New Russian Hacktivist Group Emerges, Targets US Critical Infrastructure
- Sector 16 is the latest emerging hacktivist group observed by security researchers last month.
- The gang was identified as having Russian roots and leaning toward U.S. infrastructure targets.
- In January, approximately 40% of cybercrime cases concern ransomware, with 15 groups selling or claiming data breaches.
A new Russian hacktivist group, dubbed "Sector 16," was identified during an analysis of dark web activities in January 2025. The security report covered over 250 dark web claims and revealed a significant rise in threats targeting U.S.-based organizations.
Ransomware group activity dominated Cyble cybersecurity researchers’ investigations, accounting for approximately 40% of cases, with 15 ransomware groups either claiming successful attacks or offering stolen data for sale.
Additionally, threats ranged from ransomware incidents to unauthorized network access trades, phishing services, and emerging alliances among hacktivist groups.
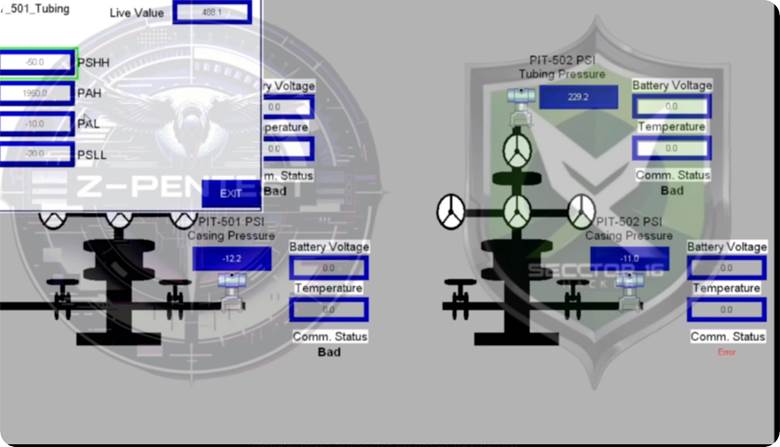
Sector 16, a newly surfaced threat group, joined forces with Russian hacktivists Z-Pentest in an attack on a Supervisory Control and Data Acquisition (SCADA) system responsible for managing oil pumps and storage tanks in Texas.
The groups shared a video showcasing the compromised SCADA system interface, displaying real-time operational data such as tank levels, pump pressures, and alarm management features.
Both Sector 16 and Z-Pentest branded the video with their respective logos, hinting at a deep collaboration between the groups. This partnership underscores Sector 16's emergence as a significant player among Russian hacktivist circles.
Sector 16 also claimed unauthorized access to a U.S. oil and gas production facility's control systems. Following this breach, the group released a second video displaying critical operational data, including shutdown management, tank level readings, gas lift operations, and valve control interfaces.
Hacktivist activity during January also included pro-Islamic groups such as Mr. Hamza, who partnered with Z-Pentest and Velvet Team for a series of Distributed Denial-of-Service (DDoS) attacks targeting U.S. military and government systems.
Notable targets included the U.S. Army’s development and communications network, an FBI portal related to bank robbery data, and the official platform for the United States Africa Command.
The January activity appears to reflect a growing trend among Russian-aligned hacktivist groups seeking to demonstrate their capabilities by targeting U.S. entities. Despite their focus on tampering with infrastructure and assembling high-profile alliances, many of these attacks have yet to prove impactful beyond showcasing access to critical systems.
Ransomware continues to dominate the cybersecurity threat landscape, from vulnerabilities in enterprise software to criminal actors selling stolen data. Cyble identified 15 ransomware groups active in January: CL0P, LockBit, INC, Lynx, Rhysida, SafePay, RansomHub, Monti, Qilin, BianLian, Medusa, Cactus, BlackBasta, FOG, and Akira.
CL0P emerged as particularly prolific, with campaigns exploiting Cleo MFT vulnerabilities, claiming over 115 victims. The targeted sectors included healthcare providers, academic institutions, transportation services, defense contractors, and government agencies.
Cyble’s report revealed multiple instances of repeat victimization, with ransomware actors targeting entities previously encountering similar breaches.
The surge in data theft claims included various attacks revealed on the dark web. For instance, one threat actor advertised a SIM-swapping service targeting users of a U.S.-based telecommunications provider, suggesting insider access or exploitation of an internal portal.
Other breaches involved unauthorized admin access to a U.S. government website, root access to a logistics company, and stolen data from an IT company that included source code, private certificates, and Docker builds.
One notable case involved a threat actor selling unauthorized access to a subdomain of a retail corporation’s network for $16,000. The actor alleged that this access could lead to illicit command execution on the organization’s servers, illustrating the potential scale of such breaches.