New Banking Trojan ‘Bizarro’ Circulating Around Europe and South America
- There’s a new banking trojan called ‘Bizarro,’ which is targeting a wide scope of bank customers.
- The trojan is spreading in Europe and South America, while the actors are based in Brazil.
- The info-stealing capabilities of Bizarro are impressive, but the infection trick remains simple.
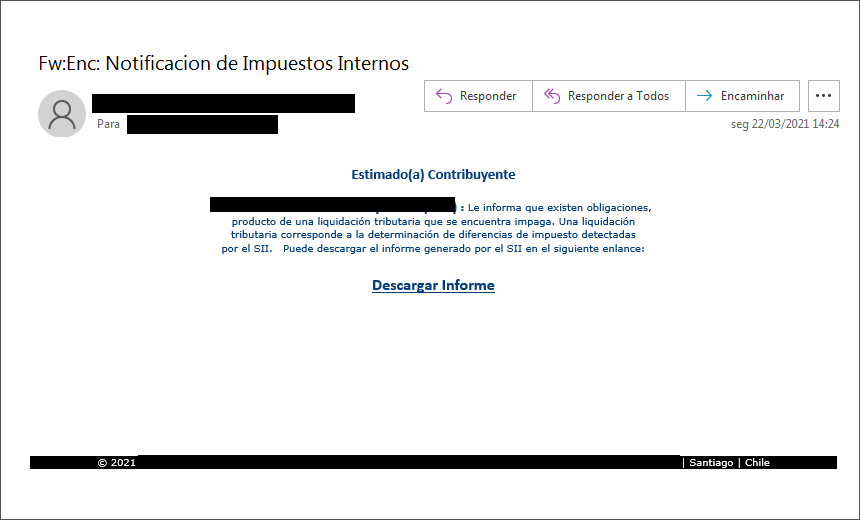
There’s a new banking trojan that targets European and South American bank customers, and it’s called ‘Bizarro.’ The malware is being distributed in the form of MSI packages which arrive as attachments on spam emails. According to the latest unveiling reports, Bizarro campaigns appear to originate from Brazil, while the actors use compromised WordPress, Amazon, and Azure servers to host their malicious packages.
The capabilities of Bizarro are the following:
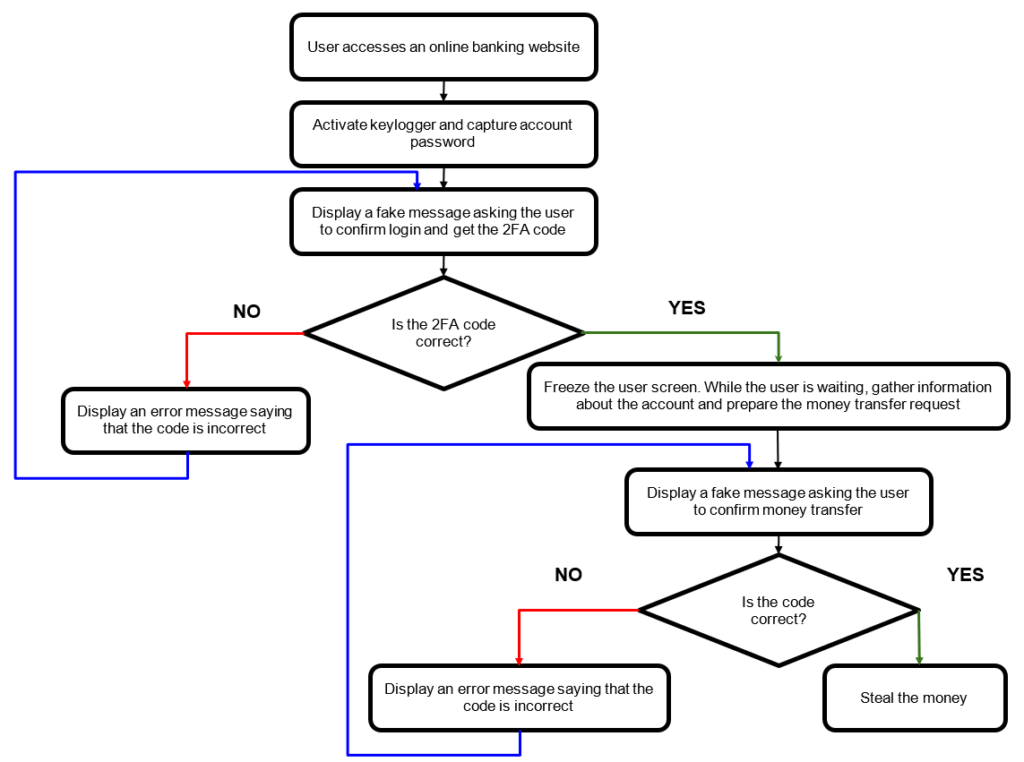
- It can capture login credentials entered on banking sites. To speed up this process, it reportedly closes your existing browser windows, so you are forced to log in. Bizarro also creates fake prompts to solicit 2FA codes.
- Bizarro constantly monitors the clipboard and will replace any Bitcoin address it finds there with its own (hoping, of course, to capture any transfers that were supposed to be paid into the original address).
