Microsoft Unearths Large-Scale Phishing Operation Involving 300,000 Subdomains
- Microsoft has dug deep into ‘BulletProofLink’, after seeing one of their clients using hundreds of thousands of subdomains.
- The service is a premium one covering all aspects of phishing operations and ensuring maximum effectiveness.
- The platform is keeping the stolen credentials for itself and then sells them on the dark web for additional profit.
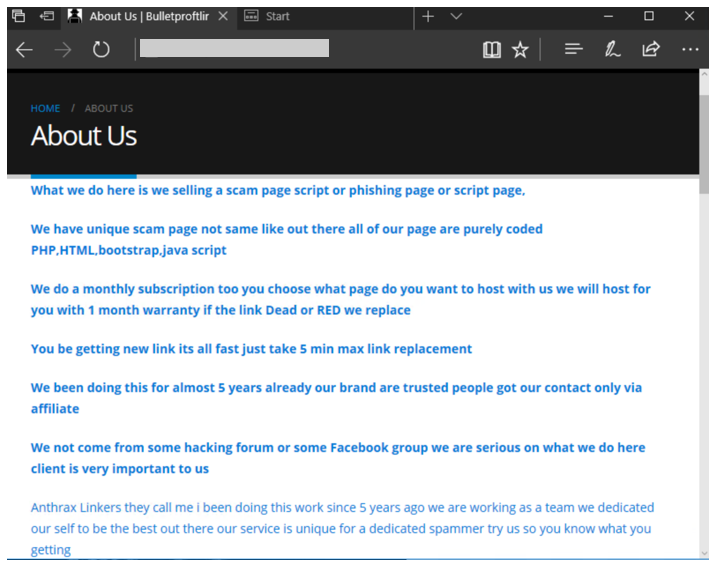
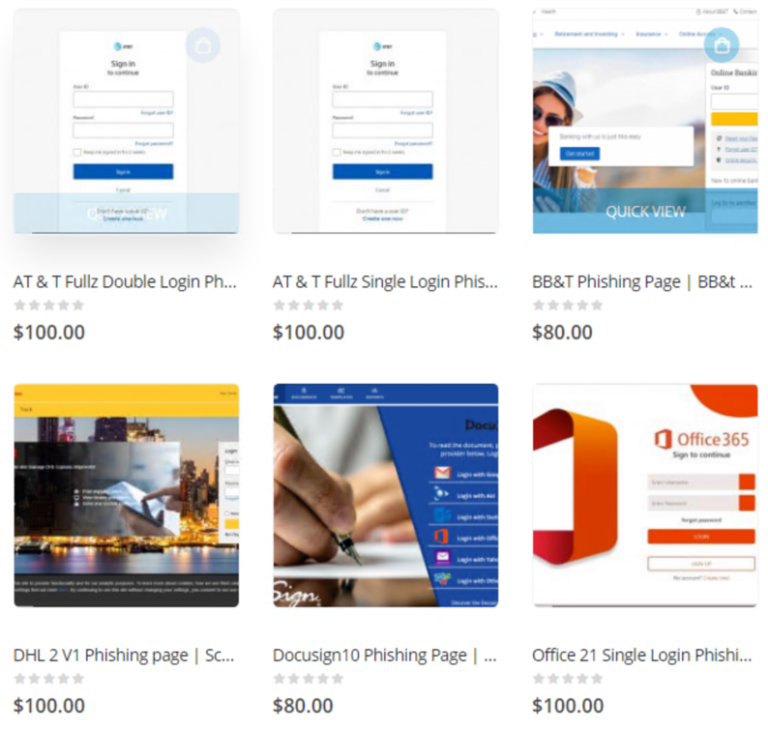
Microsoft's investigators have discovered a massive phishing campaign featuring 300,000 unique subdomains and over a hundred phishing templates made to mimic known brands and services. Soon, the researchers realized that this was actually part of a “phishing-as-a-service” (PhaaS) operation called ‘BulletProofLink’ (aka ‘Anthrax’), used by a large number of crooks who love the convenience of buying pre-fabricated kits and getting right to work. Even when needing to scale up to ludicrous levels, BulletProofLink can accommodate the need, creating behemoths like the one that Microsoft caught in the wild.
PhaaS is offered via a subscription model, so actors can buy themselves weekly, monthly, or even annual memberships. The program offers email templates to use in phishing messages, site templates for the landing webpages, email delivery tools for mass distribution, site hosting services, and even credential theft and redistribution. Of course, all of the above can be purchased individually, but this is the comfort of subscribing to a PhaaS. In the case of ‘BulletProofLink,’ we also have “FUD” (fully undetectable) links, meaning that email protection tools won’t catch the threat.
One trick used by the platform in order to evade detection from security tools is the “zero-point font” technique which renders characters that are invisible to the user. This is an effective obfuscation method that we analyzed last August, so make sure to look into that post if you’re interested in going deeper.
According to Microsoft, ‘BulletProofLink’ has been around since at least 2018, operating multiple sites as well as social media channels where they post phishing tutorials and various promotional materials. New subscribers are offered a 10% discount as a welcoming gesture, and there’s also chat support for those who need real-time help or advice. Additional themes and templates are sold separately, and there’s a galore of items to choose from. The full package may cost as much as $800 per month, putting ‘BulletProofLink’ in a premium category as most other RhaaS services cost about $50/month.
It is notable that in the case of the particular PhaaS platform, researchers spotted the “double exploitation” of the stolen credentials, which is deployed by ‘BulletProofLink’ operators to maximize their profits. The credentials that are stolen during an actor’s phishing campaign remain under the control of the kit vendor, who then resells them on the dark web.