New Phishing Campaigns Impersonating Russian Services Use Gophish to Deploy RATs
- Hackers were seen deploying new PowerRAT and DCRAT via campaigns based on phishing emails.
- Russian-speaking users are targeted by threat actors impersonating Russian services like Yandex Disk and VK.
- The attackers leverage malicious documents or HTML-based infections to infect target devices.
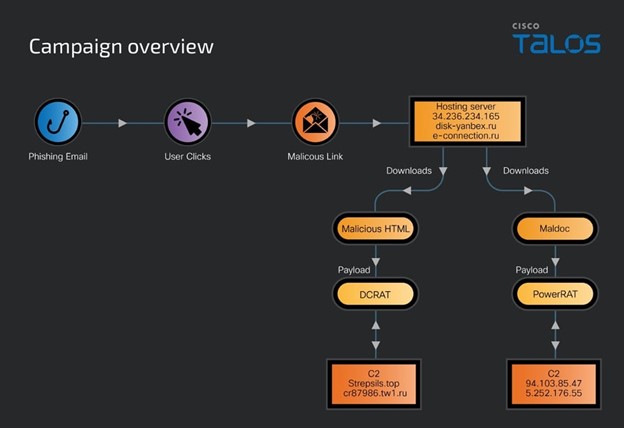
A concerning phishing campaign leveraging the open-source Gophish framework to deliver remote access trojans (RATs) such as DarkCrystal RAT (DCRat) and a new variant known as PowerRAT has surfaced.
This campaign targets Russian-speaking users with sophisticated tactics, according to the latest Cisco Talos security report.
According to its developer, the Open-Source Gophish is an easy-to-deploy phishing toolkit for conducting security awareness training.
The attack vectors utilized include modular infection chains that begin with either malicious documents (Maldoc) or HTML-based infections, actively involving victims in triggering the infection sequence.
These phishing emails mimic popular Russian services, like Yandex Disk and VK, to establish credibility and lure unsuspecting users.
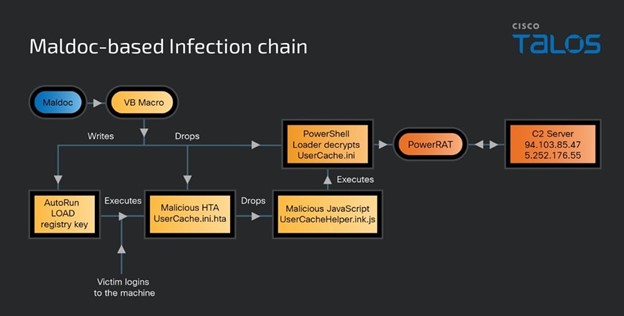
Upon opening the malicious Microsoft Word document and enabling macros, a Visual Basic macro executes, setting off a chain reaction. This macro extracts an HTML application (HTA) file and a PowerShell loader, which are instrumental in perpetuating the infection.
The HTA file deploys a JavaScript file executed via "cscript.exe," a legitimate Windows binary, to further advance the attack.
The PowerShell loader is designed to decode and execute the PowerRAT payload directly within the victim's machine memory. This malware performs system reconnaissance, collecting sensitive data such as drive serial numbers. It then connects to remote servers in Russia for additional command-and-control instructions, potentially leading to further infections.
PowerRAT stands out for its modular functionality, allowing the execution of other PowerShell scripts or commands. If the primary server fails to respond, it can autonomously decode and execute an embedded script, indicating ongoing development and adaptability.
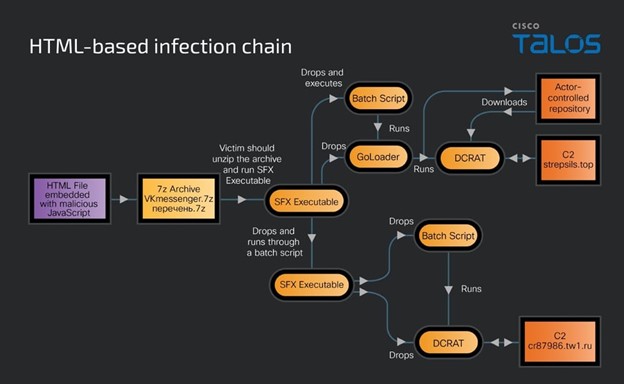
An alternative infection sequence employs HTML files with embedded malicious JavaScript. These files, when activated, initiate a multi-step process culminating in the deployment of DCRat malware. The use of HTML smuggling techniques to deliver payloads such as password-protected SFX RAR files is a notable aspect of this campaign.
In other recent news, a sophisticated malicious campaign targeted political figures and government officials in Malaysia with Babylon RAT via malicious ISO files.