New Exploit for Bypassing Windows Defender Application Control Leverages JavaScript C2
- Hackers found a new way to bypass WDAC via an advanced Command and Control framework developed in JavaScript.
- This exploit involves leveraging a combination of methods, including Electron applications and signed node modules.
- Attackers could load untrusted JavaScript code into trusted processes to bypass WDAC constraints.
A cutting-edge method for bypassing Windows Defender Application Control (WDAC) leverages an advanced Command and Control (C2) method called Loki, revealing how sophisticated attackers are exploiting trusted applications to evade even the most robust enterprise security measures.
Windows Defender Application Control is a critical Microsoft security feature designed to restrict the execution of untrusted software, creating a secure foundation for systems. The exploit is demonstrated in the latest report coming from IBM’s X-Force Red team.
WDAC plays a vital role in defending enterprises with high-security regulations, particularly in sectors such as finance and healthcare. Microsoft actively incentivizes research into bypass methodologies by offering bug bounties for successful WDAC breaches.
Attackers exploit vulnerabilities within Electron-based applications, notably the legacy version of Microsoft Teams. By targeting signed components of these applications, the team demonstrated how attackers could load untrusted JavaScript code into trusted processes, bypassing WDAC constraints.
Named “Loki C2,” this novel C2 framework was developed entirely in JavaScript. It allowed Cooke and his team to bypass WDAC policies and continue post-exploitation activities undetected.
Loki C2 enabled the execution of commands, file manipulation, and reconnaissance without loading unsigned DLLs, which are typically blocked by WDAC.
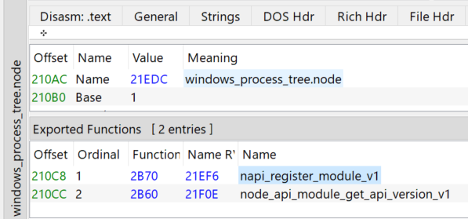
The researchers also addressed operational security by avoiding detectable actions, such as spawning PowerShell processes, which are typically flagged by Endpoint Detection and Response (EDR) solutions. Instead, Loki C2 leveraged legitimate Node.js modules, like Microsoft-signed windows_process_tree.node, to circumvent detection.
The X-Force Red team demonstrated the attack on a Windows Server 2025 instance configured with WDAC’s strict "Default Windows Mode" policy.
By replacing the resources of a signed Electron application, such as Microsoft Teams, with malicious JavaScript, the researchers established control while maintaining WDAC’s trust in the application.
While many Electron applications have implemented integrity checks to prevent JavaScript tampering, numerous actively distributed applications remain exploitable. Similar techniques were seen in a 2022 supply chain attack involving the MiMi chat application.