New Snake Keylogger Variant Targets Windows Using AutoIt in Asia and Europe
- A novel strain of the Snake keylogger added deploying an AutoIt-compiled payload to its known data-stealing capabilities.
- The malware can exfiltrate stolen data while avoiding traditional detection mechanisms
- Hiding its payload in a legitimate-looking executable, making reverse engineering more difficult.
A newly evolved strain of the infamously malicious Snake Keylogger is actively targeting Windows users across Asia and Europe, exploiting the AutoIt scripting language to enhance its stealth and evade detection.
Snake Keylogger, first established as a Microsoft .NET-based data-stealing malware, has a well-documented history of siphoning passwords, credit card details, and browsing credentials by logging keystrokes, capturing screenshots, and monitoring clipboard actions.
The latest version takes this a step further by deploying an AutoIt-compiled payload. AutoIt, a BASIC-like freeware programming language used to automate Windows tasks, is becoming a favored tool for criminals, as its scripts can appear indistinguishable from legitimate automation tools.
According to Fortinet’s malware researchers, the malware arrives as a spam email attachment disguised as a legitimate file. Once opened, it executes in the background, stealing sensitive personal and business information.
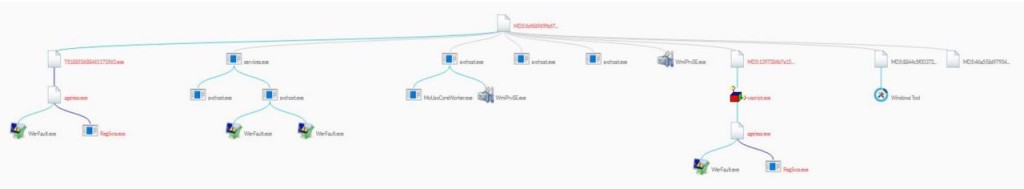
When executed, the Snake Keylogger embeds itself into the user’s system by copying its main file, named "ageless[.]exe", into the "%Local_AppData%\supergroup" directory, hiding its presence by setting the file attributes to "hidden."
It also creates a secondary script, "ageless[.]vbs", in the Windows Startup folder. This ensures the payload is executed every time the system reboots, maintaining persistence even when noticed and partially removed.
The malware injects itself into legitimate processes to avoid quick detection, particularly targeting "RegSvcs.exe" via process hollowing. This evasive technique prevents the legitimate process from loading its usual code and replaces it with malicious instructions.
Once fully active, Snake Keylogger uses the SetWindowsHookEx API to install keylogging hooks at a low level, effectively capturing input data like banking credentials and browser passwords without detection.
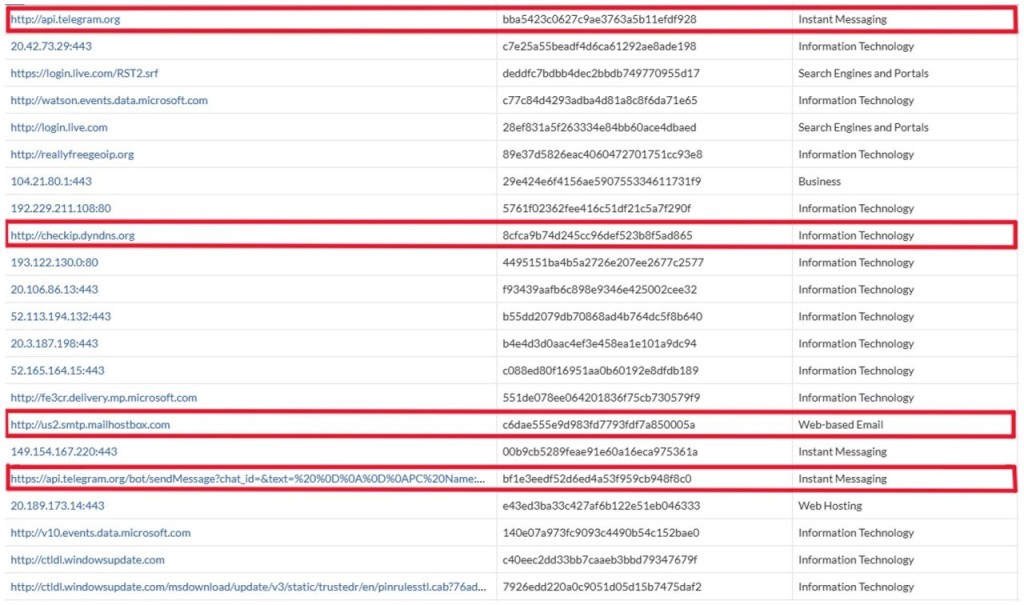
The stolen data is exfiltrated via several channels, including SMTP email services, Telegram bots, and HTTP POST requests to command-and-control servers. Additionally, the malware connects to "hxxp://checkip[.]dyndns[.]org" to retrieve the victim’s public IP address, aiding attackers with geolocation data.
The use of AutoIt is not coincidental. By wrapping its payload in a legitimate-looking executable, Snake Keylogger makes reverse engineering more complex.
Security experts highlight how AutoIt-generated scripts bridge the appearance of "benign" automation and malicious behavior to bypass traditional antivirus detection.