New Threat ‘SquirrelWaffle’ Deploys Qakbot and Cobalt Strike Through Malspam
- A new malware threat called SquirrelWaffle was discovered in malspam campaigns more and more frequently.
- It deploys a new malware loader to infect victims, and the malware packages use compromised MSWord and Excel documents for the device infection.
- The actors are using already compromised web servers and Qakbot with Cobalt Strike.
SquirrelWaffle, a recently recognized cyberthreat, has been seen deployed in malspam campaigns on a wider range of targets than before. After setting in, this threat uses other malware to further infiltrate and compromise other systems or for additional infections. Among the most important malware part of SquirrelWaffle are Qakbot and the pen-testing software Cobalt Strike.
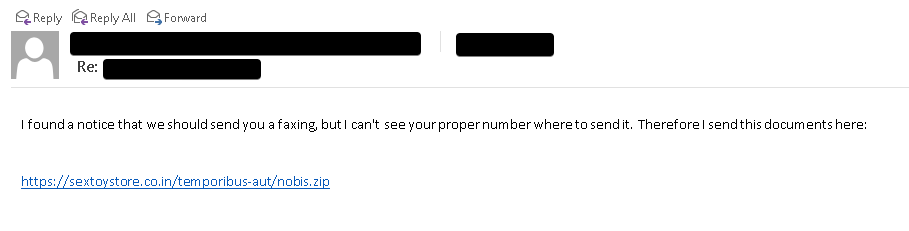
The Cisco Talos Intelligence team discovered that the threat uses malicious spam emails to deliver compromised Microsoft Word and Excel documents that help execute the payload. These emails are primarily in English but can sometimes also be in other languages like French, German, Dutch, and Polish. Any clicks lead users to download ZIP files containing the aforementioned malicious documents.
The documents themselves can have falsified validators like DocuSign (which is often used in professional documentation) and contain the entire SquirrelWaffle infection initiator, which is executed to retrieve the actual SquirrelWaffle payload off one of three to five hardcoded URLs and run the malicious DLL via rundll32.exe. The same process initiates on the MSExcel docs, except for the DLL - here is executed via ShellExecuteA and regsvr32.exe. The payload also installs Qakbot and CobaltStrike while installing the malware data packet.
After executing the malicious script, attackers can remotely command the malware set to gain remote access via a command and control (C2) server. These communications are usually masked with XOR and then Base64-encoded and contain user system configuration data. The attacker can retrieve said data with getenv, GetComputerNameW, GetUserNameW, and NetWkstaGetInfo()etc. The attacker can also use the C2 servers to deliver additional payloads to the compromised device.
According to researchers, the campaigns have started generating volume spamming since September 13, 2021. They are targeting WordPress content management systems (CMS) hosted on already compromised servers, with the most prevalently targeted version being WordPress 5.8.1.
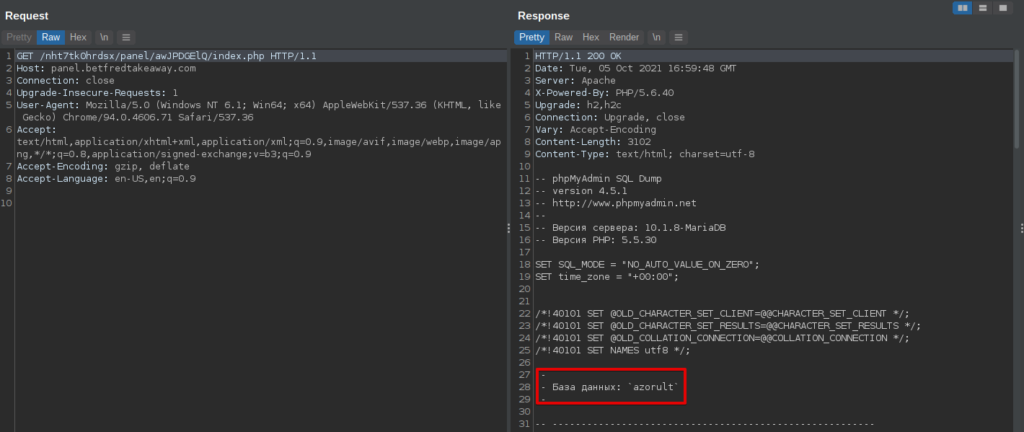
The researchers also found isolated instances of SQL dump linked with an Azorult panel at the same time with a SquirrelWaffle C2 host. Another instance showed servers with an ANTIBOT potentially deployed by rival spammers, a set of scripts generally used in phishing kits to help actors evade analysis.
It is also using IP address arrays along with blocklists to strengthen and obfuscate its malspam infrastructure. This may be done to prevent large-scale analysis and restrict access to malicious components via geographic-based filtering and other methods.
From what we can see in the research above, we can assume that SquirrelWaffle's malware family is successfully filling the void that Emotet left, and chances are it could become the next big spam player if it keeps it up.