Multiple Qualcomm Kernel Vulnerabilities Fixed With Android April Patch
- Zimperium is diving into the technical details of two Qualcomm flaws that affect Android devices.
- The presented vulnerabilities have dire consequences if exploited in the wrong way.
- Most Android devices out there will remain vulnerable to the flaws for many more months.
Back in July 2019, Zimperium discovered a set of critical vulnerabilities concerning Qualcomm chipsets powering Android devices. The flaws, which are codenamed CVE-2017-13253, CVE-2018-9411, and CVE-2018-9539, could potentially enable a malicious actor to achieve full root access on the target device without having to go through authentication. The consequences of this include access to private data, exfiltration of user credentials, the recording of audio and video by activating the device's cameras and microphone, the stealing of messages sent or received on WhatsApp and Telegram, access to email messages and attachments, and many more. Qualcomm published a relevant security bulletin in February 2020, and Google has incorporated the fixes in the most recent Android April patch.
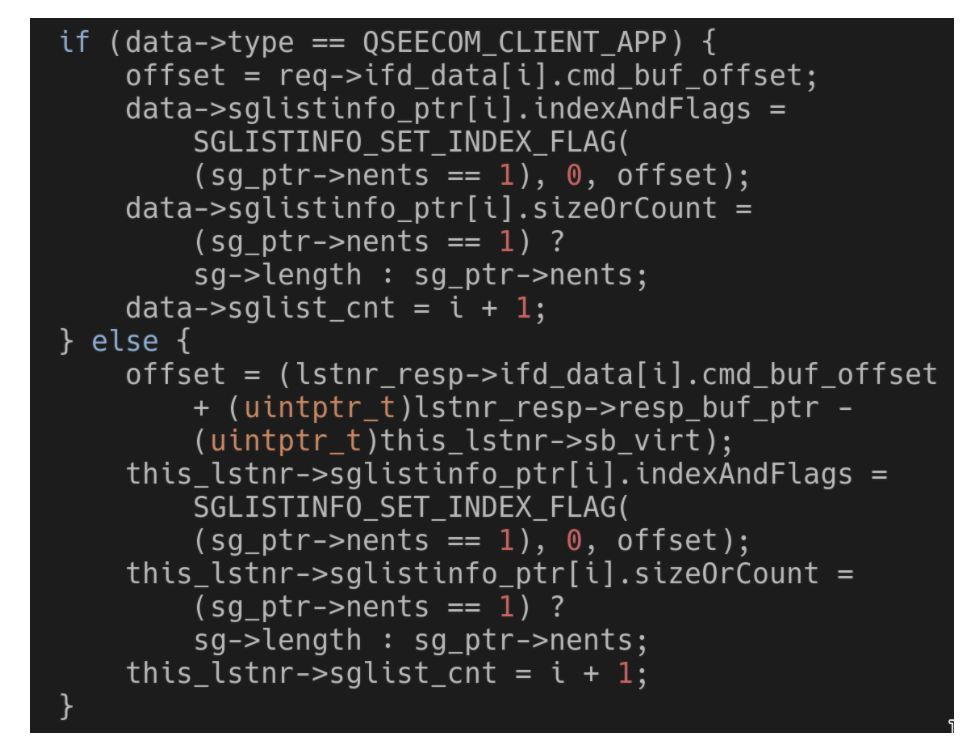
With the fixing update out, Zimperium was free to go deeper into the technical details of the Qualcomm flaws. First, there’s the race condition vulnerability which stems from the QSEECOM update function, how it behaves, and whether it can be modified while running. The researchers have found a way to instantly modify the data type of the component, bypassing the concurrent running limitations that are in place, which results in a race condition. Changing the data type of QSEECOM causes a memory corruption state. Depending on where the race hits, it may also result in a risky buffer overflow.
