New “Agent Tesla” Variant Can Steal VPN Credentials From Registry
- A new variant of the “good old” Agent Tesla info-stealer targets browsers and VPN credentials.
- The malware establishing its presence in the registry and then sends stolen data to the C2 via FTP.
- The cheap and widely available malware has just become a lot more powerful, but it’s still easy to detect and stop.
The “Agent Tesla” RAT (remote access trojan) has been updated recently, and the new modules that have landed seem to focus on the stealing of credentials from VPN tools, various web browsers, FTP, and email clients. The particular info-stealer has been around for many years now, but seeing it getting upgraded and more powerful is changing the scene.
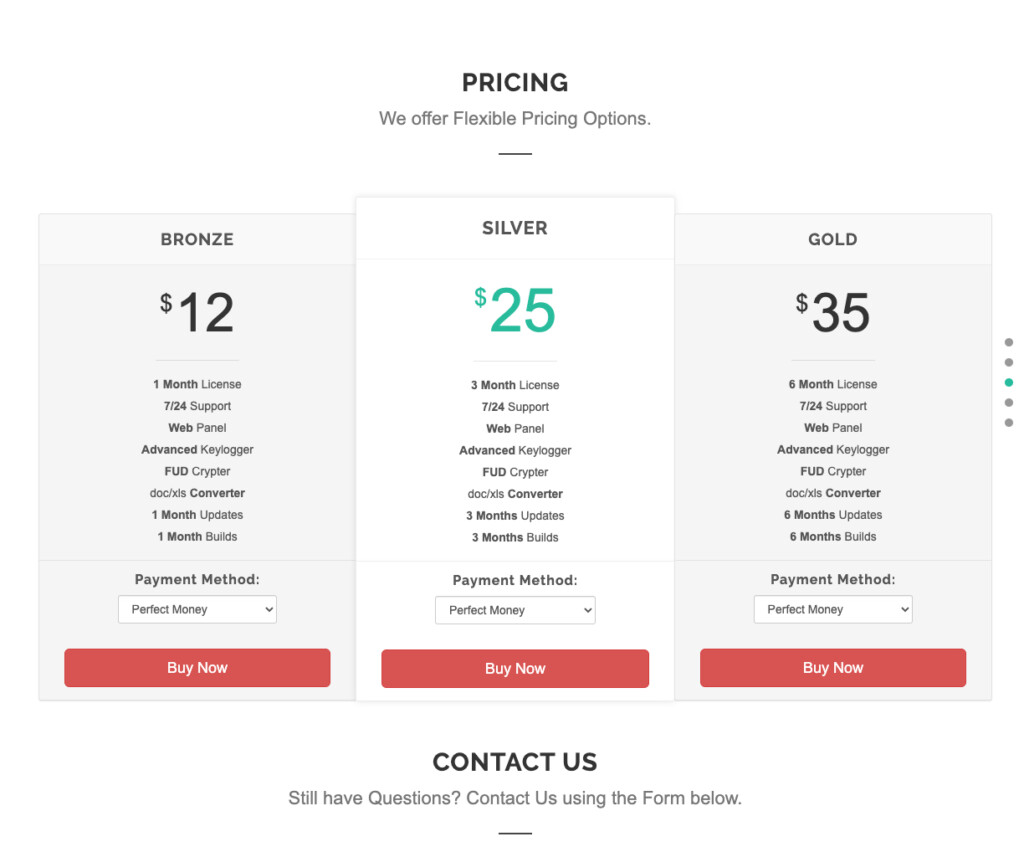
This is especially the case if the malware is popular in the cyber-crime community, inexpensive (Agent Tesla costs between $12 and $35), and widely available. BEC scammers like to deploy the particular malware family to compromise corporate networks further.
Source: Sentinel Labs
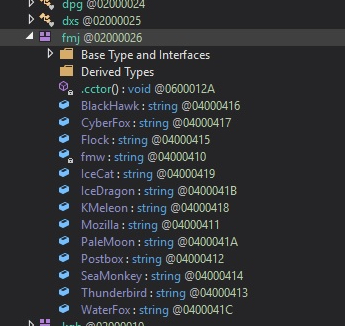
According to the latest report from Sentinel Labs, which is the cybersecurity firm that captured and analyzed the new Agent Tesla variants, the malware can now tap deep into the Windows registry, looking for configuration or support files where installed software points to.
Here are some of the tools that Agent Tesla’s new variant can target and harvest the user credentials from:
- Apple Safari
- Brave Browser
- Chromium (and derivatives)
- Google Chrome
- Comodo Dragon
- FileZilla
- IceCat
- Microsoft Internet Explorer
- Microsoft Edge
- Microsoft Outlook
- Mozilla Firefox
- Mozilla Thunderbird
- OpenVPN
- Opera Browser
- Opera Mail
- Postbox
- SeaMonkey
- UCBrowser
- Vivaldi Browser
Source: Sentinel Labs
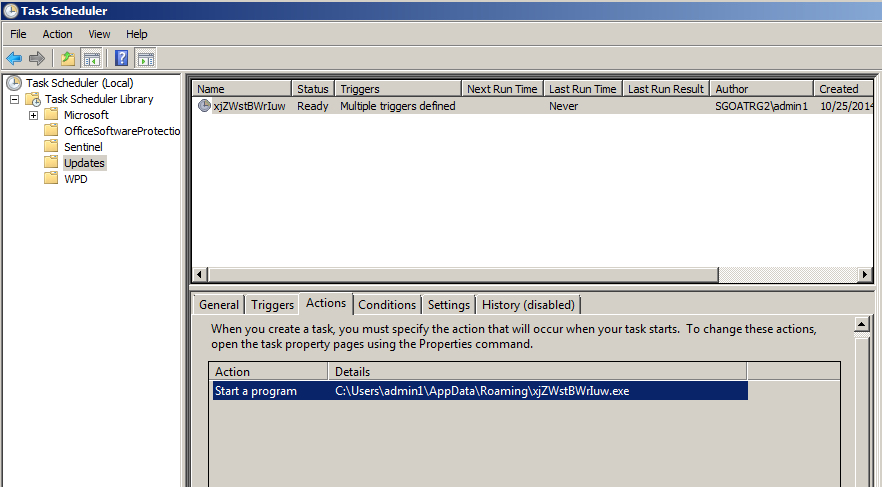
The collected credentials are then transmitted to the actors via SMTP or FTP. Besides the credentials, Agent Tesla is also attempting to gather local system information, discover wireless network settings and WiFi credentials, and add a registry key entry as well as a scheduled task for persistence.
All of this is making the malware extremely useful for low-level hackers and cybercriminals who don’t possess the skills to engage in highly-targeted operations. They simply figure a social engineering scenario, manage to plant Agent Tesla on their targets’ machines, and then enjoy a surge of crucial information arriving on the defined C2. All of this without having to spend more than a few bucks for the tool itself.
Source: Sentinel Labs
The obvious drawback of using “commodity” malware tools like Agent Tesla is that you can only compromise users who don’t use an AV tool or use one but never bother to update it.
Even newer versions like the one presented here are quickly included in the AV definitions and risk indicators. Even if they weren’t, heuristic systems would still catch the threat since the Agent Tesla fiddles with so many elements on the infected system, from the registry to the scheduler, conducting DLL search order hijacking and process injection.