Iran’s MuddyWater New Backdoor Phishing Campaign Targets Israeli Organizations
- Iranian government-backed cyber espionage group MuddyWater was seen deploying a new malware campaign.
- The phishing operation uses PDF-embedded URLs that download malware, with lures like invitations to webinars.
- Most of the targets are Israeli organizations, with over 50 such emails sent to representatives.
The MuddyWater threat group affiliated with the Ministry of Intelligence and Security (MOIS) in Iran, which has significantly increased its activities in Israel since the Israel-Hamas war began in 2023, was observed deploying a new malware campaign, and in at least one of the cases, it reverted to using a homemade implant for its first infection stage.
The Iranian government-backed cyber espionage gang usually aims to deploy legitimate Remote Management Tools (RMM) such as Atera Agent and Screen Connect. Recently, it added a new, previously undocumented tailor-made backdoor named BugSleep by Checkpoint security researchers and MuddyRot by Sekoia TDR analysts.
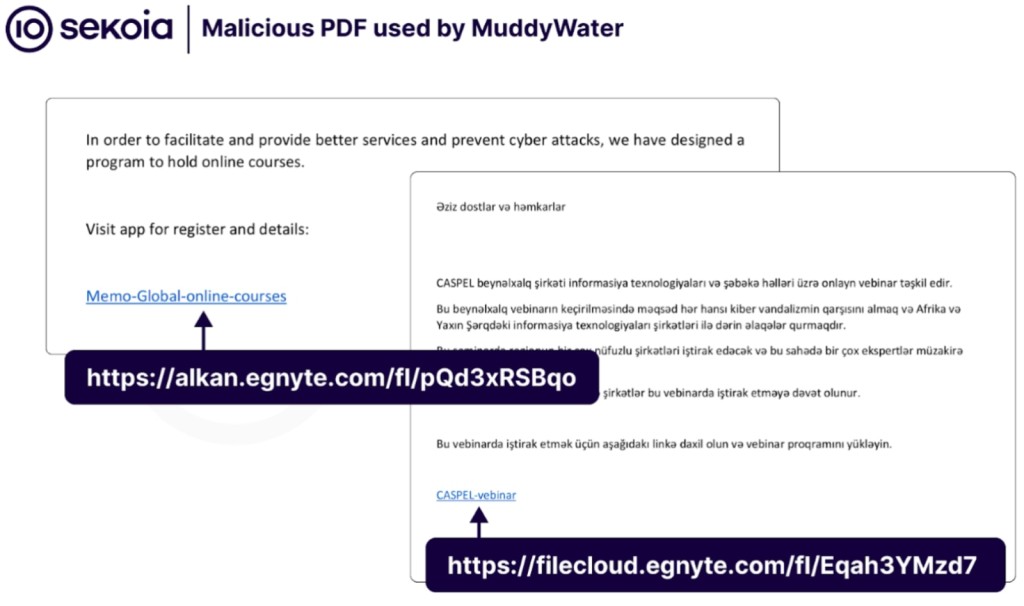
The targets are specific sectors such as municipalities, airlines, travel agencies, and media outlets, as per a Checkpoint report. The campaigns, however, use simpler lures compared to highly customized ones used before, such as invitations to attend webinars and online courses.
The group’s spear phishing campaigns were sent from compromised organizational email accounts; more than 50 such emails sent to hundreds of targets across 10 sectors of the Israeli economy have been documented since February. Others were aimed at entities in Turkey, Saudi Arabia, India, Jordan, Azerbaijan, and Portugal.
The still-developed custom backdoor designed to execute the threat actors’ commands and transfer files between the compromised machine and the C&C server was seen in several versions that revealed improvements and bug fixes.
MuddyWater group uses public exploits to compromise Internet-exposed servers, such as Exchange or SharePoint servers. Previously, their malicious emails had a link to an online storage service hosting a malicious ZIP archive hiding malware, but the latest campaigns changed to embedding the links in PDF files.
In the attacks targeting Israeli municipalities, the emails promoted a non-existent municipal app "designed to automate tasks, enhance efficiency, and ensure maximum safety in operations,” Checkpoint researchers say. The URL didn't download an app but the malware, which supports various commands, including uploading and downloading files, reverse shell, and process kill.