Microsoft Warns About a Widespread Phishing Campaign Which Abuses Redirector Links
- Microsoft has uncovered a large-scale credentials phishing campaign that relies upon hundreds of domains.
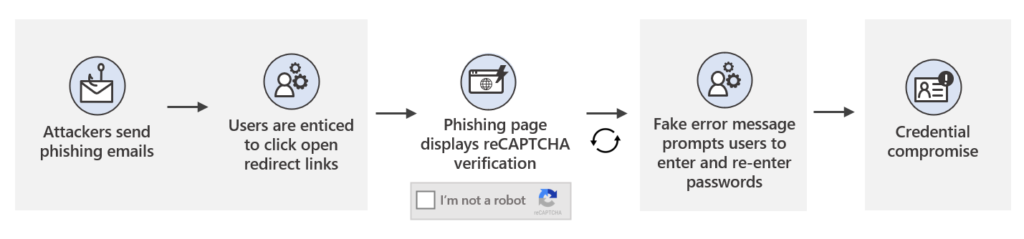
- The actors are using redirections, CAPTCHA verifications, and fake error messages to convince the victim and trick security systems.
- The phishing pages where the victims land can be highly customized even featuring their employer’s logos.
Microsoft has uncovered a new large-scale credential phishing campaign that abuses redirector links while also impersonating well-known productivity tools and services and engaging in social engineering. As the tech giant explains, redirections in email communications are very common as organizations try to get their customers to landing pages, track their click rates, and log metrics.
Phishing actors like to abuse these redirections as they can help them take users to a malicious website after bouncing them around on “clean” sites, tricking both the recipients and potentially any internet security tools they rely upon.
To further strengthen their campaign, the particular actors use a wide selection of domains from multiple countries, compromised websites, and attacker-owned DGA domains. This creates a pluralism that makes the infrastructure difficult to map and flag, so the actors continue delivering messages without many blocking problems. Microsoft says they have confirmed at least 350 unique phishing domains used in this campaign, but these are likely only a part of the total scale of the infrastructure.
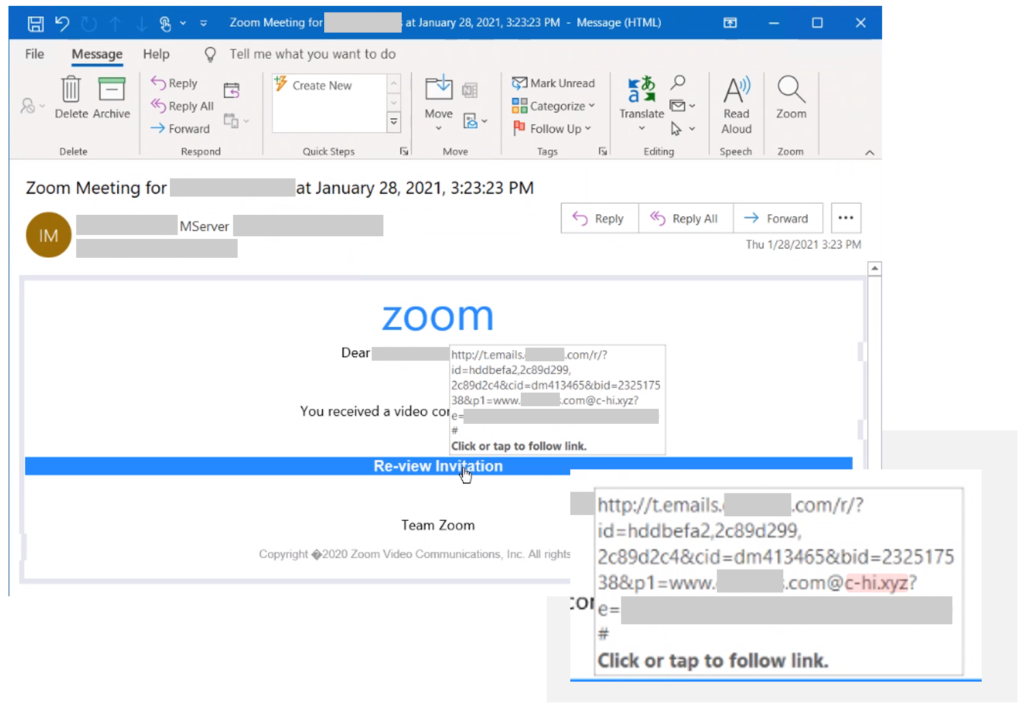
The goal of the actors is to steal credentials from their victims and then use them to infiltrate corporate networks. The general pattern followed in this campaign is to embed a large login box on the message body, urging the recipient to click on it on a fake pretense. Sometimes it is to receive an important file through a cloud service - other times, it is to address a password expiration problem, and in some cases, it is to view a Zoom invitation.
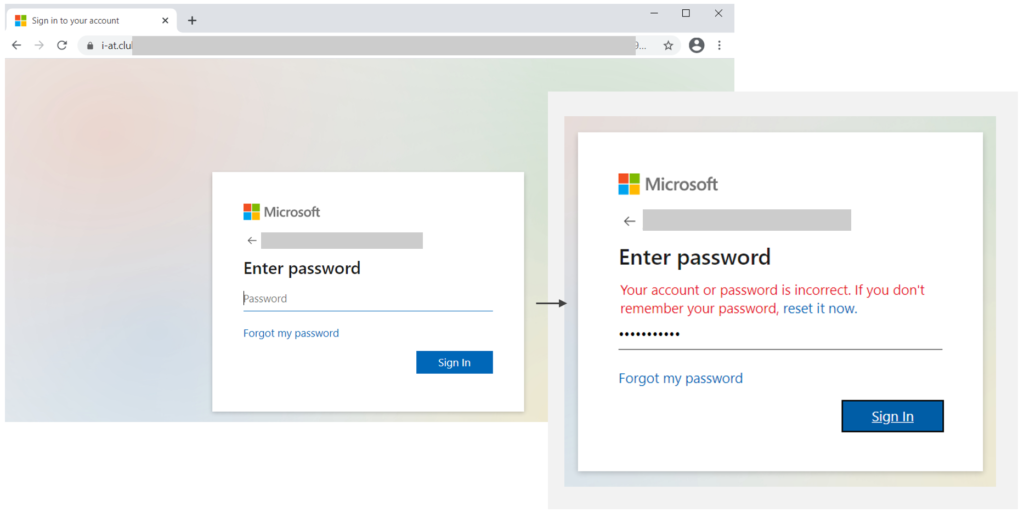
The redirection that takes place after clicking on the button typically includes a reCAPTCHA step, which acts as a wall for dynamic scanning systems that could perform in-depth analysis, as well as an element of legitimacy for the victim. If the user completes the verification, they are taken to the actual phishing page, where they are asked to enter their password. Notably, the actors deliver highly customized pages at this step by using PHP parameters, sometimes even including company logos to match the victim’s employer.
Once the victim enters their credentials, they get an error message about the session being timed out or an incorrect password. Possibly, forcing the victim to enter the password twice is a way to ensure that the stolen pass is indeed valid, as making typing errors isn’t that unusual. Entering the password again takes the victim to a final redirection on a Sophos website that tells them the message has been released, ensuring that the victim won’t get suspicious that anything bad had happened.