Newly Discovered APT Group “LazyScripter” Was Actively Spreading Malware Since 2018
- There’s a new APT group targeting job seekers in Canada and also IATA employees and airlines.
- The group relies heavily on spamming campaigns and has been engaged in that space since 2018.
- The actors are using a wide range of RATs, commodity malware, and open-source tools.
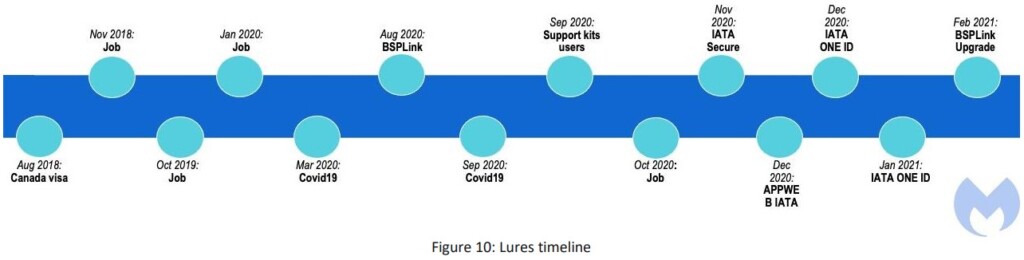
Malwarebytes researchers discovered a targeted spam campaign that dates as far back as 2018 and continues to this day by simply updating its lures. Although the observed TTPs have common ground with other known malicious groups such as APT28 and “Muddy Water,” this actor dubbed “LazyScripter” is considered a separate and so far undiscovered actor.
The phishing campaigns launched by the particular actor target job seekers with Remote Access Trojans (RATs) like Octopus, Koadic, LuminosityLink, RMS, Quasar, njRat, and Remcos. The targets seem to be people looking to immigrate to Canada. However, there are also lures specifically designed to imitate IATA (International Air Transport Association) and exploit the introduction of the IATA ONE ID contactless passenger processing tool. Thus, airlines and their employees are also targeted by LazyScripter.
According to what Malwarebytes was able to gather, the phishing lures have the following subjects:
- IATA security (International Air Transport Association security)
- BSP link Updater or Upgrade (BSPlink is the global interface for travel agents and airlines to access the IATA Billing and Settlement Plan (BSP).
- IATA ONE ID
- User support kits for IATA users
- Tourism (UNWTO)
- COVID-19
- Microsoft Updates
- Job information
- Canada skill worker program
- Canada Visa (CanadaVisa.com is the online presence of the Campbell Cohen Immigration Law Firm)
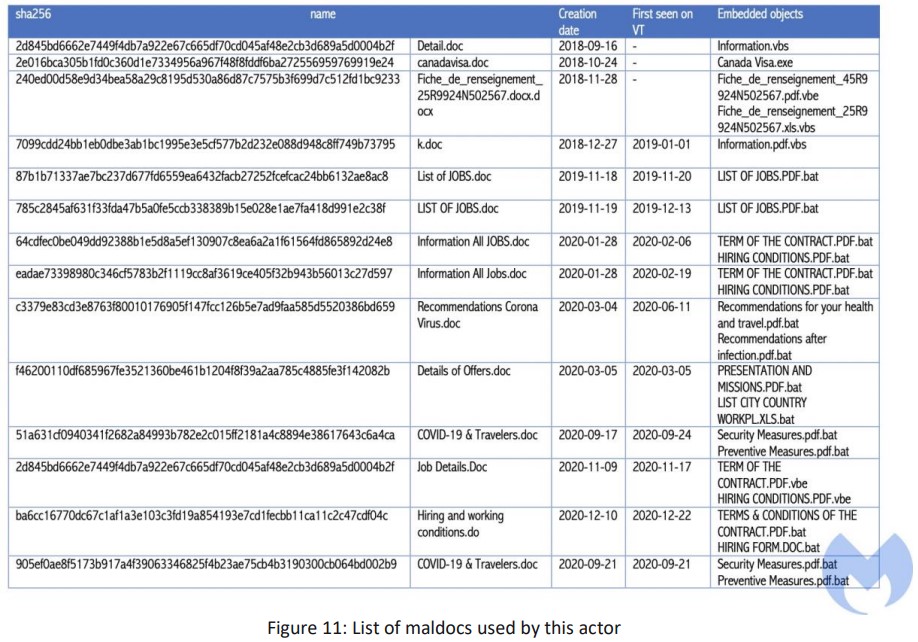
To tap onto the relevant victim pool, LazyScripter targets government-supported job finding programs hosted on Canadavisa.com and other legitimate sites. Their main infection vector is emails that carry malicious ZIP and document files hosted on GitHub. In most cases, these ZIPs contain either KOCTOPUS or Koadic, posing as “Upgrade.exe” or “IATA ONE ID.exe.”
KOCTOPUS has four different variants with different backdoor functionality, executables, VBScript, or registry keys. The group generally uses a galore of different RATs to maintain an unusually diverse set of information-exfiltration methods.
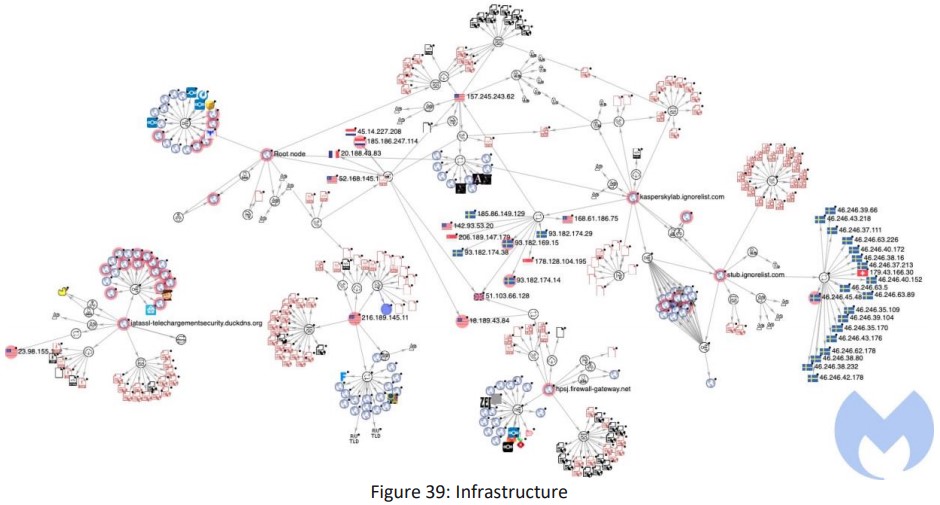
All of them use the same C2 infrastructure, which is pretty extensive too. Still, Malwarebytes was able to identify the following five subdomains relying on four different dynamic DNS domain generating providers:
- kasperskylab.ignorelist.com
- hpsj.firewall-gateway.net
- googlechromeupdater.twilightparadox.com
- iatassl-telechargementsecurity.duckdns.org
- stub.ignorelist.com
The main things that pushed Malwarebytes to consider that this actor is a new group include the facts that they rely almost solely on spam campaigns, uses a very wide range of RATs and commodity tools, uses direct embedding instead of macros, and doesn’t use custom toolsets that are linked to other similar groups.