Misconfigured Jupyter Apps Exploited for Illegal Sports Streaming
- Hackers abused unsecured JupyterLab and Jupyter Notebooks servers to stream sports illegally.
- Threat actors managed to hijack environments due to a lack of proper authentication measures.
- The exploit could lead to denial-of-service attacks, data manipulation, theft, and corruption of critical AI and ML processes.
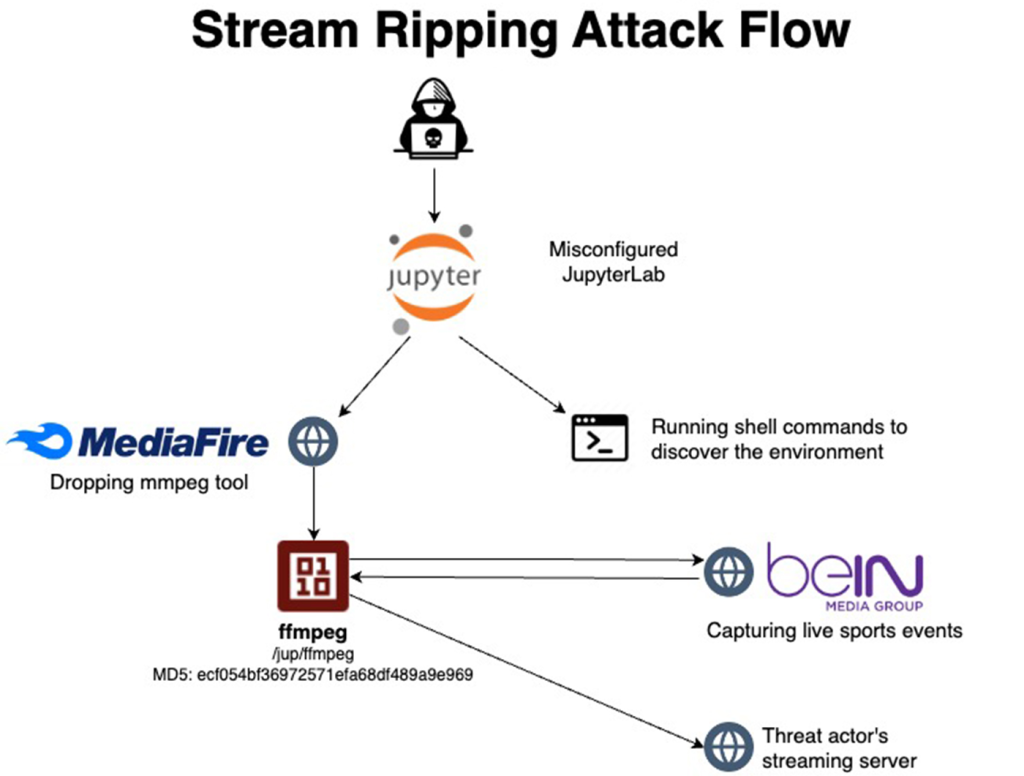
Hackers have been exploiting unsecured JupyterLab and Jupyter Notebooks servers to conduct illegal sports streaming. This revelation highlights a significant vulnerability in widely used data science environments, as uncovered by cloud security firm Aqua in a recent report.
The attackers are leveraging misconfigured Jupyter Notebooks, which lack proper authentication, to gain initial access. Using these compromised environments, they conduct a twofold operation involving updating the server and downloading the live stream capture tool, FFmpeg.
However, as noted by Aqua, this activity often goes undetected by standard security tools due to its seemingly benign initial actions.
Once FFmpeg is executed, the hackers capture live streams of sports events from networks such as the Qatari beIN Sports and reroute them to their server for unlawful broadcasting via ustream[.]tv.
This makeshift broadcast exploits Jupyter Notebooks' server resources and provides profit opportunities through advertising revenue from illegal streams.
The implications of such unauthorized access extend beyond digital piracy. Morag warns of severe risks, including potential denial-of-service attacks, data manipulation, theft, and corruption of critical AI and ML processes.
Additionally, the possibility of lateral movement into more sensitive environments could lead to significant operational disruptions, financial loss, and reputational damage.
While the masterminds behind the campaign remain unidentified, certain clues hint at an Arab-speaking origin, suggested by one of the specific IP addresses involved (41.200.191[.]23).
In other news, LaLiga published a September report that claimed its anti-piracy unit tackled illegal platforms, some of which were owned by Google. The latter is accused of indirectly endorsing piracy by standing idle while illegal IPTV services prosper.