New Mandrake Spyware Variant Found on Google Play Store Hiding for Two Years
- Android cyber-espionage platform Mandrake was seen on the Google Play Store again.
- The new variant, with upgraded obfuscation and evasion techniques, infiltrated the Android app store in 2022.
- It managed to remain undetected while being downloaded 32,000 times by unsuspecting Android users.
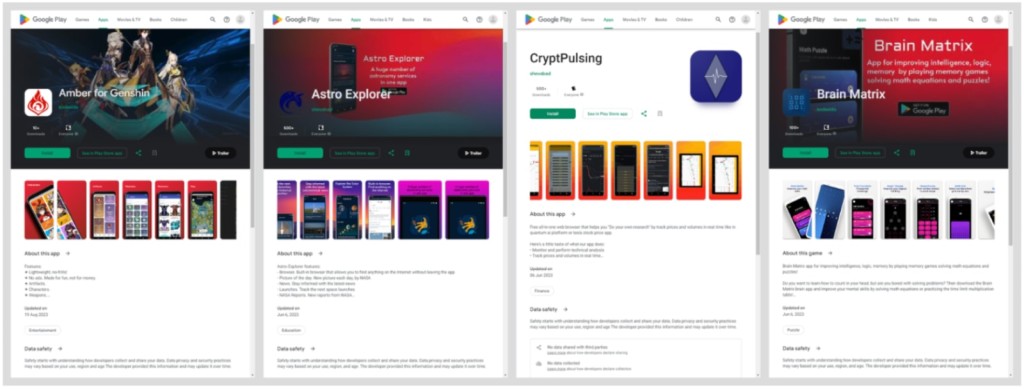
Five Mandrake spyware apps stayed available and undetected on Google Play from 2022 to 2024, totaling more than 32,000 installs, a new report by Kaspersky security researchers says. According to VirusTotal, as of July 2024, no vendor had detected any of the apps as malware.
The sophisticated Android cyber-espionage emerged after a two-year break with a new and improved version that displayed new layers of obfuscation and evasion techniques.
It now moved the core malicious functionality to OLLVM-obfuscated native libraries and used certificate pinning to prevent the capture of SSL traffic while communicating with command-and-control servers (C2) registered in Russia.
Moreover, the new version is equipped with sandbox evasion and anti-analysis techniques, testing whether Mandrake was running on a rooted device or in an emulated environment via Frida detection.
Out of the five malware apps on Google Play, the one with the highest number of downloads was AirFS, which pretended to be a file-sharing app. With north of 30,000 installs, it was also the one with the most longevity and most recently updated. Its reviews revealed the app did not work or stole data from user devices.
The latest campaign uses the same dropper, loader, and core stages as the previous versions of Mandrake but moved from hiding the first stage malicious activity in DEX files to the native library libopencv_dnn.so, which is harder to analyze and detect. Moreover, it is heavily obfuscated with OLLVM.
Some samples even have only two stages – the dropper decrypts an APK file from its assets, combining the loader and core.
Mandrake was first documented in 2020 when Bitdefender researchers highlighted the malware's sophisticated spying capabilities and noted that it has operated in the wild since at least 2016. The original Mandrake campaign had two major infection waves between 2016–2017 and 2018–2020.