When you purchase through links on our site, we may earn an affiliate commission. Here’s how it works.
What Is a NAT Firewall, Why Is It Important, and Why Do So Many VPNs Use It?
"NAT firewall" is the kind of word you see paraded in marketing copy by VPN providers and highlighted as a must-have feature on VPN review sites.
It sounds cool, we'll give you that, but do you actually know what it is and why it's important?
If you don't, no worries. We'll go over this topic in-depth in this article, and we'll also try to make it as easy to understand as possible.
Even if you know what NAT firewalls are, give this article a quick scan, at least. Who knows, maybe you'll find out some new things. And if not, you can always send us your questions or ideas, and we'll add them to this article.
So, let's get started.
What Is a Firewall?
First, we need to take a look at what a firewall is. To keep things simple, just think of it as a layer of protection on a network.
Any data that leaves the network or gets sent to the network has to pass through the firewall. If it notices any suspicious traffic (like data packets you didn't request), it will discard it.
Here's a simple image to help you visualize what firewalls are:
What Is a NAT Firewall?
To fully understand it, we first need to let you know about two things:
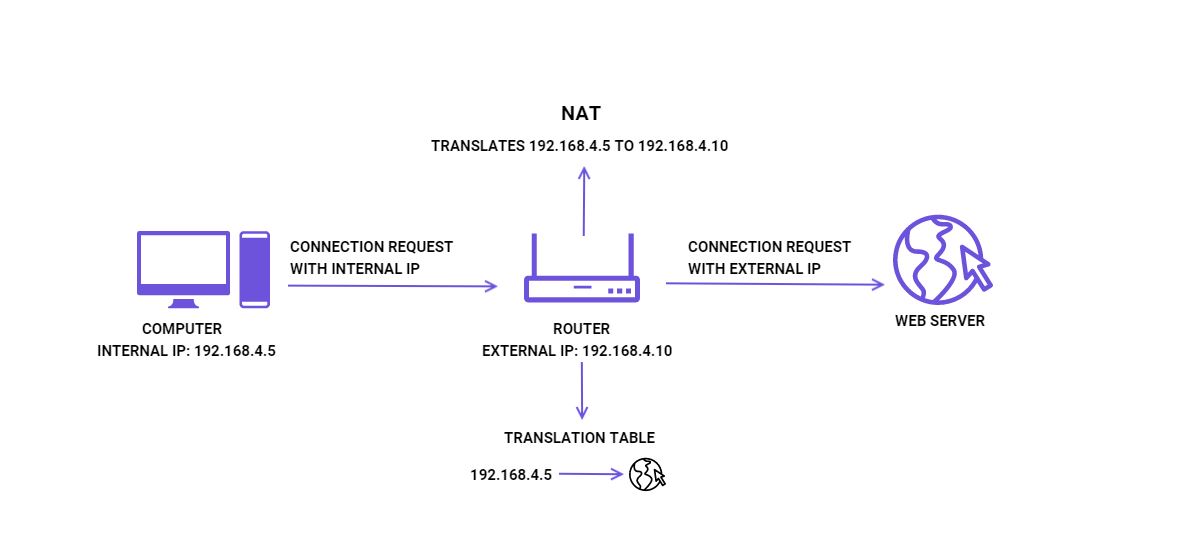
- Internal/External IP Addresses - Your ISP assigns your router an external IP address, which lets it communicate with the Internet. In turn, the router assigns each device on your local network an internal IP address. Only devices on your local network can see internal IP addresses, and they're basically invisible to external devices on the Internet.
- NAT (Network Address Translation) - This is how devices with internal IP addresses communicate with the Internet through one single external IP address (your router). Basically, your router acts as a middleman between devices on your local network and the Internet, and all internal IP addresses remain hidden when you go online. Also, NAT helps solve the fundamental issue with IPv4 addresses - their shortage.
Now, here's where the NAT firewall comes into play:
When internal devices communicate with the Internet, the router needs to sort a lot of data packets so that the requested web content is sent to the right device. For example, if you connect to Facebook on your smartphone, the router needs to make sure the requested website is delivered to your smartphone, not your computer.
