New Malicious Android Apps Found on Google Play Store
- New ad-clickers, spyware, and premium service subscription apps have been discovered on the Play Store.
- All of the reported apps were removed from the Play Store or cleaned by now, so users are advised to update or remove them.
- These apps are making a profit for their developers by increasing the internet data consumption for the users.
Google has been trying to render Play Store a safe place for Android users for years now, but it remains a tough to achieve feat, apparently. In November 2019, the “App Defense Alliance” was formed, bringing five mobile security experts together and promising a new age in the Play Store security. All apps would have to pass through their advanced static and dynamic analysis tools before being approved for Android’s official app store. Yet, here we are again, reporting a fresh batch of malicious apps that were available on the Play Store and which were boasting the “Play Protect” approval shield.
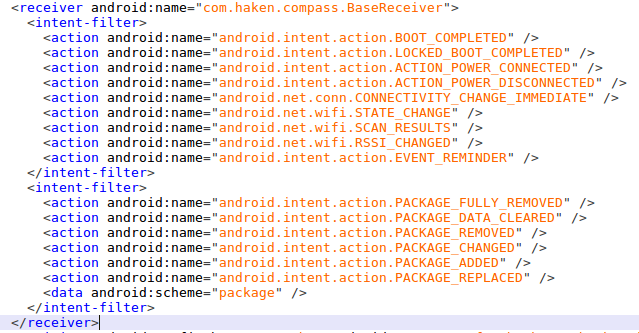
Four researchers at CheckPoint are warning about eight "Haken clicker" apps, 48 "BearClod clicker" apps, and another four "Joker" apps that have infested Google Play recently. A total of 78 million users downloaded these apps, and some of them are still available on the Play Store at the time of writing. The researchers clarified that those still present should be new, "clean" versions of the apps, so they are reportedly safe to use now (as long as they are updated). For the complete list of problematic apps, check out CheckPoint’s detailed report.
Clickers are essentially adware apps that hijack the user’s ad profile ID, fetch ads, and conduct virtual clicks. The money from this fraudulent activity goes to the developer's pocket, but the spike in internet data and battery consumption burden the users, of course. The “BearClod” family of apps performs the ad-clicking by using JavaScript code, while the “Haken” clickers are utilizing native code injection on the AdMob library and Facebook. These apps secure the “BOOT_COMPLETED” permission to ensure that the click-fraud action will initiate after resetting the device, even if the user won’t launch the malicious app.
Source: CheckPoint Research
As for the "Joker" apps, these are spyware and automatic subscribers to premium services. This family of apps appeared last year and keeps on resurfacing on the Android Play Store every now and then. The process involves fetching a payload from the C2 infrastructure, which then checks if the device is from the US or from Canada. If it's not, the malware loads the configuration that came from the C2 and starts listening to incoming SMS. The configuration file also contains URLs pointing to premium services that are opened in a hidden WebView and then the user automatically is subscribed to the services, and without him realizing it at the time. The subscription comes with an affiliate referral cut that goes to the developer, while the user is called to pay for the service on their contract bill.
#Joker Trojans on Google Playhttps://t.co/q2iWCcNd9v Feb 18, 10,000+ installshttps://t.co/TJcfsmz5FP Feb 19, 1,000+ installshttps://t.co/EagH4xZymj Feb 20, 10,000+ installs pic.twitter.com/lDfDcbhKFk
— Tatyana Shishkova (@sh1shk0va) February 21, 2020