New Gorilla DDoS Botnet Hits 100 Countries with Over 300,000 Attacks
- A relatively novel botnet malware family issued more than 300,000 attack commands targeting over 100 countries worldwide.
- These predominantly targeted distributed denial-of-service attacks aimed at universities, government websites, and more.
- Researchers say Gorilla uses various DDoS methodologies and encryption algorithms commonly associated with the Keksec group.
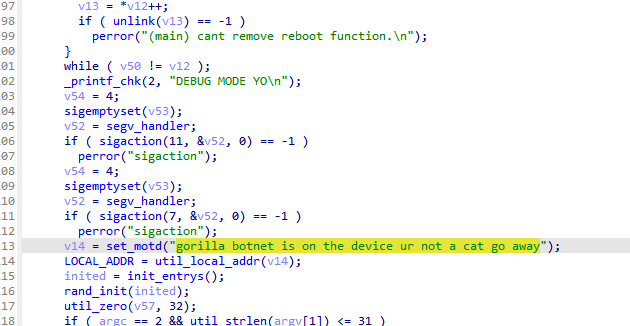
A formidable new botnet malware family named Gorilla, also known as GorillaBot, was seen emerging from the shadows of the leaked Mirai botnet source code by security researchers from NSFOCUS. Gorilla Botnet’s attacks hit over 20,000 targets in 113 countries.
More than 300,000 attacks were launched between September 4 and 27, 2024, with a peak of 20,000 commands daily that predominantly targeted distributed denial-of-service (DDoS) attacks.
China, the U.S., Canada, and Germany are among these countries, and key sectors under attack include universities, government websites, telecoms, financial institutions, and the gaming and gambling industries.
The researchers identified the new botnet last month, but Gorilla has been operational for over a year, according to cybercrime analyst Fox_threatintel.
Gorilla employs various sophisticated attack vectors, including UDP flood, ACK BYPASS flood, Valve Source Engine (VSE) flood, SYN flood, and ACK flood methods. The UDP protocol's connectionless nature is leveraged for IP spoofing, facilitating massive traffic generation.
Beyond its broad attack methods, Gorilla is notable for its adaptability across multiple CPU architectures, including ARM, MIPS, x86_64, and x86. It communicates with five predefined command-and-control (C2) servers to execute DDoS commands.
A striking aspect of this malware is its embedded capability to exploit a security flaw in Apache Hadoop YARN RPC for remote code execution—a vulnerability that has been exploited in the wild since 2021.
Gorilla ensures persistence on infected hosts by creating a service file configured for automatic execution at system startup, responsible for downloading and executing a shell script from a remote server. Additional commands are incorporated to maintain control upon system startup or user login.
NSFOCUS highlights Gorilla's innovative utilization of various DDoS methodologies and encryption algorithms commonly associated with the Keksec group. These measures effectively conceal key information and employ numerous techniques to sustain long-term control over IoT devices and cloud hosts, indicating a high level of counter-detection awareness.
Meanwhile, a DDoS distribution site was disabled following a law enforcement sting dubbed Operation Power Off, as per the UK's National Crime Agency (NCA) announcement, which described the DDoS-for-hire service DigitalStress as the world's most prolific operator in the field.