New RaaS “SMAUG” Wants to Take All the Ransomware Treasure
- SMAUG is a new RaaS aiming to become the ruler of the ransomware scene, at least for a while.
- The project looks very professional and operates on a matching level, although still pretty young.
- SMAUG is already gaining traction, and as a ransomware strain, it is very effective and efficient.
A new ransomware as a service (RaaS) platform named “SMAUG,” which first appeared in April 2020, wants to dominate the field and render every other offering obsolete. Similarly to how Tolkien’s fictional dragon character “Smaug” was the greatest of his kind and sincerely interested in Erebor’s vast treasures.
So, if that is the goal, would the firepower of “SMAUG” be enough to justify these aspirations? A Sentinel Labs report is helping us answer that question.
First of all, SMAUG is open to everyone willing to join the platform, so it doesn’t operate in a confined context like other RaaS. Secondly, it’s a complete and robust service that doesn’t have downtimes or inconsistencies. Thirdly, the fee charged by the operators of the service is set to 20%, which is relatively low. There is a 0.2 BTC registration fee to enter the dragon’s realm, though, but this assures that only serious crooks will join.
Source: Sentinel Labs
Then there’s the actual technical aspect of the ransomware, which is pivotal, of course. SMAUG is very advanced, supporting a wide range of platforms, being able to infect multiple hosts with a single key (company mode), and can even work without an internet connection (offline mode).
The encryption process is based on an AES-256 scheme using an RSA-2048 public key. The encryption speed is another highlight of SMAUG, as the malware uses a multi-threaded code to encrypt the victim’s files quickly, minimizing reaction times.
In regards to AV detection evasion, SMAUG relies on obfuscation and crypting, while its payloads were developed with footprint minimization in mind. For now, SMAUG doesn’t come with a default packer, so its users are free to use whatever they prefer.
Source: Sentinel Labs
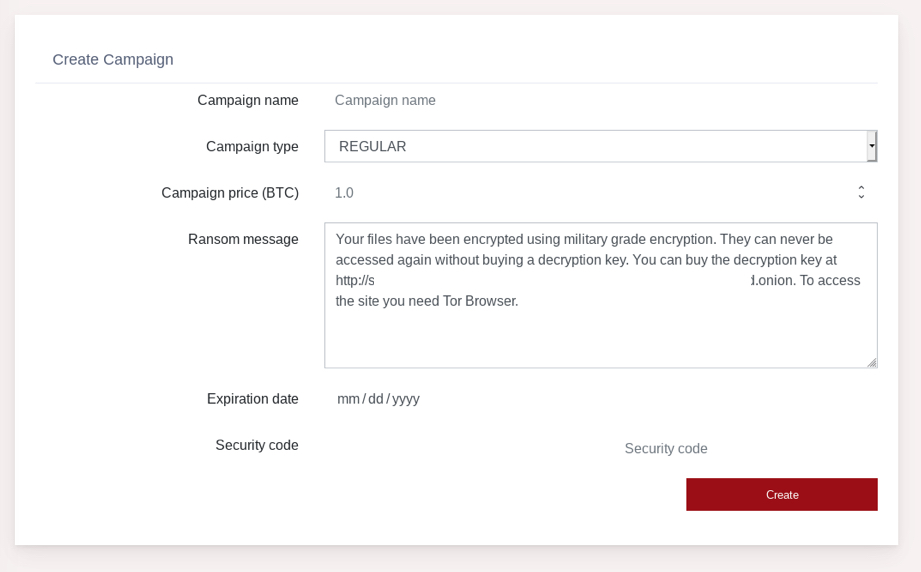
As for the payment process, there’s a fully automated system that can be customized by the user, so there are no fixed ransom amounts, standard messages, etc. This is another example that underlines the open nature of SMAUG.
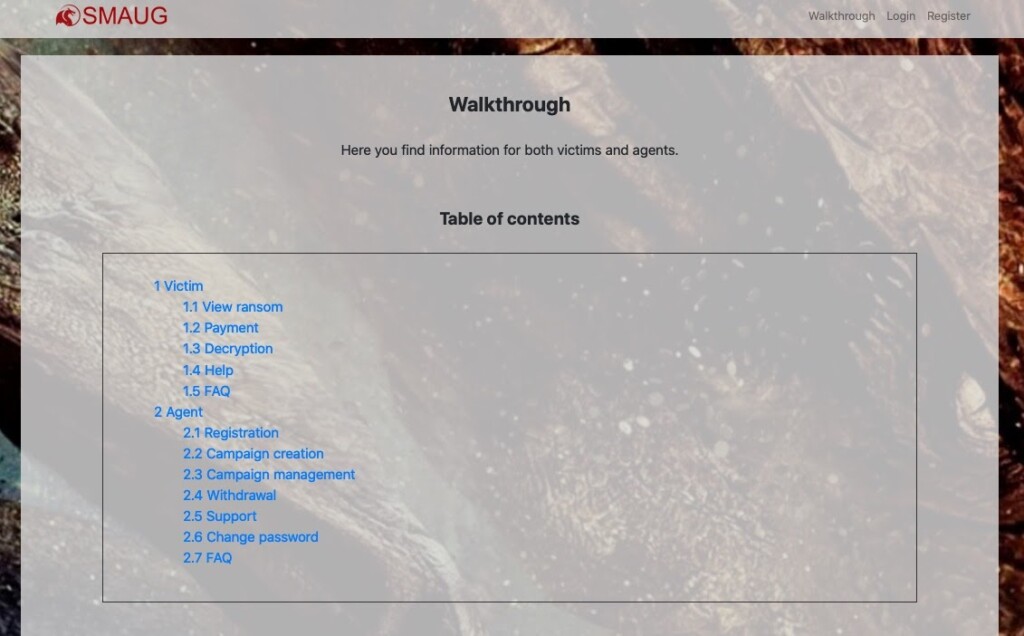
The onion-based portal for the payments is rich in information and features a user-friendly interface, while the “walkthrough” is legitimate-software-level good.
Source: Sentinel Labs
However, there is a single limitation, and this is infecting CIS-based (Commonwealth of Independent States) organizations. That would be Armenia, Azerbaijan, Belarus, Kazakhstan, Kyrgyzstan, Moldova, Russia, Tajikistan, and Uzbekistan.
This tells us a lot about the origins of SMAUG, and the group is very serious about this rule, threatening to ban any member who dares to violate it.
Read More:
- The “Thanos” RaaS Is Moving Forward and Growing in Popularity
- Nemty Ransomware Closes Down RaaS Operations and Goes Private
- “Cyrat” Is a New Ransomware Strain Disguised as a DLL Fixer