A New Set of ‘INFRA:HALT’ Vulnerabilities Is Coming for Your OT Devices
- A set of 14 critical flaws in the TCP/IP stack ‘NicheStack’ affects thousands of industrial devices around the world.
- Users are advised to patch their firmware immediately, but a fixing update is not available from every vendor.
- There are at least some partially effective mitigation strategies that should be followed by OT product admins.
Researchers at JFrog and Forescout, the team that discovered ‘Name:Wreck’, have now jointly uncovered a new set of flaws that affect roughly 6,400 currently-online OT and industrial devices from 200 vendors. The set contains 14 critical vulnerabilities with varying implications, all affecting the closed-source TCP/IP stack ‘NicheStack’. Unfortunately, this technical solution (which has been around for about 20 years) appears to be commonly deployed in industrial automation systems, so the impact is pretty wide.
Without further ado, the flaws are given below ranked by their criticality:
- CVE-2020-25928: RCE on DNSv4, CVSSv3.1 score – 9.8
- CVE-2021-31226: RCE on HTTP, CVSSv3.1 score – 9.1
- CVE-2020-25927: DoS on DNSv4, CVSSv3.1 score – 8.2
- CVE-2020-25767: DoS infoleak on DNSv4, CVSSv3.1 score – 7.5
- CVE-2021-31227: DoS on HTTP, CVSSv3.1 score – 7.5
- CVE-2021-31400: DoS on TCP, CVSSv3.1 score – 7.5
- CVE-2021-31401: App-dependent, TCP, CVSSv3.1 score – 7.5
- CVE-2020-35683: DoS on ICMP, CVSSv3.1 score – 7.5
- CVE-2020-35684: DoS on TCP, CVSSv3.1 score – 7.5
- CVE-2020-35685: TCP spoofing on TCP, CVSSv3.1 score – 7.5
- CVE-2021-27565: DoS on HTTP, CVSSv3.1 score – 7.5
- CVE-2021-36762: DoS on TFTP, CVSSv3.1 score – 7.5
- CVE-2020-25926: DNS cache poisoning on DNSv, CVSSv3.1 score – 4
- CVE-2021-31228: DNS cache poisoning on DNSv4, CVSSv3.1 score – 4
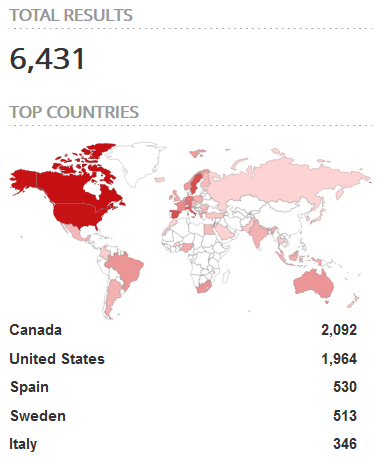
A search on Shodan has returned about 6,400 results, mostly from Canada and the United States, while Spain, Sweden, and Italy also appear to deploy a respectable number of vulnerable devices. As for the seconds where these are used, half of them are found in the otherwise crucial energy and power industry, one-fourth is in VoIP, and one-fifth in networking.
Addressing the set of the ‘INFRA:HALT’ flaws would be a matter of applying fixing patches on these devices, but patching OT products isn’t a simple process. Additionally, not every one of the 200 affected vendors has released fixing updates for their products. This leaves many users with the only option being mitigation.
Forescout is proposing the following steps to be taken for a complete mitigation strategy:
- Discover and inventory devices running NicheStack. Forescout Research Labs has released an open-source script that uses active fingerprinting to detect devices running NicheStack. The script is updated constantly with new signatures to follow the latest development of our research. Forescout has also released an updated Security Policy Template (SPT) for eyeSight to detect devices running the stack.
- Enforce segmentation controls and proper network hygiene to mitigate the risk from vulnerable devices. Restrict external communication paths and isolate or contain vulnerable devices in zones as a mitigating control if they cannot be patched or until they can be patched.
- Monitor progressive patches released by affected device vendors and devise a remediation plan for your vulnerable asset inventory balancing business risk and business continuity requirements.
- Monitor all network traffic for malicious packets that try to exploit known vulnerabilities or possible 0-days. Anomalous and malformed traffic should be blocked, or at least alert its presence to network operators. Forescout has released a script for eyeInspect that detects exploitation attempts against the vulnerabilities in INFRA:HALT
- Disable the DNSv4 client if not needed, or block DNSv4 traffic. Because there are several vulnerabilities that facilitate DNS spoofing attacks, using internal DNS servers may be not sufficient (attackers may be able to hijack the request-response matching).
- Disable HTTP if not needed, or whitelist HTTP connections.
- For CVE-2021-31400, CVE-2021-31401, and CVE-2020-35684, monitor traffic for malformed IPv4/TCP packets and block them. E.g., having a vulnerable device behind a properly configured firewall should be sufficient. For CVE-2020-35685, we suggest using recommendations we outlined in our NUMBER:JACK report, whenever it is feasible.
- Monitor traffic for malformed ICPMv4 packets and block them.