New Russian APT Spear-Phishing WhatsApp Campaign Impersonates US Officials
- The Star Blizzard/Callisto group impersonated U.S. government representatives in emails containing malicious QR codes and short links.
- The Russian-aligned hackers used Ukraine NGO aid via a WhatsApp group as a lure and exploited WhatsApp’s authentication process.
- Attackers accessed the victim’s WhatsApp messages and exfiltrated message data directly from the compromised account.
A major tactical shift in the spear-phishing activities of Star Blizzard, a Russian-aligned threat actor, was seen in a new campaign targeting WhatsApp accounts of high-profile individuals, Microsoft Threat Intelligence said in a recent report.
Targeting WhatsApp for the first time, Star Blizzard’s (formerly known as SEABORGIUM, also known as Callisto Group/TA446/ColdRiver/TAG-53/BlueCharlie) campaign strategy remains rooted in familiar spear-phishing practices but added US officials impersonation, malicious QR codes, and shortened links.
The campaign begins with emails designed to impersonate a U.S. government official, leveraging the credibility of prominent figures to enhance engagement.
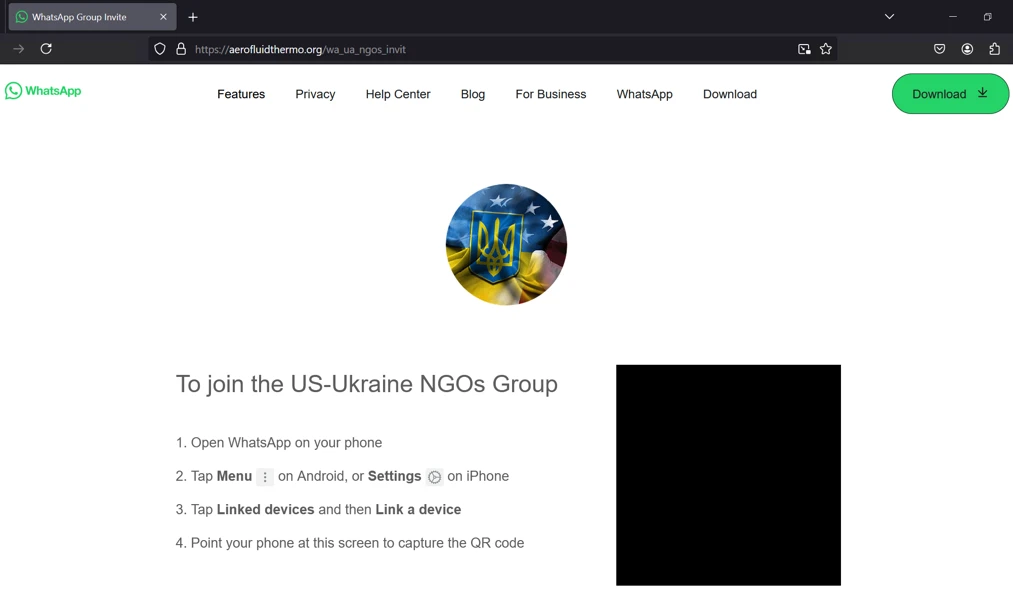
Initial emails contain QR codes claiming to provide access to a WhatsApp group focused on “supporting Ukraine NGOs.” The QR code is deliberately broken to prompt recipients to engage with the sender.
Once the target responds, a second email is sent with a Safe Links-wrapped, t[.]ly shortened link. Clicking the link redirects the victim to a malicious webpage designed to exploit WhatsApp’s authentication process.
Upon navigating to the redirected page, victims are prompted to scan a QR code to supposedly join the WhatsApp group. However, this QR code controls WhatsApp Web connectivity, granting the attacker access to the victim’s WhatsApp messages.
Using browser plugins, Star Blizzard can exfiltrate message data directly from the compromised account.
This development reveals a significant departure from Star Blizzard's established tactics, techniques, and procedures (TTPs), which adapted to protective measures.
Historically, Star Blizzard’s campaigns have predominantly targeted individuals and entities involved in government affairs, diplomacy, defense policy, and international relations as they relate to Russia.
Additionally, the actor has pursued sources providing help to Ukraine in the ongoing war with Russia. Between January 2023 and August 2024, the group actively targeted civil society organizations, including journalists, think tanks, and NGOs, aiming to exfiltrate sensitive data and disrupt operational activities.
Microsoft and the US Department of Justice seized 180 associated websites of Star Blizzard’s infrastructure, temporarily affecting their operations in October 2024. However, the group quickly transitioned to new domains to maintain continuity.
In June 2024, the Council of the European Union (EU) sanctioned six hackers, including Ruslan Peretyatko and Andrey Korinets, believed to be Russian military intelligence officers who are part of this advanced persistent threat (APT).
A recent phishing campaign was deployed by hackers impersonating Amazon, who used Google Drawings and WhatsApp shortened URLs. Users’ details were then stolen via a malicious domain that requested sensitive personal data, including banking details.