Neiman Marcus Confirms Data Breach Linked to Snowflake Exposing 64,400 Customers
- Neiman Marcus acknowledged a security incident occurring in May that exposed sensitive customer details.
- The luxury retailer confirmed the data breach is connected to the company’s Snowflake account.
- Apparently, a hacker is selling the dataset, which allegedly includes names, addresses, phone numbers, and more.
Neiman Marcus Group (NMG) sent data breach notifications to its customers, acknowledging the security incident that occurred in May. The company said the sensitive details of 64,472 customers were exposed after the company’s account with a third-party cloud services provider called Snowflake was compromised.
NMG said they filed a data breach notification with the Office of the Maine Attorney General, informed law enforcement authorities, and notified affected customers. The firm’s investigation, with the help of cybersecurity experts, revealed that exposed data contained information such as names, contact data, and dates of birth, as well as ‘Neiman Marcus’ or ‘Bergdorf Goodman’ gift card numbers with no PINs.
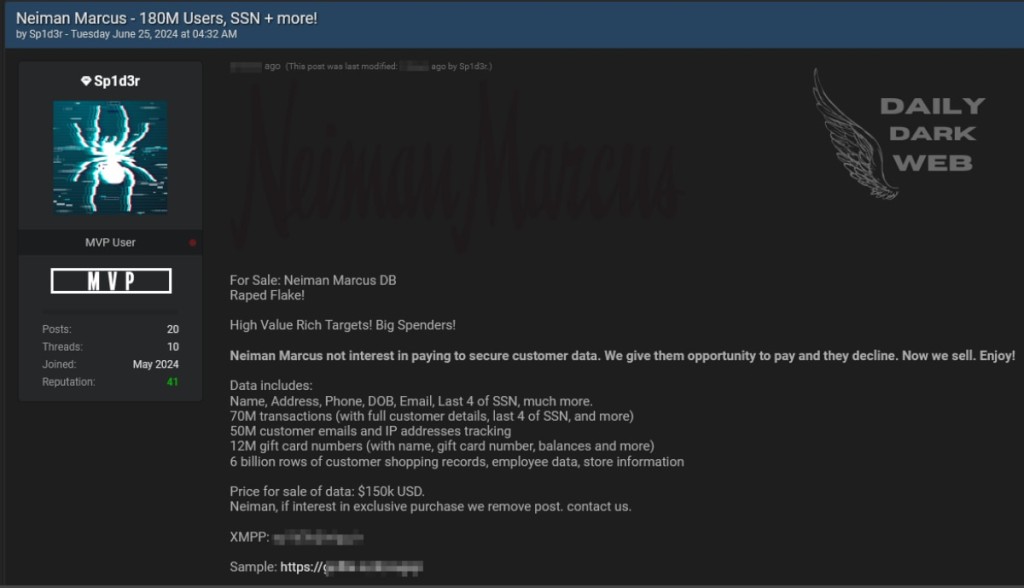
Shortly after the disclosure, cybercriminal Sp1d3r announced on a popular hacker forum that they were selling the exposed Neiman Marcus data. Soon after, the post was removed or hidden. It advertised having the customers’ names, addresses, phone numbers, dates of birth, email addresses, last four digits of Social Security Numbers, customer shopping records, employee data, and store information.
Earlier this month, hacker Sp1d3r was selling data reportedly stolen from cybersecurity company Cylance, including 34 million customer, prospect, and employee emails and from the Australian live events and ticketing company TEG (Ticketek Entertainment Group), which is believed to be related to a breach of the company's Snowflake account, but this was not yet confirmed.
The approximately 165 companies using Snowflake environments linked with the massive data breach include Ticketmaster, Ticketmaster, Santander Bank, LendingTree subsidiary QuoteWizard, Advance Auto Parts, and Pure Storage.
These breaches have been attributed to the UNC5537 threat actor. However, a member of the infamous ShinyHunters hacking group revealed earlier this month how they reportedly stole customer data from Snowflake accounts.
Incident response firm Mandiant said the data was stolen by threat actors leveraging leaked credentials collected by several info-stealer malware variants. These belonged to Snowflake customer accounts that did not have multi-factor authentication (MFA) enabled.