Monero Bug May Have Exposed the Privacy of Transactions for a Small Number of Users
- Monero transactions could be de-obfuscated thanks to a nasty bug in the decoy algorithm.
- The flaw affects transactions made quickly after a user received new funds and went on to spend them.
- Monero says a fix will be coming shortly on the official wallet, but until then, wait for at least an hour before spending.
An extremely risky bug was found in Monero which may have exposed the privacy of the transactions of a small number of holders of what is considered to be one of the most securely anonymous crypto coins out there. The bug impacts users who spend their funds soon after they received them, with the threshold being probably at around 20 minutes. As the vulnerability remains present in the official wallet code, users of Monero are advised to wait for at least an hour before they spend any newly-received funds.
The Monero developers have promised a fix to land soon and also clarified that a full network upgrade is not needed to address the particular flaw. Also, users are assured that their funds are at no risk of being stolen, and nothing about the transaction amounts or the addresses is revealed, yet this is still a serious problem and a huge privacy liability for the decentralized ledger. And to make it worst, the bug appears to have always been there, so it’s just that nobody had spotted it previously. This means that past transactions are impacted.
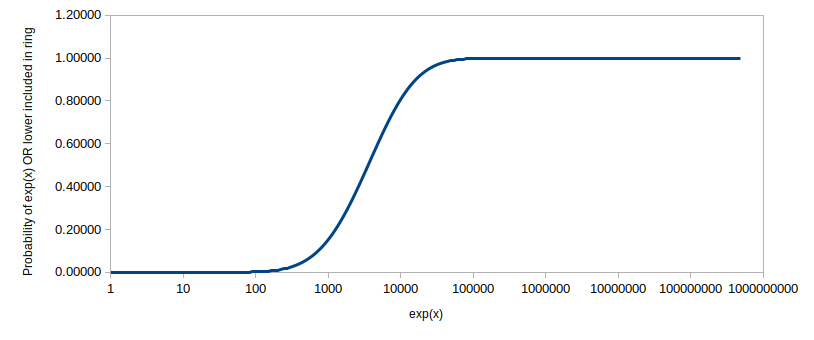
The problem lies in Monero’s decoy selection algorithm which leaves outputs that are spent immediately after the lock lifts to be easily identifiable in rings. As the team explains on GitHub, the selection of the 10 decoys for the output is done by an algorithm that relies on “gamma distribution”, which is in turn directly linked to a time counter that starts after the reception of an amount. At about 1,000 seconds or roughly 17 minutes, the diversion of the decoys is still not great enough to ensure that taking an average output time won’t be close to the actual value, so the real transaction could be identified.
In practice, this should affect only a small portion of Monero users, but until a fix is out, you should better wait for at least an hour before you spend your newly received funds anywhere. Even if this bug wasn’t the case, there are other time-related factors that should prevent you from doing that.