The NAT firewall is part of that sorting process. It's a network security layer that allows your router to discard unwanted traffic that could potentially be malicious - like hackers trying to abuse unauthorized connections to take over your device, or malicious bots infecting your device and adding it to a botnet.
How a NAT Firewall Works - Simple Explanation
Feeling a bit lost?
No worries - these kinds of things are pretty complicated. To simplify this even more, here's a quick overview of how it all works:
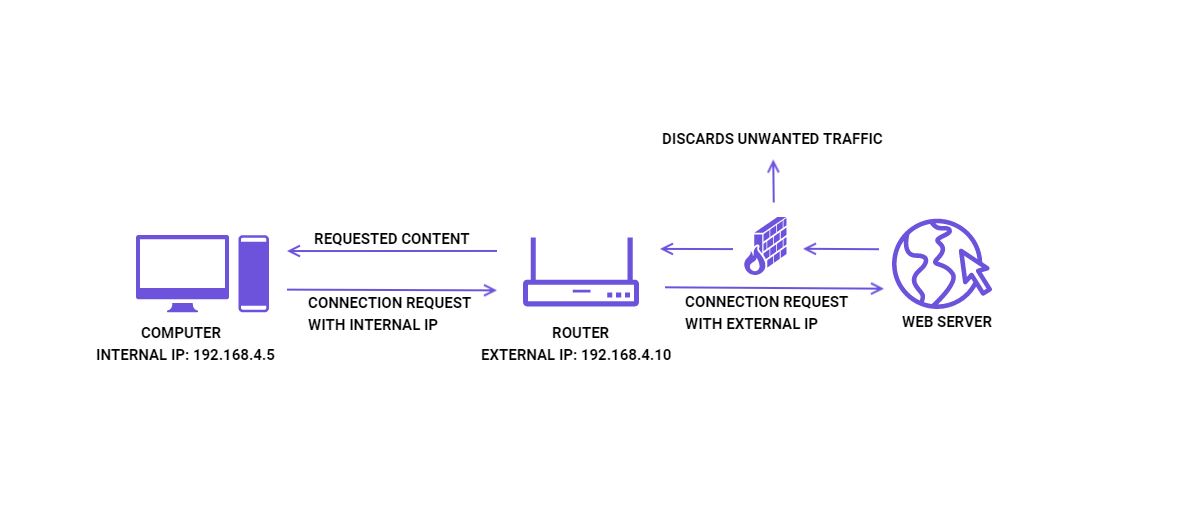
- You type in a website's name and hit enter.
- When you do that, your device will send a connection request to your router. Also, it identifies itself with its internal IP address.
- The router translates that request and forwards it to the site's web server using its external IP address. It also makes a note of the request's source - your device's internal IP address.
- The web server responds to your router with a copy of the website.
- The router checks the received content against the internal IP address that requested it. It discards any data that's not relevant and forwards the web site copy to your device via its internal IP address.
If you're still having trouble understanding how a NAT firewall work, just think of it as an office receptionist - you tell the receptionist not to forward any calls to you for the day. A bit later, you leave instructions telling the receptionist to forward calls to you from a specific client.
When someone calls the office, the receptionist will only put them through to you if they are that client. So they only do it if you previously requested to get those calls.
How Does a NAT Firewall Protect You?
As we said, NAT firewalls stop your devices and network from interacting with malicious traffic. Here's exactly how:
- The firewall checks the source of the data packets to make sure it's legit.
- NAT firewalls check that the received data packets are the ones you really requested.
- A NAT firewall discards any suspicious packets, such as the ones that have no internal IP address as a destination.
- NAT firewalls make it more difficult for hackers to discover open ports, inject malware, and execute certain cryptographic attacks.
Why Do VPNs Use NAT Firewalls?
You already have a NAT firewall on your router, right? That's true, but here's the thing - your router's NAT firewall can't sort and filter out data packets in your VPN traffic. Why? Because it's encrypted, and only the VPN client on your device and the VPN server can decrypt the data.
Simply put, your router's NAT firewall is completely blind when dealing with VPN traffic. It will automatically pass it back and forth without checking if the data packets are malicious or not.
