New Malware Family “Coper” Spreads Among Colombian Android Users
- A new family of banking trojans called “Coper” targets Colombian Android users, customers of ‘Bancolombia’.
- The apps are very tricky, abusing multiple permissions to ensure that they remain active and are hard to remove.
- The entire set of the malware apps is still available for download from the Google Play Store, as the apps don’t have the malicious module.
There’s a new family of Android trojans circulating out there, unfortunately even finding their way into the Play Store, targeting mainly Colombian users for now. The set of the malicious apps was discovered by researchers at Doctor Web, who have given it the name “Coper.” The apps feature a modular architecture and a multi-stage infection mechanism and also deploy several protective techniques to defend against detection and removal.
“Coper” apps pretend to be the official Android apps of Grupo Bancolombia, a large financial institution in the Latin American country. They mimic the genuine apps right to the icon and GUI level, but the lack of proper functionality is what secures their bad review scores on the Play Store. Notably, they are still available on Android’s official app store as Google hasn’t removed them yet.
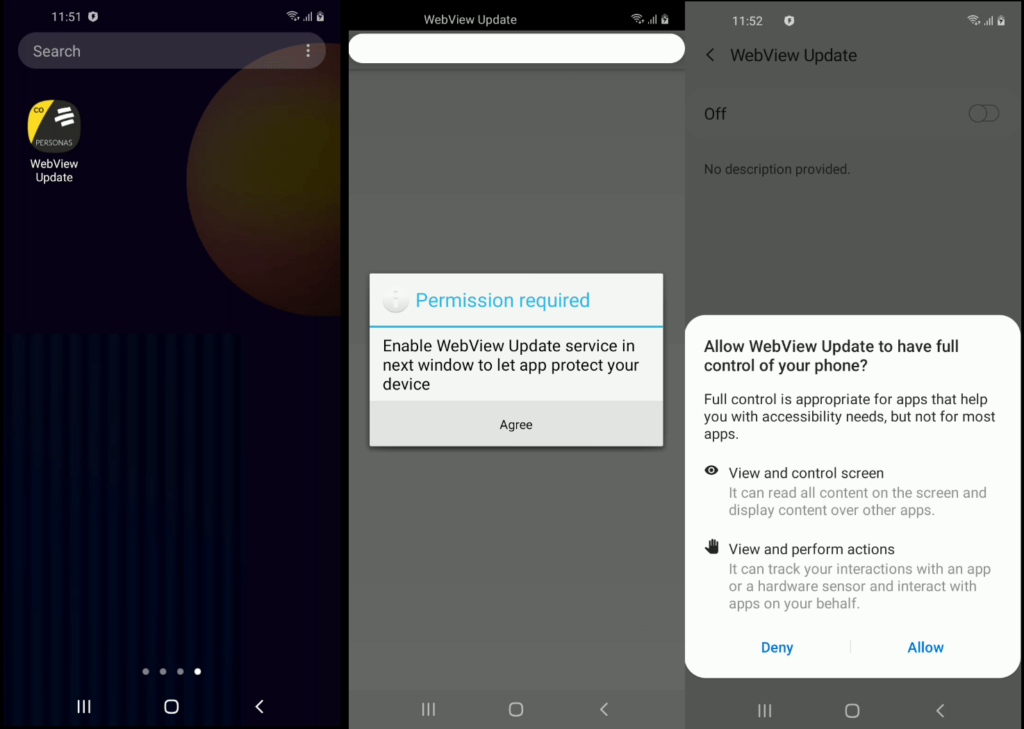
Upon installation, the trojan apps attempt to fetch the main malicious module. The fact that this module is missing from the core of the apps explains how they passed Play Protect checks. The app is actually decrypting and executing a dex file disguised as an HTML file, and at the same time, requests permission to the Accessibility Services. This ensures that the trojan will be able to serve the victim various false messages and overlays on the screen, click on buttons and links without requiring user interaction, and read the content of other apps.
In other cases, the malware requests to be excluded from battery optimizations to ensure that it remains active and running at all times in the background. If the victim isn’t careful enough and grants the permission request, the trojan is practically allowed to do anything on the infected device. That would include the following actions:
- send USSD requests
- send SMS
- lock the device screen
- unlock the device screen
- start intercepting SMS
- stop intercepting SMS
- display a push notification
- re-display phishing window on top of the specified app
- run a keylogger
- stop a keylogger
- uninstall applications specified in the command
- uninstall itself with the dropper app
- intercept and send contents of incoming push notifications to the C2
To protect themselves from deletion, the trojan apps mask their presence as system apps using the cog icon and also monitor what the user is doing to prevent manual removal. For example, if the user attempts to open the Play Protect page, or visits the system app list, or attempts to review the trojan’s access rights, the malware simulates a Home button click, abusing the Accessibility Services permissions to take the victim back to the home page.
To avoid having to deal with nasty infections like that, only install apps from the official bank website or follow a link to the Play Store from there. Also, make sure that you read a few user reviews, be very cautious with permission requests during installation, and use a mobile AV tool that could catch masked threats like the "Coper."