MongoDB Honeypot Experiment Generates Interesting Data
- Researchers have set up an unprotected MongoDB honeypot for three months and recorded 428 attacks.
- Most of the attacks came from automated bots that search the net 24/7 for unprotected instances.
- It took the first attackers roughly 7.5 hours to access the database, and then sent about 20 requests per day.
Bob Diachenko and his fellows in Comparitech had conducted a follow-up experiment of what they did last month when they left an unsecured Elasticsearch honeypot online for eleven days to see what happens.
This time, the researchers created a MongoDB database and kept it on an unprotected server for three months. This extensive period enabled the team to gather more insightful data, and indeed, the large number of attacks they recorded provides a broader spectrum of access types.
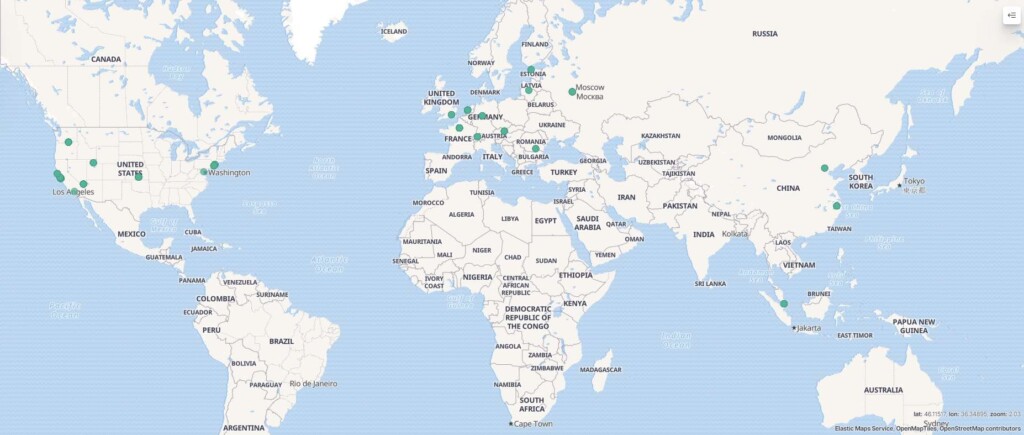
The experiment ran from December 6, 2019, to March 7, 2020, with the team recording a total of 428 unauthorized access attempts. The majority (218) of the access requests to the honeypot came from USA-based IP addresses, with the Netherlands coming second (51), and France third (34). Singapore and Russia also had a noteworthy number of attacks, whereas China is interestingly missing from the top places.
This could very possibly be a deceptive statistic, though, as the IP addresses are almost certainly not indicative of where the attackers are really based. Hackers use VPNs and pick a USA-based server simply because they are less likely to be blocked this way.
Source: Comparitech
About a third (127) of the scans came from legitimate entities like IT security companies. One hundred thirty scans were status checks that cannot be attributed either to malicious or well-intended actors. One hundred thirty-seven scans were requests aiming to view, scrape, and download the data, so these were clearly attempting to steal the data.
The remaining 34 requests were clearly destructive, with the actor downloading the data, deleting it from the server, and often leaving a ransom note behind. As the researchers explain, a large portion of these requests came from bots, which is another indication of the automation that takes place in the field.
Source: Comparitech
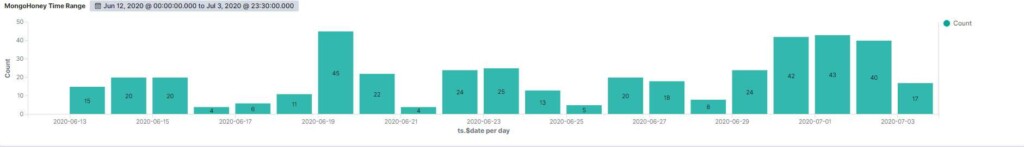
As for the attack volume and the timing stats, the first one came 7.5 hours after the honeypot’s initial exposure, which is more or less the same that we saw in the Elasticsearch experiment.
The average number of daily requests is 20, while the peak value was reached on January 6, 2020, with 43 requests. The reason for this was that the database was indexed by specialized search engines (Binary Edge, Shodan), so it came up in the results of sweeping bots like the “Conficker” and “Gamarue.”