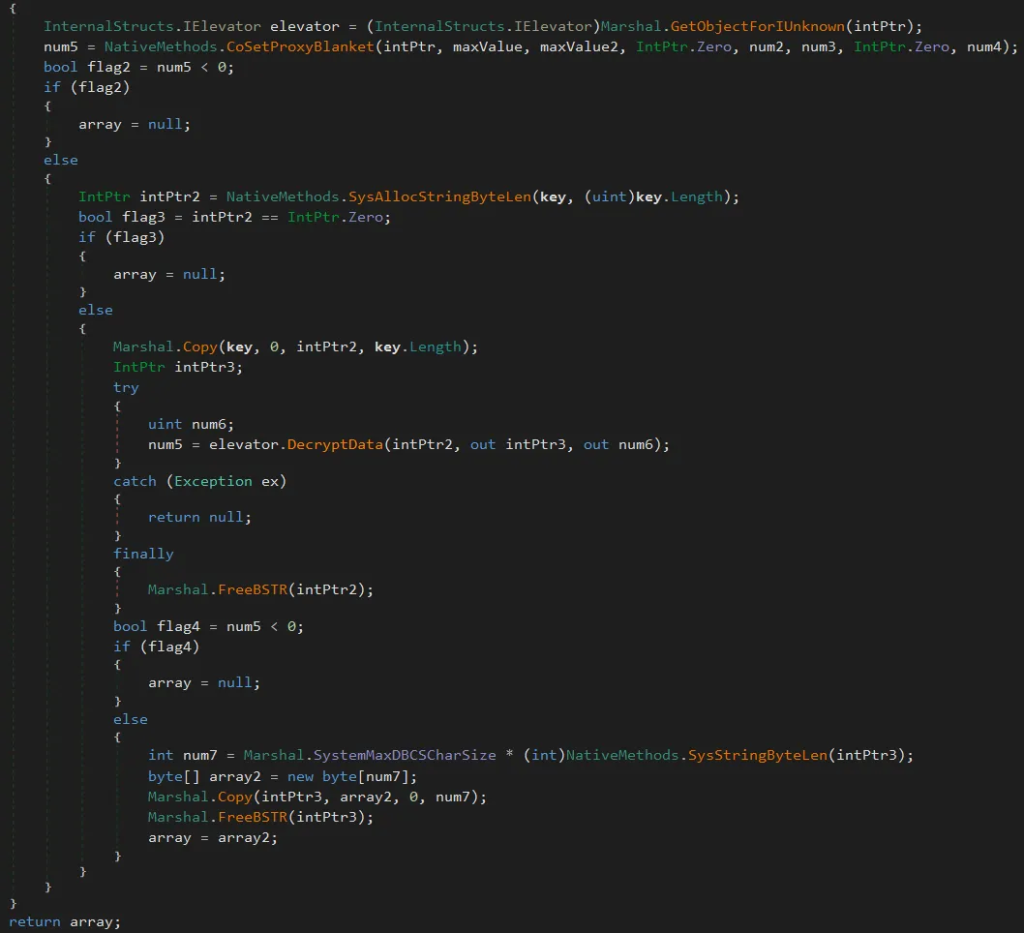
The mechanism used by Glove Stealer to defeat Google’s App-Bound encryption involves leveraging Chrome’s COM-based IElevator Windows service to decrypt and recover App-Bound encrypted keys. This requires the malware to first gain local admin privileges on a compromised system, positioning a supporting module within Chrome's Program Files directory for key retrieval.
Despite its innovative approach, Glove Stealer seems to be in its nascent phase, as its methods are akin to earlier tactics employed by other infostealers that have since evolved to more sophisticated means of bypassing Chrome’s security enhancements.
While Google's App-Bound encryption initiative was designed to elevate access barriers required for such attacks, the frequency of info-stealing malware incidents has not declined. Instead, these attacks have proliferated, exploiting vulnerabilities through various vectors, including zero-day exploits, malvertising, spearphishing, and deceptive internet forums.
Recently, cybersecurity researcher Alexander Hagenah created a public tool that bypasses Google Chrome's latest cookie encryption system, called “Chrome App Bound Encryption Decryption.” It enables the extraction of saved credentials from the Chrome browser, posing potential security risks for users who rely on Chrome for storing sensitive data.