A New APT Named SilverFish Was Uncovered by Researchers
- Yet another APT group linked to the SolarWinds attacks has been uncovered by Swiss researchers.
- The threat actors appear to serve Russian interests, but the attribution isn’t incontestable.
- The targeting of the group called SilverFish is high-level, and so is its operational sophistication.
Swiss researchers of the PRODRAFT threat intelligence team have published a detailed report into a new APT group of actors, which they named Silverfish. According to the team’s findings, this new group has links to the infamous SolarWinds attacks and also the persistent TrickBot campaigns we've seen in the second half of 2020.
Moreover, the group uses the same servers as EvilCorp, which is responsible for the development and distribution of the Dridex and the WastedLocker malware. All that said, the origin of SilverFish appears to be Russian, although PRODRAFT chooses not to give geography-based attributions and only focuses on attack patterns.
The new group was uncovered in December 2020 when PRODRAFT conducted an investigation for one of its clients in the financial sector who was affected by the SolarWinds supply chain compromise. The researchers dug into the IOCs shared by FireEye back then and created a unique fingerprint on one of the online servers used by the attackers. After a 12-hour scan on the entire IPv4 range using that fingerprint, they identified 200 more hosts using a similar setup.
Having mapped the C&C infrastructure, the researchers were able to monitor the Silverfish activities, identify victims, notify them with IOCs, and finally publish their detailed report to help the infosec community track the new APT properly.
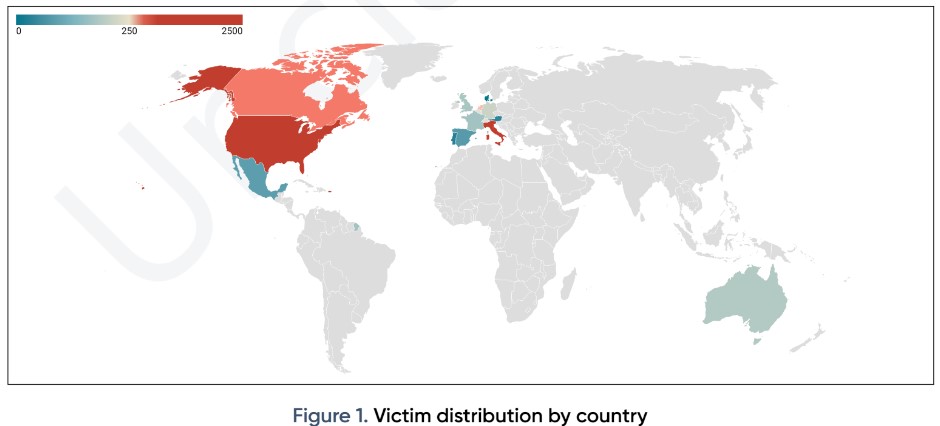
According to the stats published, SilverFish is responsible for at least 4,720 individual attacks since December 2020, mainly focusing on government entities, global IT providers, firms engaging in the aviation industry, and defense companies. In general, half of the targets are entities that have a market value of over $100 million.
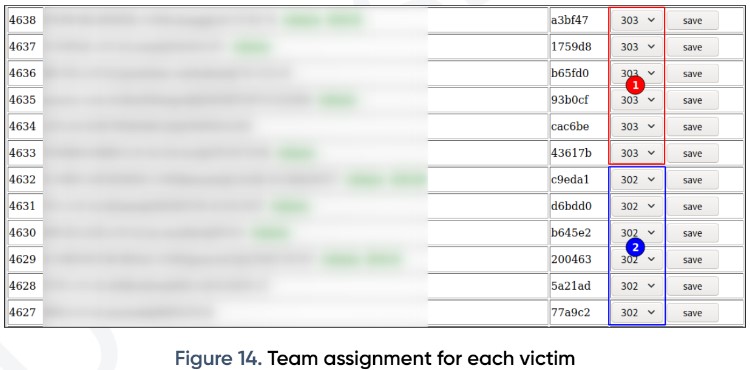
An interesting part of the SilverFish operation - as described by PRODRAFT - is its professional organization and working patterns. Reportedly, the actors are working in strict shifts between 08:00 and 20:00 UTC, Monday through Friday, so this is their full-time job. Also, there’s a certain level of organization in the C2 hierarchy, assigning targets to different groups and triaging them appropriately.
As for the tools used by SilverFish, the set would include Empire, Cobalt Strike, Mimikatz, Powershell, BAT, CSPROJ, JavaScript, and HTA files used for enumeration and data exfiltration. Of course, there’s a lot more going on, which is far too extensive for us to outline here, so for more in-depth technical details, you should check out PRODRAFT’s report on GitHub.