New Chinese APT Named ‘Luminous Moth’ Discovered and Profiled
- A Chinese APT group named ‘Luminous Moth’ has been targeting Philippinese entities since December 2020.
- The actors are using a bulk approach of high-volume compromises but only proceed with a small selection.
- The malware and data exfiltration tools appear to be selectively deployed depending on the target.
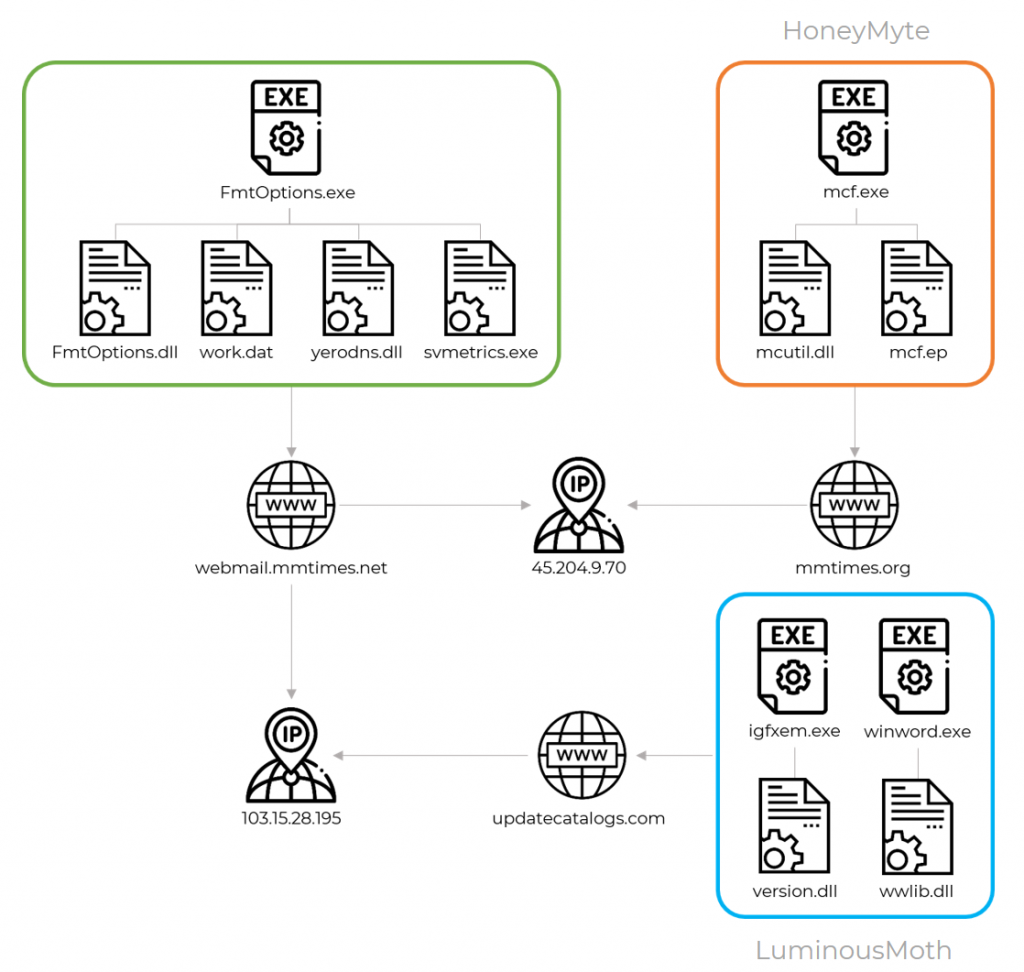
Researchers at Kaspersky have identified and profiled a novel APT group that appears to be based in China, naming it ‘Luminous Moth.’ The actors are using a unique set of tools and malware propagation methods, but their infrastructure shares parts with another notorious Chinese hacking group, ‘Mustang Panda.’ 'Luminous Moth' was seen targeting several hundreds of high-profile entities in the Philippines and tens of important organizations in Myanmar.
As Kaspersky details, this newly profiled APT follows a strange approach of launching high-volume attacks only to use a small selection of the compromised points to further its malicious activity. This obviously creates an opportunity for researchers and blows the hackers’ cover. One explanation for it is having the main payload propagate through USB drives to spread to other hosts. This is an “out of control” system that generates large amounts of collateral damage.
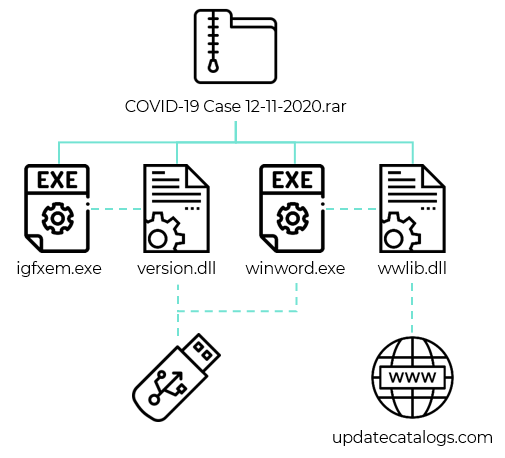
There are two ways 'Luminous Moth' deploys for breaking in. First, they send a spear-phishing email to the victim, which contains a Dropbox download link that fetches a RAR archive. In there, there’s a pair of malicious DLLs that are masqueraded to appear as a DOCX file. The second vector relies on the first, with the DLLs being sideloaded by two executables to spread to removable devices and also download a copy of the Cobalt Strike tool.
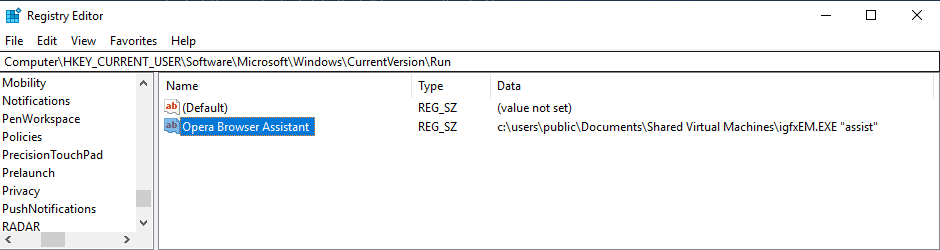
A registry value is also added to the infected system to ensure that the malware runs automatically at system startup. The entry is masked as “Opera Browser Assistant,” which is somewhat of a weird choice since Opera isn’t the most popular choice of browsers. Manually looking for and deleting this entry is highly unlikely anyway, though.
In several cases, 'Luminous Moth' deployed a fake Zoom application with a valid digital certificate owned by Founder Technology, a Shanghai company. This tool helped the hackers scan the infected filesystem for specific filetypes and then exfiltrate things of interest to the set C2 server. The configuration strings for this data exchange are encrypted (AES), and all files in the configuration files are encoded with Base64.
A Chrome cookies stealer was deployed in other cases, looking for the following values: SID, OSID, HSID, SSID, LSID, APISID, SAPISID, and ACCOUNT_CHOOSER. By using these values, the actors can duplicate Google account sessions and access valuable accounts like, for example, the victim’s Gmail account.