A Wave of New ‘Panda Stealer’ Strain Infections Troubling Crypto-Holders
- There’s a new info stealer distributed aggressively in certain countries, and it’s called ‘Panda Stealer.’
- The malware is mainly going against digital crypto wallets, but they can also steal credentials and take screenshots.
- There are strong indications of a link between ‘Panda Stealer’ and the Phobos ransomware group.
There’s a new crypto-stealer circulating out there called ‘Panda Stealer.’ According to researchers at Trend Micro, it is a modified fork of ‘Collector Stealer,’ following the same file-less approach to evade AV detection. According to telemetry data analyzed by the security company, the new wave of attacks targets mostly the United States, Australia, Japan, and Germany.
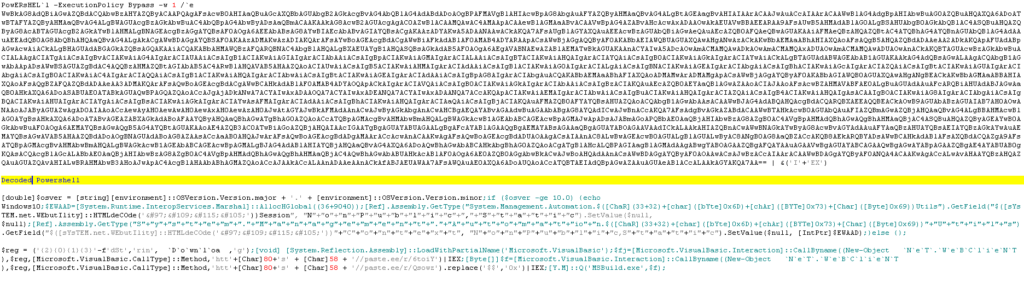
The distribution method is spam emails that involve some form of business quote requests and have Excel file attachments. These files are laced with malicious macros that download a loader, and finally, that loader fetches and executes ‘Panda Stealer.’ Alternatively, there are attachments of Excel files containing a formula that utilizes a PowerShell command, accesses the paste.ee service, runs a second encrypted PowerShell command, hollows a legitimate MSBuild.exe, and replaces it with the Panda Stealer payload (also fetched via paste.ee).
In terms of capabilities, the Panda Stealer can collect the following data from a compromised system:
- Private keys and transaction histories from digital wallets like Dash, Bytecoin, Litecoin, and Ethereum.
- Credentials from apps like NordVPN, Telegram, Discord, and Steam.
- Cached data, cookies, passwords, and card details from a range of web browsers.
- Captures screenshots.
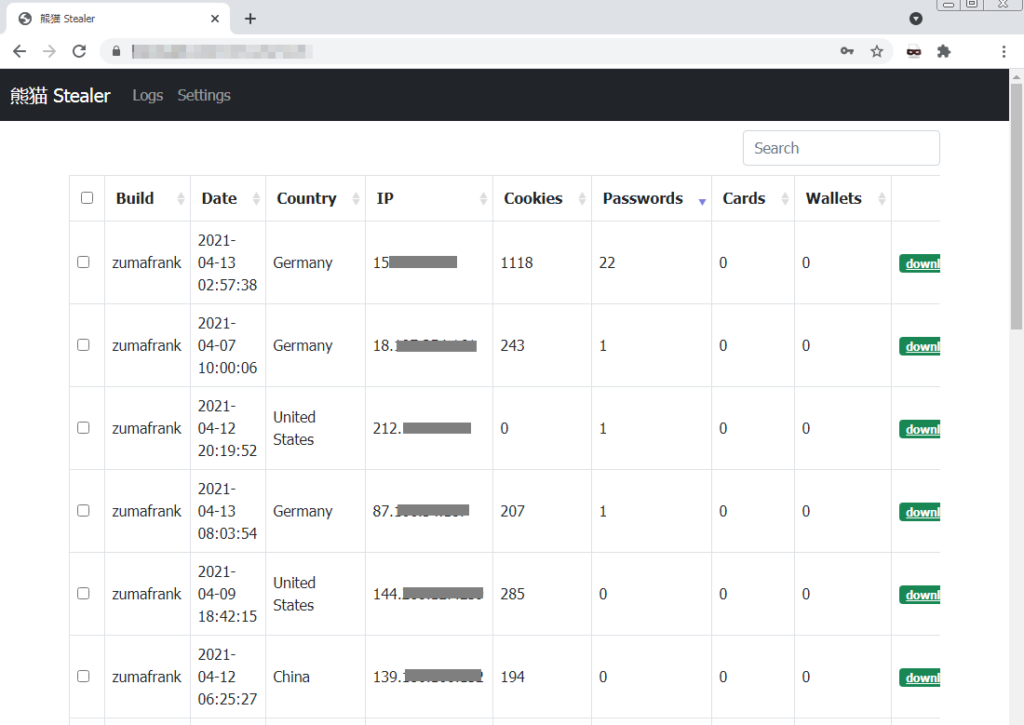
The malware drops files under the %Temp% folder, stores them under a random file name, and then packages them before sending them to the C2 server. Trend Micro was able to discover more than 140 C2 servers and over ten download sites - so for a full list, make sure to check out the detailed report.
In terms of attribution, we’ve had an interesting tip from Morphisec’s CTO, Michael Gorelik, who has indications that ‘Panda Stealer’ is actually linked to the Phobos ransomware group. A month ago, we reported about an update on the way Phobos was being delivered, and we saw a suspiciously similar PowerShell script using base64 encoding to fetch a payload through paste.ee and then perform a string replacement to a hollowed MSBuild.exe process.
Gorelik believes that malicious actors are now treating info stealers as a standard space to maintain a presence in due to the value spikes that the cryptocurrency universe is going through at the moment. Thus, hackers are quick to adapt and use their existing arsenal with trusted methods to create powerful info stealers and grab a piece of the pie. Morphisec reports that over the last 12 months, 31% of all attempted endpoint attacks came from info stealers.