New Ransomware Ymir Discovered in the Wild Using RustyStealer
- Security researchers identified a new ransomware family they named Ymir, which displays robust stealthy capabilities.
- Deploying RustyStealer allowed the attackers to control the compromised machines, send commands, and harvest data.
- The initial RustyStealer sample was a Rust-compiled PE file deployed to Temp.
Cybercriminals are currently utilizing a new and noteworthy ransomware family named Ymir. This sophisticated malware is distinguished by its stealthy capabilities, enabling it to evade detection through advanced memory operations facilitated by API calls, according to the latest report from the Kaspersky cybersecurity team.
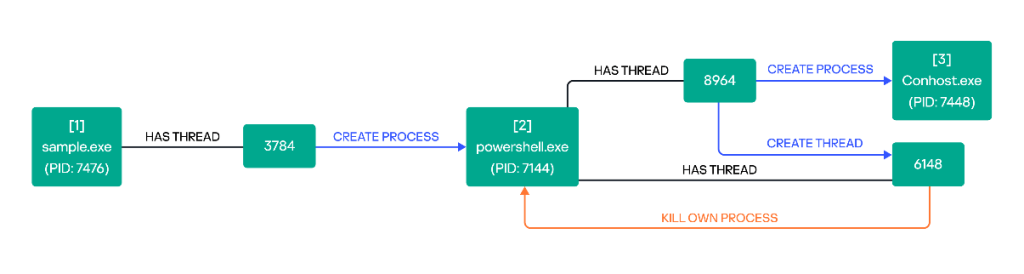
The initial breach occurred via PowerShell remote control commands, allowing attackers to gain unauthorized access to the system. Subsequently, they deployed tools such as Process Hacker and Advanced IP Scanner to disable security measures. With reduced defenses, the attackers executed Ymir to fulfill their malicious intent.
The examination began with an inspection of the artifact, including file properties, strings, and capabilities. Although the binary lacks high entropy, which typically signals packing, the presence of specific API calls, usually found in various ransomware samples, suggests its ability to allocate memory for malicious code insertion.
Significantly, the researchers identified key indicators within the binary strings, such as the ransom note filename, contents in a PDF file, encryption extension, PowerShell commands, and encryption algorithm hashes. Notably, the malware borrows code from the CryptoPP library, enhancing its cryptographic functions.
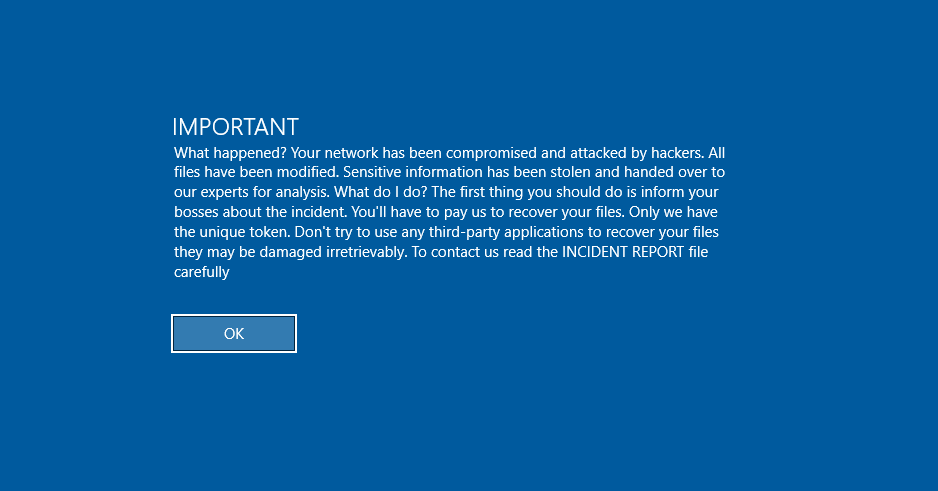
The ransom note within Ymir informs victims of the system compromise and instructs them to contact the attackers. Although it claims data theft, the absence of network exfiltration capabilities indicates that data would likely be extracted through other means post-access.
Days before deploying Ymir, a new threat named RustyStealer was detected, facilitating machine control and information gathering. Subsequent malicious activity on a domain controller included compromised access by legitimate users, one with elevated privileges.
This incident underscores a clear link between stealer botnets as access brokers and ransomware execution. Ymir's development exemplifies a potent threat to businesses, illustrating the emergence of groups capable of deploying configurable, robust malware.
Following the alerts triggered two days prior to the ransomware attack, the failure to act on critical system warnings underscores the necessity for enhanced response strategies beyond relying on endpoint protection platforms (EPP).
Kaspersky continues to monitor the Ymir threat diligently, having detected it as Trojan-Ransom.Win64.Ymir.gen. While the group behind this ransomware has not launched a dedicated leak site, their activities remain under surveillance to ensure preparedness against future incidents.
In other news, RansomHub emerged as a dominant force, surpassing the former leader LockBit after a law enforcement crackdown on the latter.