New Actors Appear in the Threat Landscape While Old Ones Change Platform or Branding
- We are seeing some new actors joining the ransomware and data-stealing extortion game lately.
- There’s one new ransomware group claiming to have links with REvil, and another one that gives no opportunity for negotiations.
- Babuk has also jumped to a new sector, now operating a leak platform for other actors to join.
There’s some notable motility taking place in the threat landscape right now, with existing actors changing names and branding, some hopping to a different sector, and several new and promising groups appearing out of nowhere and calling for the community’s attention. This is a natural development in a dynamic space, especially now that established players have decided to go private or just lay low for a while.
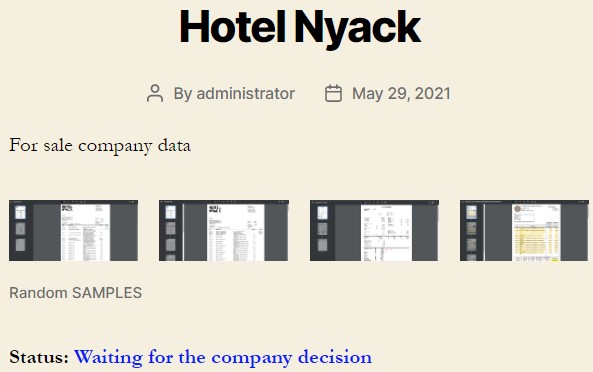
First, we have a spin of the REvil ransomware group called “Prometheus,” and based on its logo, there is a tight affiliation with the notorious group. Already, the new ransomware group has a dedicated data leak site up and listed 27 victims, including the Ghana National Gas and Hotel Nyack in New York. An impressive start for sure, and one that indicates a link with REvil - even if the latter hasn’t confirmed a connection yet.

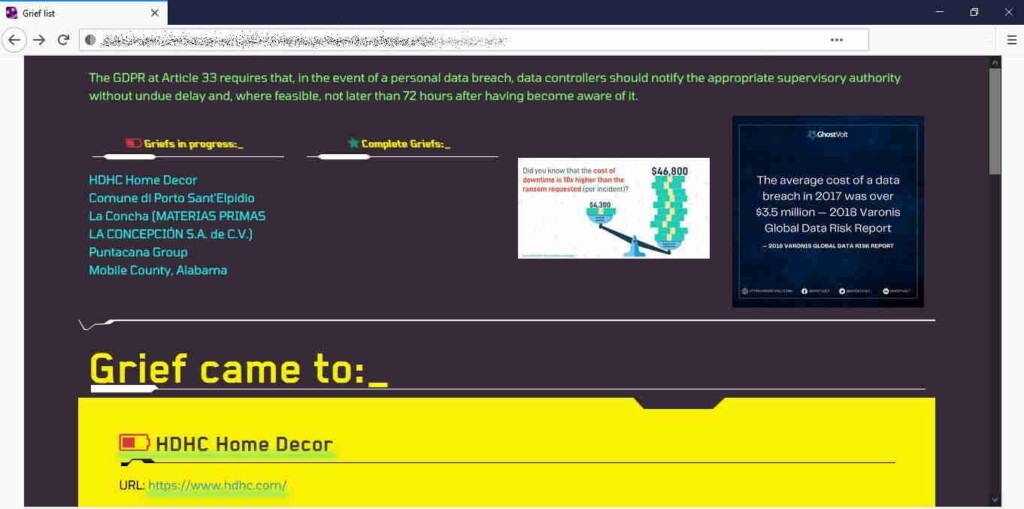
Second, we have the “Grief” ransomware group, which is a new operation that has already compromised several notable private and public entities from around the world. They, too, follow the same encryption+data stealing approach that raises the extortion heat for the victims. There’s even a GDPR reference on the leak site to make it clear for the compromised organizations that they have two options, pay the ransom or deal with regulator fines and the PR damage that with data breaches.
As these actors stated in a mini-interview to SuspectFile, they are unwilling to give victims plenty of negotiation time and room like other groups. They are not giving any discounts, and they are not holding anything back when it comes to leaking stolen data. The hackers believe that negotiation games are only making more money to insurance companies and intermediaries, so they’re not interested in any of that. It’s simply “pay or grief” with no time wasted for anything.
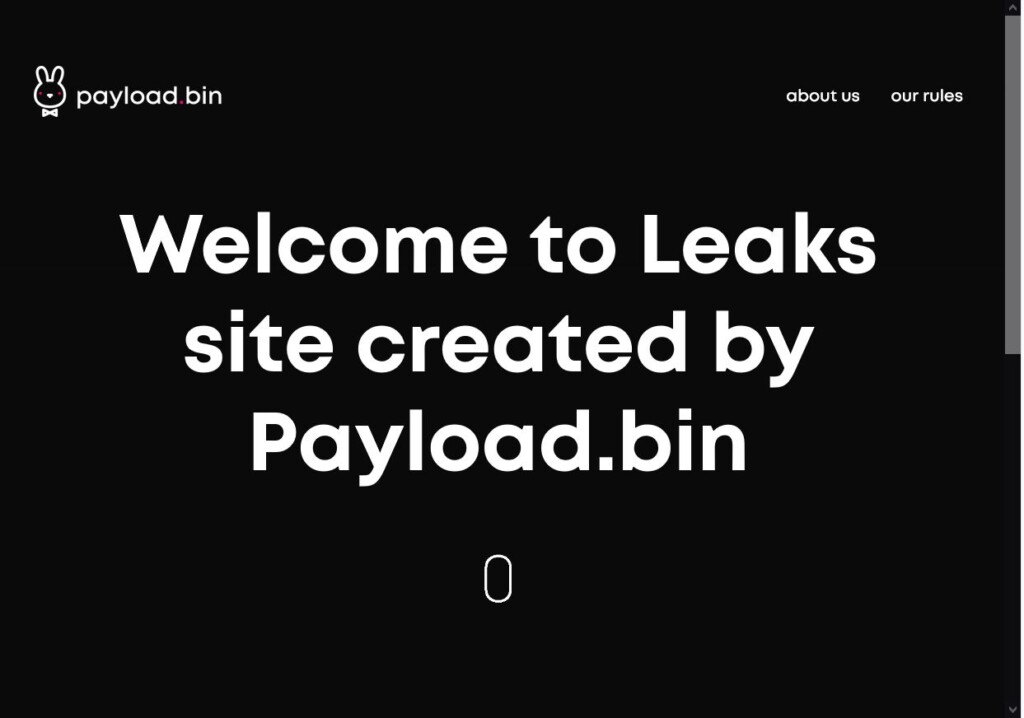
And then we have Babuk, who delivered on the promise to stop doing the “ransomware encryption” thing and just focus on network intrusions and data-stealing extortion. The group has now launched the so-called “Payload Bin,” which is essentially a leak site. It already has the source code stolen from CD Projekt RED in that February 2021 "HelloKitty" ransomware attack, which is an interesting and pretty much unexpected entry to start with.