‘Netop Vision Pro’ Virtual Learning Platform Was Vulnerable to Malicious Attacks
- The popular classroom management solution "Netop Vision Pro" was found to be vulnerable to multiple attacks.
- An actor would eavesdrop and steal Windows credentials, screenshots, and even drop malware through the chat.
- The vendor was quick to push a fixing update for most of the flaws and will add full encryption soon too.
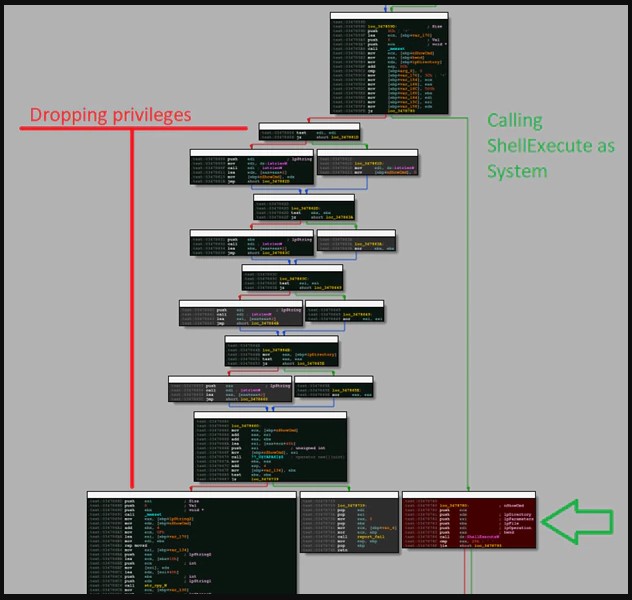
The McAfee Labs Advanced Threat Research team has analyzed Netop Vision Pro, a classroom management platform that is widely deployed right now by schools that have been closed due to COVID-19. Unfortunately, the researchers have discovered four previously unknown critical vulnerabilities, namely CVE-2021-27192, CVE-2021-27193, CVE-2021-27194, and CVE-2021-27195.
While no full technical details have been released yet (for obvious reasons), these flaws concern remote code execution, elevation of privileges, and system take-over scenarios. McAfee’s team reported its findings to Netop in December 2020, and the vendor fixed them in February 2021.
The software itself enables teachers to perform tasks on the student’s computers remotely, including quite invasive actions such as running apps, controlling desktop, blocking web access, or locking their computers. This creates an array of attack opportunities which is further magnified by unsafe default settings and the complete lack of network traffic encryption in the software.
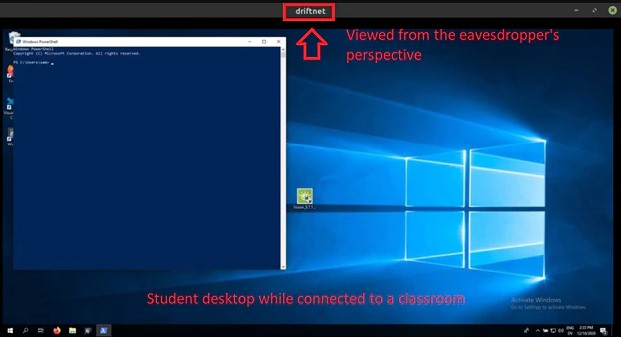
The researchers found out that they were able to even observe Windows user credentials in plain text, screenshots set between students and teachers, and every other data exchange that takes place through Netop.
Of course, an eavesdropper would have to be on the same local network as the students to capture the data packets that fly around. Being there enables the actor to find who else is connected and get a feed from their webcams as well without raising any alarms for the eavesdropped class.
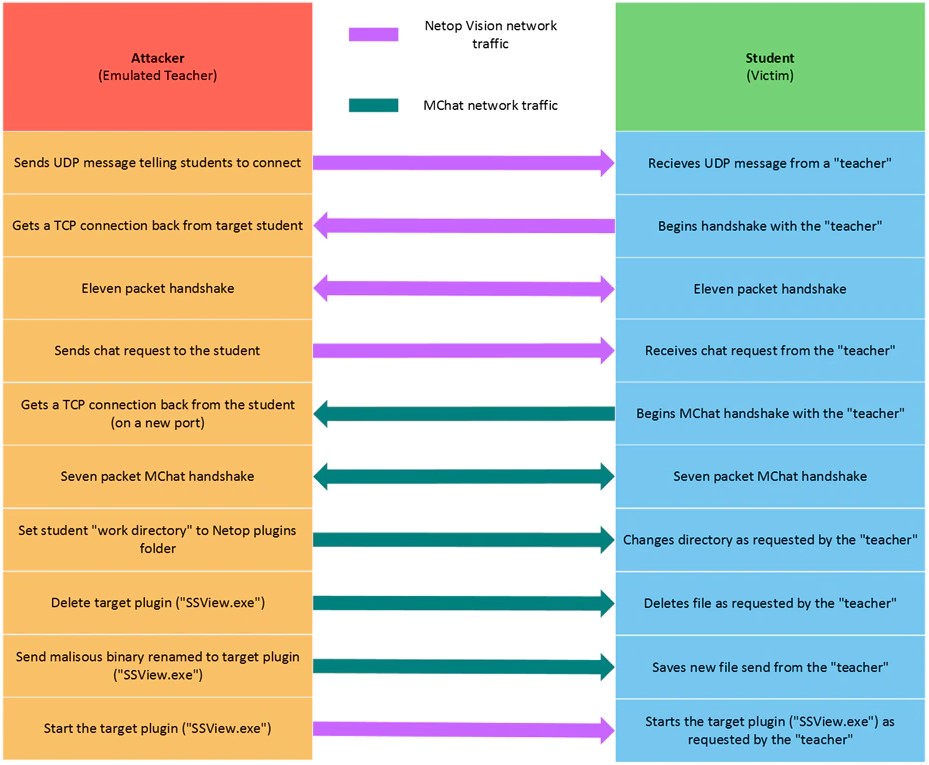
Apart from all that, the researchers proved that the embedded chat client called MChat is also vulnerable to exploitation. A malicious actor could disguise themselves as a teacher, drop files onto the student’s machine, run malware remotely, and do so through the Netop System privileges - all happening without the need to authenticate.
If you haven’t updated your Netop Vision Pro tool yet, go ahead and jump to version 9.7.2 or later. The vendor has fixed all of the reported problems, so local privilege escalation and arbitrary read/writes through the MChat client are no longer possible.
Moreover, Windows credentials are now properly encrypted, so eavesdroppers won’t get anything usable. However, the network traffic which carries the student screenshots is still unencrypted, but Netop promised to address that too in a future update.