Plus, some routers don't even interfere with VPN traffic due to a feature called VPN Passthrough. When enabled, that feature allows VPN connections to pass through the router without being rerouted or inspected.
tl;dr - if you only rely on your router's NAT firewall when using a VPN, malicious data can slip through.
How VPNs Use NAT Firewalls
VPN providers use NAT firewalls at the server level. Here's how it all happens:
- Once the VPN server receives your requests, it decrypts them and forwards them to the appropriate web server.
- When the VPN server receives the requested content, its NAT firewall will filter out any unnecessary packets.
- Then, the server re-encrypts the traffic and sends it back to your device, where the VPN client will decrypt it.
NAT vs. PAT
PAT stands for Port Address Translation and is sometimes used as an interchangeable term with NAT. So when some VPNs say they use a NAT firewall, they're actually referring to a PAT firewall.
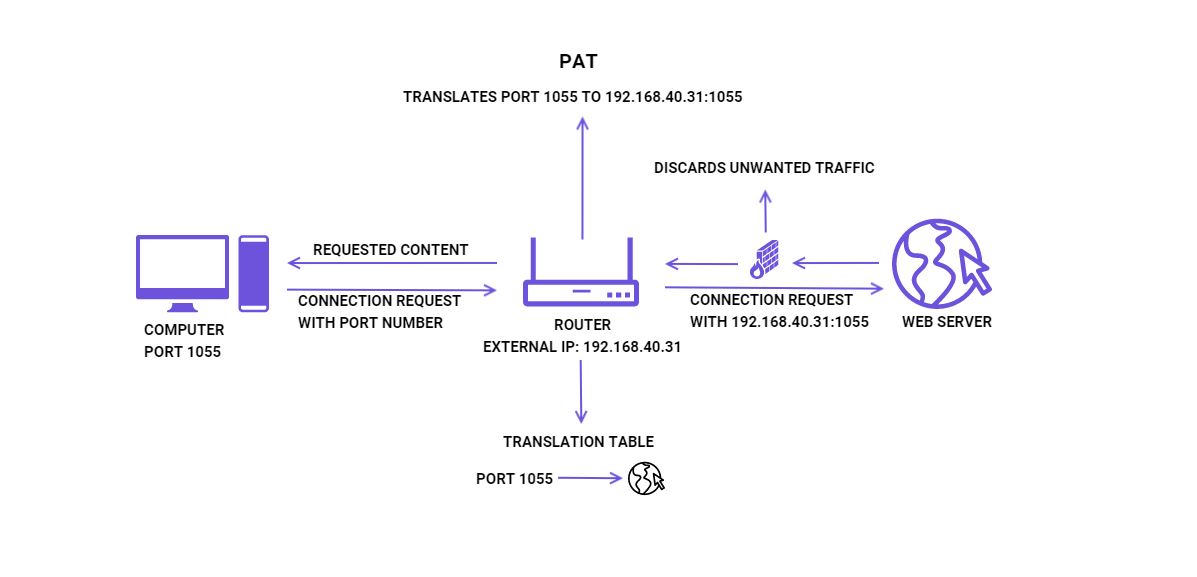
That's not very surprising since PAT does the same thing as NAT with just one small difference: instead of internal IP addresses, routers use port numbers to communicate with the web and keep track of devices on a local network.
For example, let's say you use your computer to watch a video on YouTube. Instead of directly translating its internal IP into an external one, the router will enable communications via the computer's port number.
So if the computer uses port 1055, and the router's IP is 192.168.40.31, the external IP for the computer via PAT will be 192.168.40.31:1055.
The router will keep track of the source port (1055) and its destination (website IP + port number) in its translation table. When it receives a response from the internet server, it checks its translation table, sees that port 1055 requested the content, and forwards the data to your computer (the device using port 1055).
Some VPNs prefer using PAT over NAT because of two reasons:
- They don't need to own as many internal IP addresses as they would with NAT.
- They can offer better privacy because all the traffic that leaves the VPN's server will have the same return address. Since there are usually tens or hundreds of people using the server simultaneously, it's pretty much impossible for anyone to associate a request with a specific subscriber.
