New Cactus Ransomware Strain Exploits Fortinet VPN Vulnerability
- Security researchers noticed a new variant of the infamous Cactus malware.
- The novel strain was observed abusing a known flaw in the Fortinet VPN client.
- The vulnerability permits authentication bypassing on the admin interface due to a faulty Apache HTTPD configuration.
Another iteration of the Cactus ransomware was seen by Trellix’s security researchers exploiting VPN vulnerability in the MICS Admin Portal in Ivanti MobileIron Sentry versions 9.18.0 and below. Hackers targeted Fortinet VPN, which offers SSL VPN and IPSec VPN, to exploit the VPN network and connect to internal ones.
The initial entry point occurred via the CVE-2023–38035 flaw, a vulnerability that may allow an attacker to bypass authentication on the admin interface due to an insufficiently restrictive Apache HTTPD configuration.
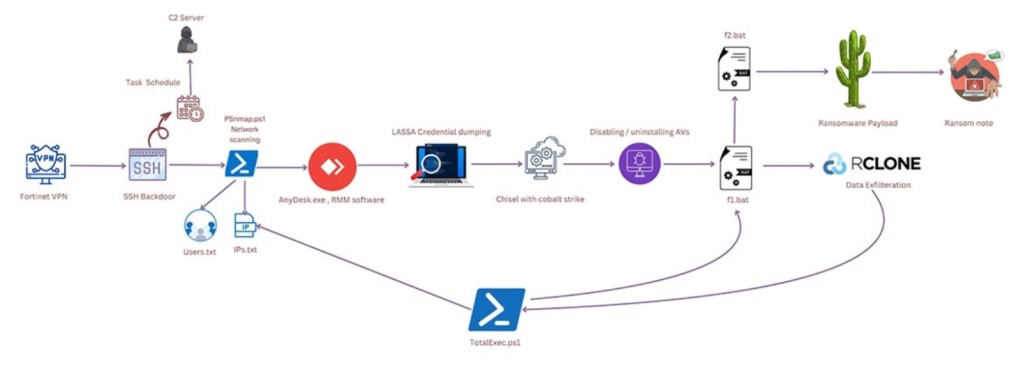
This infamous double-extortion ransomware usually exploits vulnerabilities in virtual private network (VPN) software to gain access to a target environment. It establishes command and control (C2) communications with its operator and maintains persistence across reboots via Scheduled Tasks.
The new strain managed to enter the internal network via public-facing applications and then created an SSH backdoor for the C2 server, listing the IP addresses and Users inside the network via the SoftPerfect network scanner or PSNmap tool.
Remote Monitoring and Management (RMM) tools like AnyDesk and Splashtop were used to maintain access to the C2 server, as well as Chisel with Cobalt Strike. The actors moved laterally by using the LSASS credential dumping technique from Web browsers and disk files.
Once a batch script silently uninstalled common antivirus software, the attacker created a new admin user account and used RClone for exfiltration on cloud storage. The attacker encrypted files via the OpenSSL library with RSA and AES algorithms. Finally, a PowerShell script executed the ransomware payload.
Cactus ransomware appeared in March 2023 and targeted over 100 commercial entities and high-profile victims.
In June, a new Fog ransomware variant was discovered abusing compromised VPN credentials to target the US education and recreation sectors, in some cases using administrator accounts to establish RDP connections to Windows Servers running Hyper-V and Veeam.
In recent news, a novel ransomware group known as EstateRansomware has been observed leveraging a now-patched flaw in Veeam Backup & Replication software that permits access to encrypted credentials.