New “SunCrypt” Ransomware Gang Joins the ‘Maze’ Cartel
- A new data-stealing ransomware strain has appeared, and it has already claimed five victims.
- The ransomware is called “SunCrypt,” and it has joined the Maze cartel to seek technical support.
- Maze remains a troubling mystery, and the source of tens of catastrophic infections daily.
The ‘Maze’ cartel that the notorious ransomware actors kicked off a couple of months back has a new member. A new group using a new ransomware strain called “SunCrypt” has come to light, and Maze was happy to welcome them under their umbrella. Although the cartel’s exact nature remains a mystery, it is believed that Maze supports other actors with specialist advice, infrastructure, resources, and even ransom cuts.
According to Bleeping Computer, who claims to have had direct communication with SunCrypt, the new group is independent of Maze, but they are in close cooperation. More specifically, SunCrypt will share some revenue with Maze in exchange for support in handling the volume of the field of operations.
Maze is a powerhouse in the field, and we get tens of infection alerts concerning the particular strain every day. That said, it is unquestionably strong in infrastructure, resources, and member count, so it’s in a position to help others as well.
source: Bleeping Computer
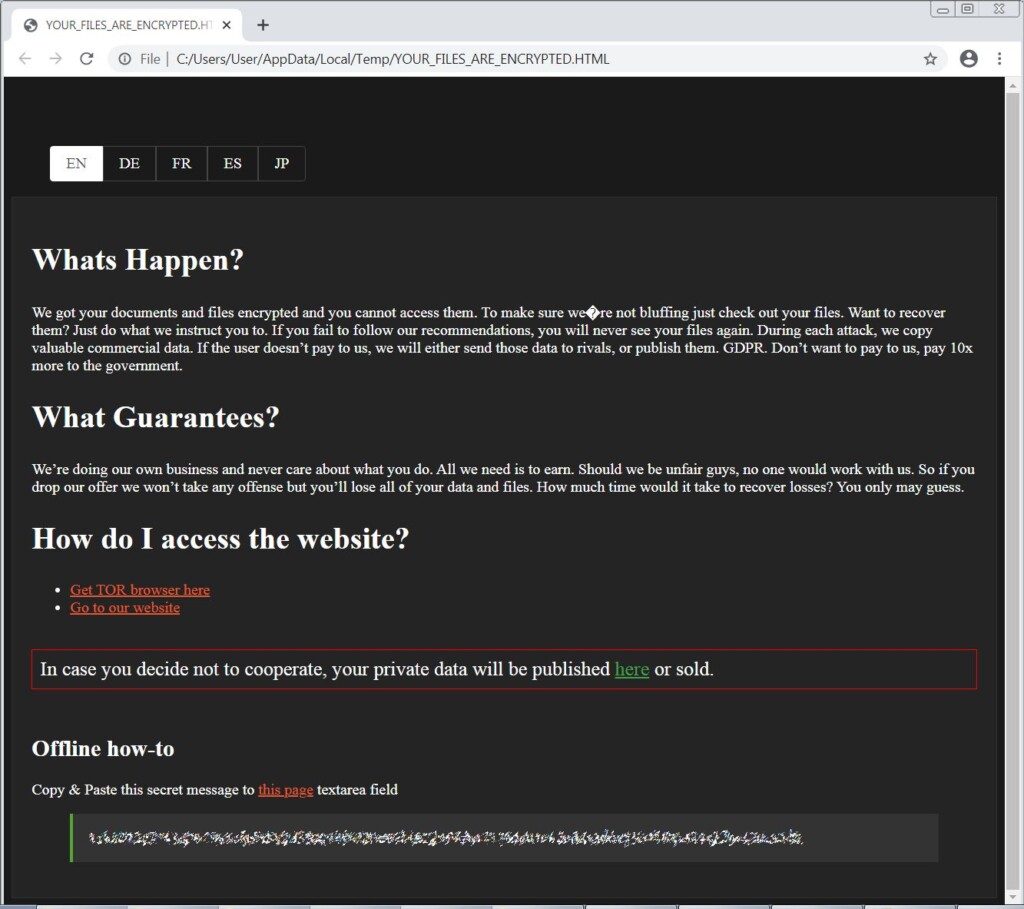
From a technical perspective, the SunCrypt ransomware comes in the form of a DLL, encrypting the files and appending a hexadecimal hash to each file name. The ransom note that is generated on every folder points the victim to a Tor payment site, with the link being common for all victims.
So far, SunCrypt has compromised at least five entities, as they have published samples of the stolen data on their leak portal.
🤔
SunCrypt pic.twitter.com/Rfh74gEFPB— Neutral8✗9eR @[email protected] (@0x009AD6_810) August 26, 2020
We have reached out to ransomware analysts to see if they have already found any weaknesses in the encryption scheme of the SunCrypt, and we will update this piece as soon as we hear back from them. Hopefully, the new ransomware won’t be at the level of Maze, but this is unlikely considering the diligent work that goes into the development of strains meant to target large organizations.
As for what the new membership revealed about the Maze cartel, besides the IP address that the SunCrypt points to upon execution, there’s not much else that can be deduced. Maybe the obfuscated PowerShell script that is responsible for the installation of the SunCrypt is also a tool that was kindly shared by Maze, but this doesn’t offer much either.
Finally, we know that Russian hackers operate Maze, so maybe SunCrypt are Russians too. This is just speculation at this point, but the more Maze opens up, the more information around the group will surface.
Read More:
- Big Steel Sheet Manufacturer Struck by Maze Ransomware
- Textile Cutting Expert ‘Lectra’ Struck by the Maze Ransomware Group
- “Cognizant” Is Circulating Notices of a Data Breach to the Affected Associates