Can NAT Firewalls Get in the Way of Torrenting?
Yes, it can happen. Your router's NAT firewall might consider your upload and download streams suspicious and could cut you off from seeders and leechers in the torrent swarm. That pretty much means you won't be able to upload/download torrents, or you'll only do it at a slow pace.
Luckily, most home routers have more "relaxed" NAT firewalls and don't penalize torrenting so much. They're usually stricter on more public networks - like at work, school, hotels, etc.
But if you're worried about your router's NAT firewall getting in the way, or you are experiencing slow speeds because of it, you could just use a VPN. Like we already said, it encrypts your traffic, so the router's NAT firewall can't block it.
It's true that the VPN's own NAT firewall could interfere, but that rarely happens. VPN providers normally configure them to allow P2P traffic - as long as the VPN itself permits it, of course.
Some VPNs also let you use port forwarding to get around their NAT firewalls, but we really advise against it. It's much safer to use a VPN whose NAT firewall doesn't restrict torrent traffic than to rely on a VPN who forces you to open your ports.
Why?
Because opening ports is more dangerous - after all, it makes it easier for hackers to track your traffic since you are using a special port.
Related: Find Out The Best VPN for Torrenting To Secure P2P Traffic
Which VPNs Offer NAT Firewalls?
Pretty much all the top providers on the market have it:
- NordVPN (Read Review)
- IPVanish (Read Review)
- VyprVPN (Read Review)
- PIA (Read Review)
- PureVPN (Read Review)
We should also add ExpressVPN as an honorable mention. They don't offer a NAT firewall, but they do have a decent article explaining why they don't use it. Basically, the service broadcasts your requests through different ports and keeps them closed when their servers send you replies. That offers a similar level of protection to NAT firewalls. If you'd like to see our review of ExpressVPN, follow this link.
Similarly, Surfshark's support reps told us their service uses a port-blocking policy to prevent unwanted and malicious traffic. If you want to read more about them, check out this review.
Make Sure You Also Use Antivirus Protection
Router and NAT firewalls are a great way to protect your network from malicious traffic. However, they can't protect you from malware 100% of the time. Even the smallest malicious code that slips through can put your entire device and network at risk.
What's more, a NAT firewall can't protect you from phishing. Antivirus protection will at least prevent malware infections, even if you accidentally click on a malicious link.
So we really recommend installing antivirus software on your device. Here are some of our top picks.
Also, you should consider getting a secure router. Many of them actually have built-in malware protection.
Stuck Using a VPN With No NAT Firewall? Use Glasswire With It!
Maybe you don't like any of our recommendations, or you're happy with the VPN service you have even though it doesn't have a NAT firewall. Or maybe you still have a few months to go with your yearly subscription and can't get a refund.
Whichever the case, there's something you can do - use Glasswire. It's a network monitoring tool that's pretty much a firewall, and it's free to use. It's relatively simple to use, and it shows all the apps on your device that are downloading or uploading data.
Even better, Glasswire makes it simple to detect suspicious apps and block their connections. The app also notifies you if any unusual changes happen in your apps ("unusual" usually meaning signs of malware).
Your antivirus should then take care of the culprits in question (detection + quarantine + removal).
If you're more tech-savvy, consider using Wireshark instead. It's also free to use, and - unlike Glasswire - it lets you inspect data packets more closely.
These tools are not the same thing as NAT firewalls, but they at least let you monitor your network traffic for suspicious activity. If you know other tools like Wireshark and Glasswire that offer similar or better functionality, let us know.
Conclusion
NAT firewalls are an essential security feature in all routers since they protect your network from unwanted, potentially malicious traffic. Unfortunately, when you use a VPN, your router's NAT firewall can't detect and block suspicious traffic.
That's why we recommend using a VPN that uses its own NAT firewall on its servers. That way, its servers will filter out any shady data. Of course, you should also make sure the VPN has other ways to secure your data - like powerful encryption, no-log policies, leak protection, and Kill Switches.
Are there any things we forgot to mention about NAT firewalls and how VPNs use them? Let us know in the comments or on social media, and we'll make edits if necessary.