Source: Zimperium blog
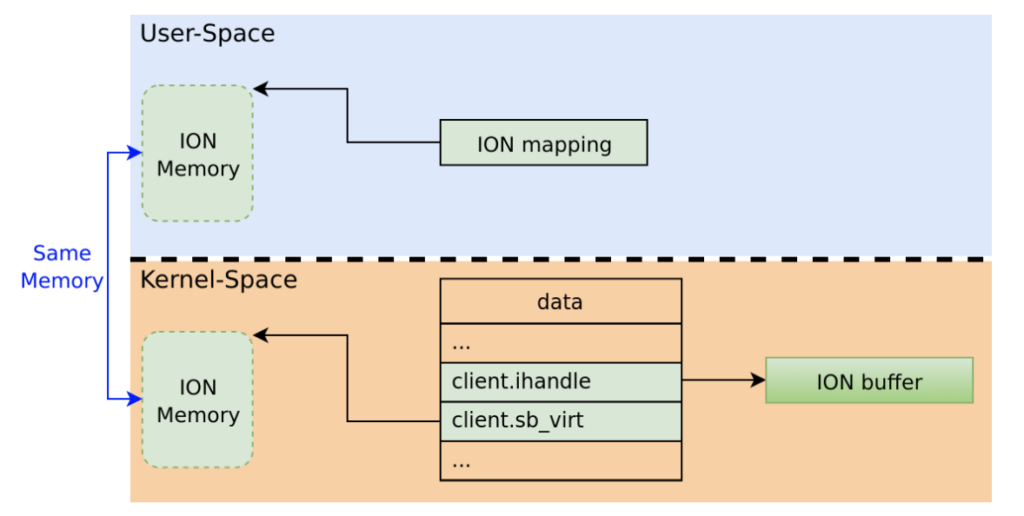
The second flaw is a “use-after-free” vulnerability that lies on the ION mechanism and how it works in conjunction with QSEECOM. ION can reference allocated buffers and map user-space processes into memory, linking the kernel communication with the TrustZone when needed. The kernel can modify the ION buffer independently, so if it is somehow set to “NULL,” the freed memory could be used for potential exploitation. There are checks in place to verify user-space-deriving requests, but the researchers have found a way to override them by using excessively large requests. By doing that, it is possible to force the kernel to modify a memory mapping that has been already freed.
Source: Zimperium blog
Source: Zimperium blog
Zimperium discovered the flaws on July 31, 2019, Qualcomm sent patches to vendors on November 4, 2019, Samsung incorporated the fixes on March 3, 2020, and Google distributed the patches as part of the Android security update that was released on April 6, 2020. The problem is that, for most users out there, the April 2020 patch will take many months to reach them - and for a significant portion of the market share, it never will.
Source: xda-developers.com
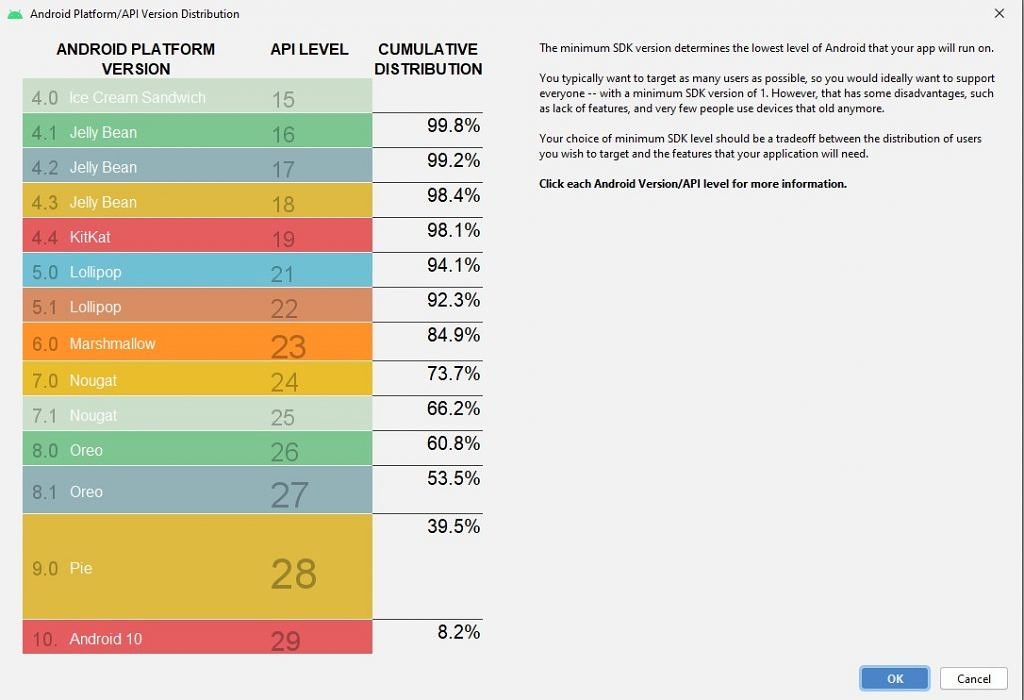
According to the most up-to-date Android platform version usage statistics (April 10, 2020), Android 10 is only used by 8.2% of the total number of active Android devices, version 9 “Pie” holds 31.3%, while the 8.0 and 8.1 “Oreo” versions account for 21.3%. The remaining 40% is unsupported, so if you’re using an earlier version, you’re vulnerable to numerous flaws in addition to those the concern Qualcomm chips.