New Dharma Ransomware Variant Is Using the “COVID” Extension
- A new COVID-themed variant of the Dharma ransomware is infecting systems around the globe.
- The ransomware uses strong encryption and randomized keys, while the actors are defining ransoms arbitrarily.
- The new variant deploys various methods of persistence, defense evasion, and system recovery restraining.
Malicious actors are not only looking to take advantage of the COVID-19 pandemic, but they are also getting inspired by it. We have seen system-wiping malware tools getting the “COVID-19” name, and now we see a fresh ransomware variant based on Dharma, using a payload named “1covid” and giving the encrypted files the “.ncov” extension. We have recently covered the news about the Dharma/CrySiS source code being offered for purchase on the dark web, so the appearance of a new variant could be one of the many that are about to follow in the following months.
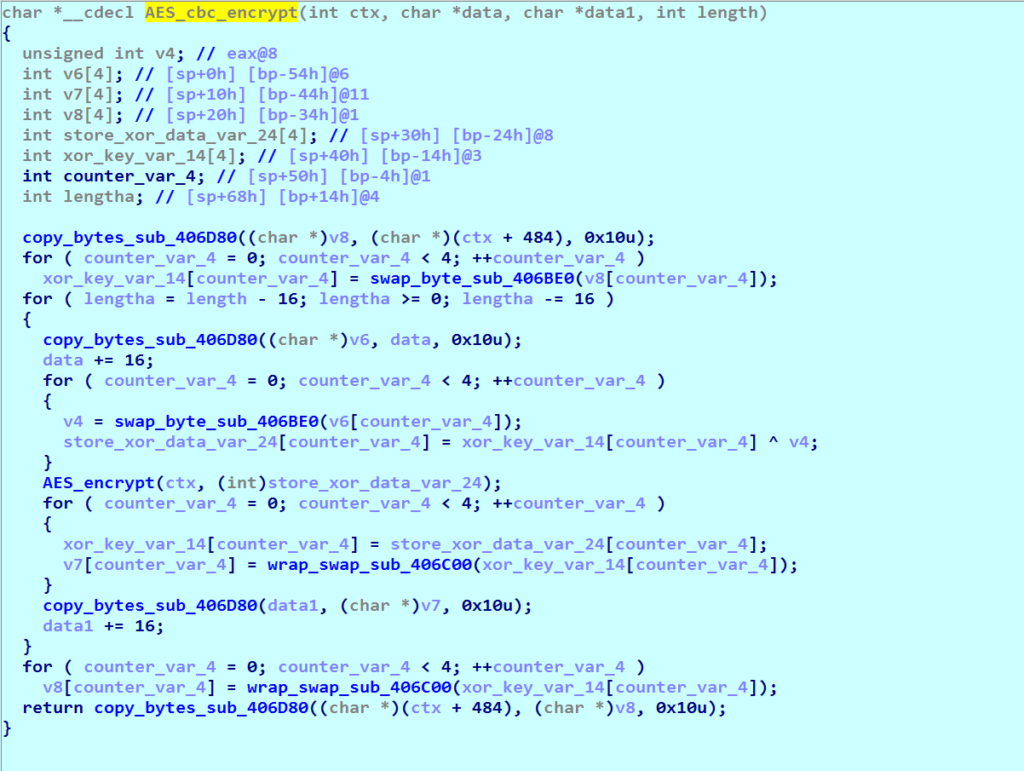
As reported by Quickheal researchers, who named the new ransomware variant “Ransom.Crysis.A3,” the actors are demanding a ransom in Bitcoin, and the price supposedly depends on how quickly the victim sends a message to “[email protected].” The victim is given a maximum of 24 hours, and the “typical” free encryption of a single file is also offered as proof of their capability. The encryption is done by using AES-256 (128-bit block + 256-bit key), and the same robustness that characterizes Dharma is making unlocking of the files pretty much impossible at the moment.
Source: Quickheal Blog
From a technical perspective, “Ransom.Crysis.A3” is checking for a list of services that could interfere with the encryption process and kills them beforehand. For example, network services and SQL servers are killed so that network drives are encrypted as well. Then, it drops a copy of the payload on the System32 folder and the Windows Startup, while a new registry entry is also written on the system. All of this is happening to establish persistence in the infected system, as well as to inhibit a successful system recovery.
Already, 63 out of 72 detection engines in Virus Total can flag “Ransom.Crysis.A3” as ransomware, so it is advised that you use an AV suite from a reputable vendor and keep it updated. If you receive an unsolicited email, don’t download and don’t execute any attachments that come with it. Finally, you should take frequent backups of your most valuable data and store them on offline media. If something goes wrong on your system, wipe everything by formatting the drives, and only then attempt to restore from backups. With the Dharma source code circulating out there, there’s going to be a wave of infections made by new variants until white-hat researchers finally manage to crack it.