Multiple Chinese Hacking Groups Targeted Telecommunication Service Providers in Asia
- At least three Chinese state-sponsored APTs targeted large telcos in Southeast Asia.
- The actors exploited several of the now-patched zero-day flaws in Microsoft Exchange.
- The hackers demonstrated resilience and persistence, changing to different tools and infrastructure when discovered.
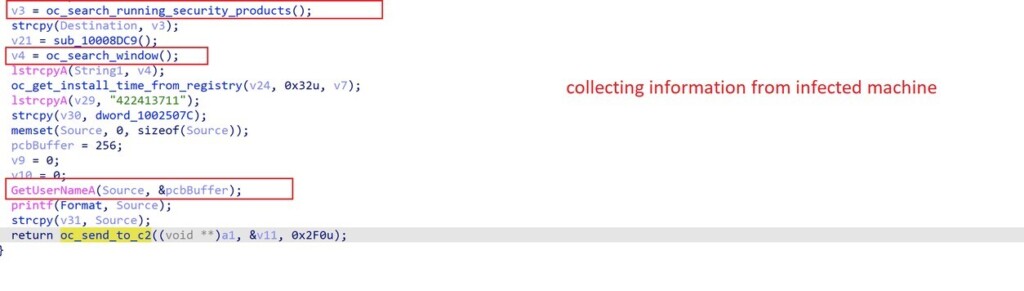
Since the beginning of 2021, there have been numerous attacks originating from various Chinese hacker groups, targeting large telecommunication service providers in Southeast Asia. The intruders' goal was to access sensitive information such as the "Call Detail Record" CDR data and compromise key network components like Domain Controllers, Web Servers, and Microsoft Exchange servers. In most cases, these groups exploited published MS Exchange flaws that went undiscovered for a long time.
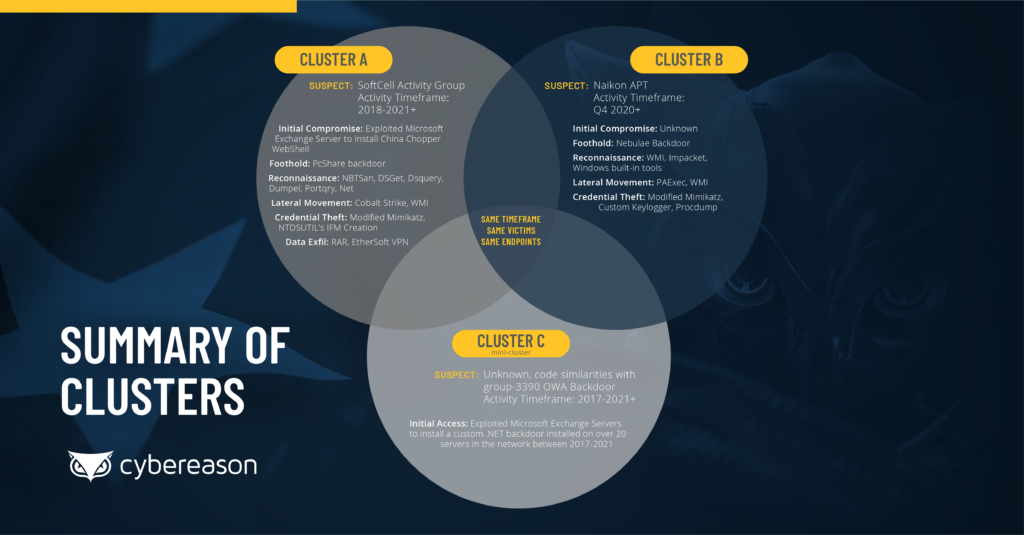
Security researchers of the Cybereason team have proactively hunted for attacks leveraging these exploits and found three large and frequently overlapping operations. These are attributed to 'Naikon APT,' 'SoftCell,' and 'Iron Tiger' (APT27/Group-3390), all Chinese actors specializing in cyber-espionage and links to the state. Unfortunately, the timeframe of these operations begins a long time back, with the earliest being in 2017, the other in 2018, and the most recent starting in the final quarter of 2020.
'SoftCell' was among the most careful, taking a "low and slow" approach to not raise any alarms. When they eventually did, they changed toolsets, infrastructure, and techniques in order to continue operating undetected. During the 2.5 years of their operation, they used Cobalt Strike, Mimikatz, WMI, NBTscan, SoftEther VPN, and the PcShare backdoor.
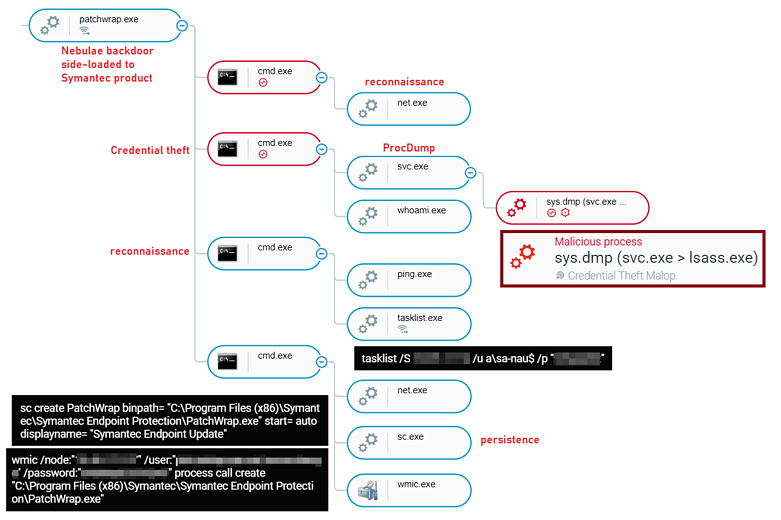
'Naikon APT' deployed the Nebulae backdoor, which relied upon DLL side-loading to execute attacks using legitimate executables while avoiding detection. If that channel was blocked, the actors simply changed the abused executable, preferring to exploit an antivirus product trusted by systems and users alike. This group followed "living off the land" reconnaissance practices and used tools that are built into Windows.
The 'Iron Tiger' used a custom 'OWA backdoor' to exfiltrate data, obfuscating the .NET binary through .NET Reactor. The backdoor is planted into a Microsoft Exchange server, and from there, it can fetch more payloads on command.
The targeted telcos weren't named, and the magnitude of the compromise of sensitive customers like organizations and individuals cannot be assessed right now. To appreciate this with accuracy, it would require an internal investigation conducted by the telcos. However, the fact that the actors persisted for two and three years indicates that they had some success in exfiltrating valuable information. This is further backed by their insistence on changing tactics, infrastructure, and toolsets once they were discovered.