New Malware Family ResolverRAT Distributed in Global Phishing Campaign Targeting Companies
- ResolverRAT employs a multi-pronged approach to bypass traditional defenses and maintain an active presence.
- It spreads via phishing emails employing fear-based themes like legal infractions or copyright violations.
- Evidence suggests it is part of an advanced, global operation targeting multiple corporate entities across regions, languages, and industries.
A new and sophisticated remote access trojan (RAT), named ResolverRAT, targets enterprises with advanced stealth and evasion techniques. This malware was recently identified during a threat analysis of a recent attack.
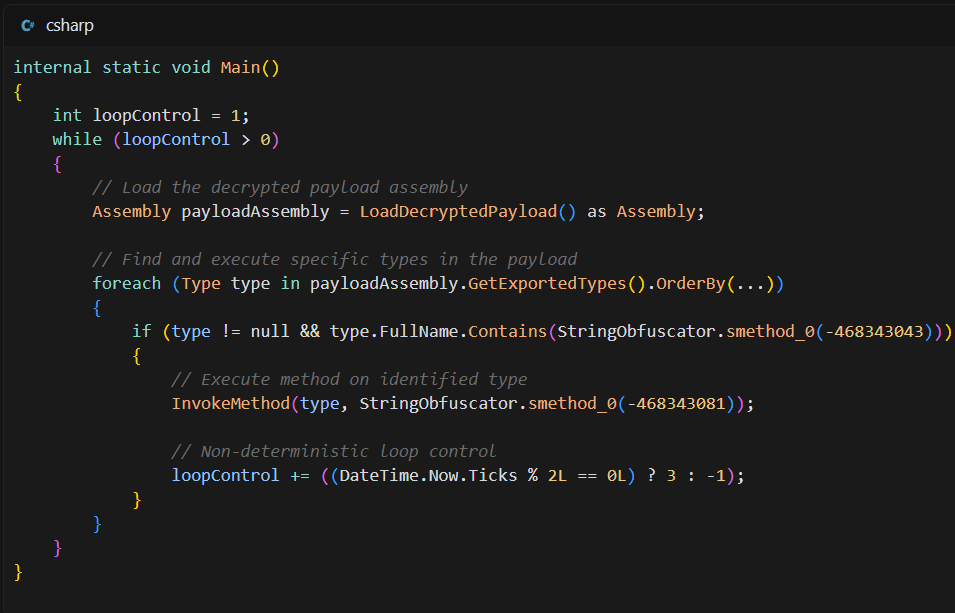
ResolverRAT earned its name for relying heavily on runtime resource resolution and complex in-memory execution, which make detection via static or behavioral analysis tools incredibly difficult, a comprehensive Morphisec cybersecurity report says.
The malware is not just a variant of previously identified campaigns; its architecture and tactics justify its classification as a new malware family. ResolverRAT surfaced in multiple attack waves, with the most recent incident observed on March 10, 2025.
ResolverRAT employs a multi-pronged approach to bypass traditional defenses and maintain an active presence within compromised systems.
Utilizing fear-based themes like legal infractions or copyright violations, emails are tailored in the native languages of target regions to enhance legitimacy. Subject lines include phrases like "Gathering Evidence of Copyright Violation" (translated across languages such as Hindi, Turkish, Italian, and more).
The malware chains infected DLLs with legitimate executables, inserting itself invisibly into enterprise systems. Notably, it has used the hpreader.exe executable, reinforcing patterns previously observed in Rhadamanthys and other malware.
ResolverRAT deploys encrypted payloads concealed through AES-256 encryption and compressed with layered GZip algorithms while keeping the full payload entirely in memory. The RAT hides behind obfuscated resource strings and employs Dynamic Resource Handling, and communication blends in with legitimate network traffic.
The malware bypasses SSL inspection by embedding fake certificates and conducting private handshakes directly with its command-and-control (C2) servers.
Evidence suggests ResolverRAT is part of an advanced, global operation targeting multiple corporate entities across regions, languages, and industries.
Detailed analysis reveals shared tactics and infrastructure links between ResolverRAT and the campaigns documented by Check Point Research and Cisco Talos. These earlier campaigns used similar file structures and email themes, signaling a possible affiliate model or coordinated effort among threat actor groups.