- And last but not least, it is a full-blown backdoor, which gets fired up as soon as the user visits one of a set of hardcoded banking sites.
The backdoor offers a lot of options to the attacker, including:
- Gathering data about the infected system and sending them to the C&C server.
- Searching for and stealing files from the infected computer.
- Dropping files on the affected system (such as other malware).
- Remote control of the mouse and keyboard.
- Keylogging.
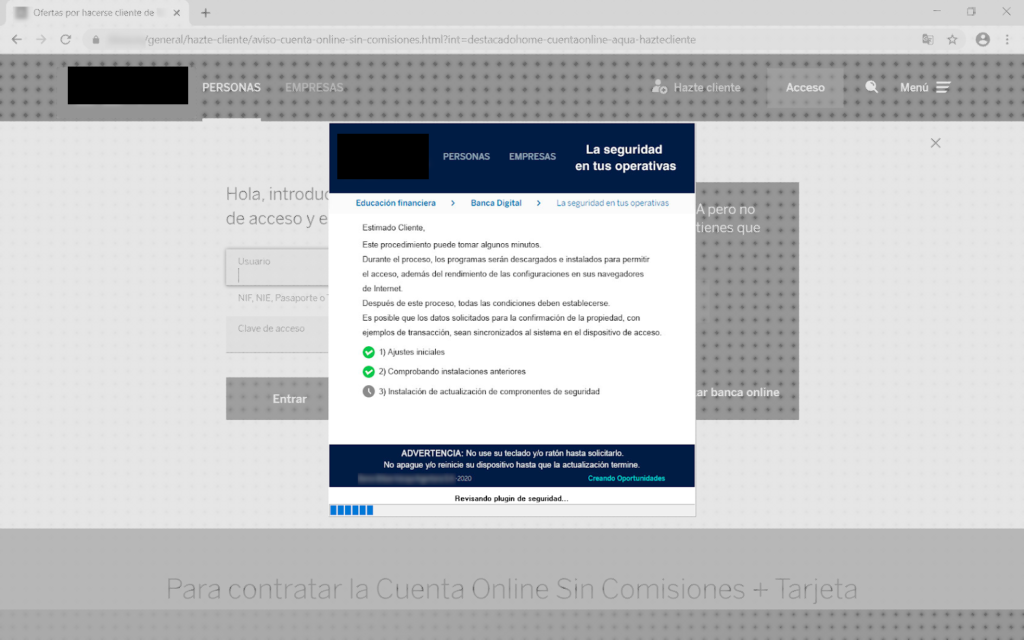
- Creating fake popup windows and messages. The messages are intended to slow down the user’s response time and include progress bars.
- Emulating banking sites on the fly.
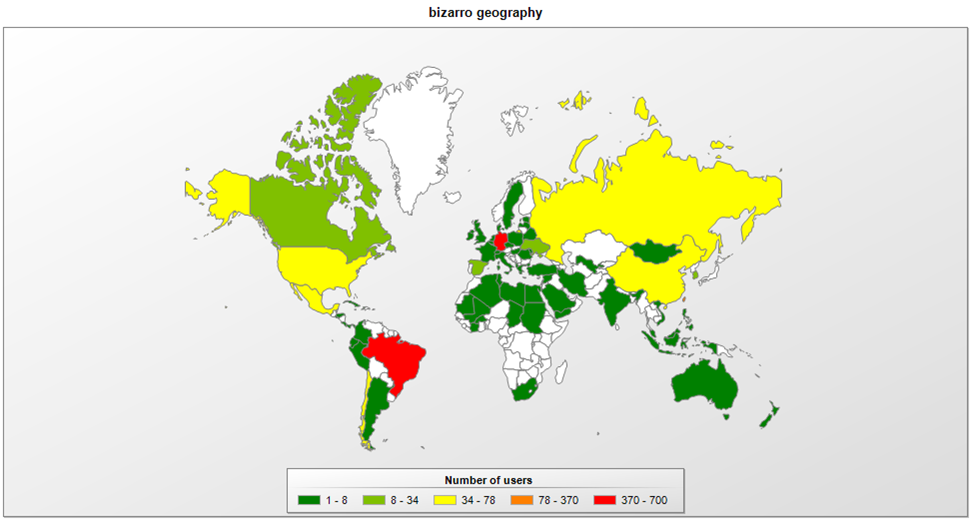
So far, researchers have seen the trojan mimicking at least 70 banks from various European and South American countries, so Bizarro’s scope is really wide. Most of the infections are in Brazil, Argentina, Chile, Germany, Spain, Portugal, France, and Italy.
The malware arrives in ZIP form, and it contains the payload “BIZARRO.DLL,” which is written in Delphi. Upon execution, the DLL exports a function that contains the malicious code, while analysts also point out that all functions have been heavily obfuscated to complicate research.
If we were to give you a single piece of advice to help you stay protected from these trojans, we would tell you to simply avoid downloading attachments that arrive via unsolicited emails. That should be a rule to follow no matter what claims are made in the content of the message, as these are always crafted to grab your attention and convince you that you need to take action. It’s always clickbait. Finally, keep an up-to-date security solution active on your system and scan files there before opening them.