Nasty PHP Malware Reinfects Cleaned Website Files in Less Than a Second
- PHP malware is used to initiate a persistent and powerful background process that can do it all on its own.
- The process is locking down target files and ensures that they are reinfected if cleaned or restored.
- The only way to catch these threats is through file integrity monitoring services that would generate accurate alerts.
Very few things can be more irritating for a website administrator than having cleaned up files reinfected with malware almost immediately. When this is combined with ignorance regarding the source of the infection, the situation can drive the admin crazy.
As Sucuri researchers report, this is precisely the case with a new PHP malware that stays hidden, reinfecting cleaned files and even locking them down, so the website owner cannot easily clean them.
The trick for the attackers lies in executing a background process, which is spawned by sending an HTTP request to the malicious PHP script, the “red.php.” This is what turns the malware on, while the background processes may follow with POSIX commands.
These can initiate a set of actions like the following:
- Check the Environment
- Lock File
- Make locked files modifiable
- View Function
- phpinfo
- php_version
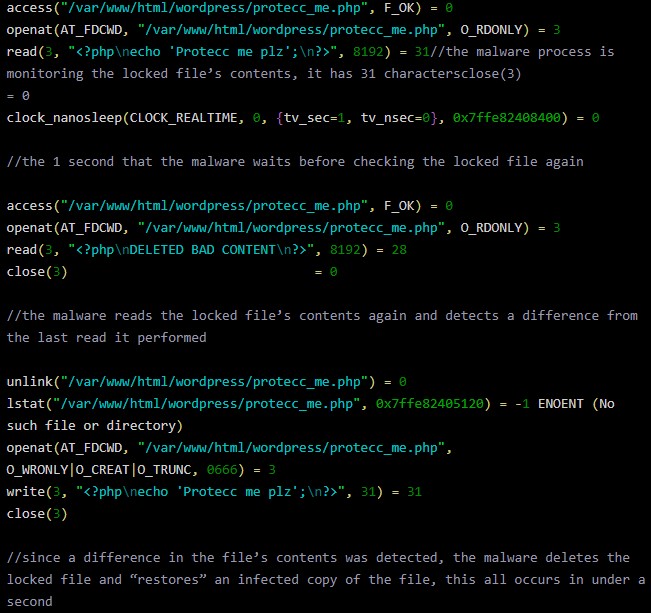
Even if the red.php is deleted at this point, the background process will continue to run, monitoring the infected website and retaining the capacity to run any of the above commands at any time. When the attacker targets a particular file, the background process will store its contents in $content, create a SHA1 hash value, and then store than in $hash_content. The hash value is then used for the monitoring and is compared with the locked reference every second.
Source: Sucuri
If the admin cleans the file or restores it, the process will catch the action within a single second. Should that happen, the malicious script will run the “file_put_contents” function, and the infected code in the targeted file will be restored, essentially reinfecting it. Since this occurs so quickly, the admin will be left perplexed as to what is going on.
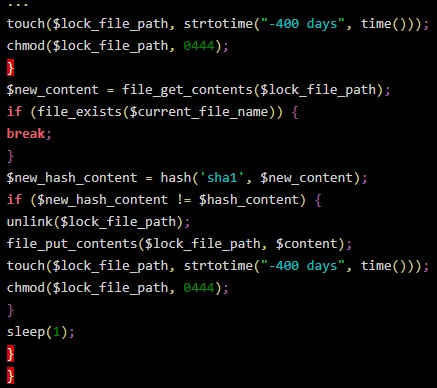
The background process is also tampering with the targeted file’s timestamps, subtracting 400 days from the current date with “-400 days.” This ensures that if the admin tries to review the logs to figure out what’s happening, they will be even more confused by what they’ll see.
And finally, to put an obstacle in the file’s modification, the malware is changing the file’s permissions to “read-only” though chmod. While this isn’t a serious blockage, it is still yet another nuisance for the admin.
Source: Sucuri
The only sure method to deal with malware like this is to deploy a file integrity monitoring service. In this case, checking the running processes would reveal the presence of the malicious background process, but this may not be the first thing that would come to the admin’s puzzled mind.
Read More:
- ESET ‘Mobile Security 6’ Released With a Powerful Anti-Trojan Feature
- New WordPress Malware Can Find and Disable Security Plugins
- The “TikTok Pro” App Is Essentially Spyware Under Disguise