Microsoft July 2021 ‘Patch Tuesday’ Brings 117 Fixes, 4 for Zero-Days
- Microsoft has released a large ‘Patch Tuesday’ pack, addressing 117 vulnerabilities.
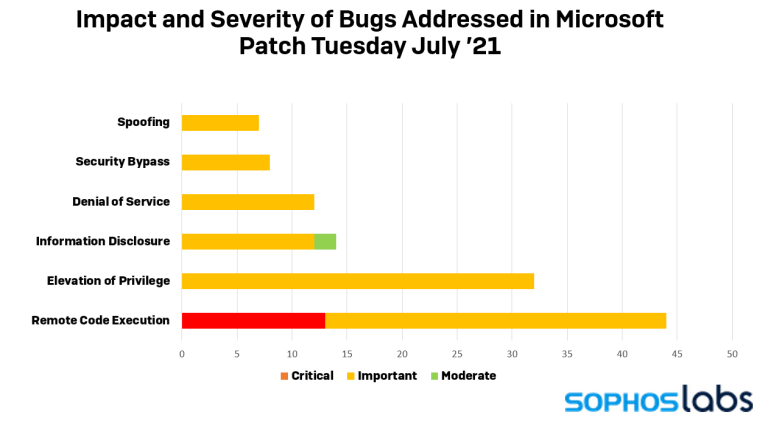
- Among them are four zero-days and a total of 13 critical flaws, one being the Print Spooler RCE.
Microsoft has released another ‘Patch Tuesday,’ and this month, we got fixes for no less than 117 vulnerabilities - 13 of which are critical and four actively exploited in the wild. One of these is a fix for the printing spooler service RCE that proved more complicated to address in the previous Patch Tuesday pack and remained unremediated since April when it was discovered.
Here are the most important fixes of this month’s patch:
- CVE-2021-34448: Scripting Engine memory corruption vulnerability. A critical flaw that is being under active exploitation.
- CVE-2021-33771: Windows Kernel elevation of privilege flaw that is rated as important and has been confirmed to be under exploitation.
- CVE-2021-31979: Another actively exploited Windows Kernel elevation of privilege flaw categorized as important.
- CVE-2021-34527: Windows Print Spooler remote code execution vulnerability that has been under exploitation for months now. Is rated as critical (CVSS – 8.8). Changed tracker ID from CVE-2021-1675.
- CVE-2021-34474: Critical (CVSS – 8.0) RCE flaw in the Dynamics Business Central.
- CVE-2021-34464 and CVE-2021-34522: Critical (CVSS – 7.8) RCE vulnerability in Microsoft Defender.
- CVE-2021-34473: Critical (CVSS – 9.1) RCE bug in Microsoft Exchange server.
- CVE-2021-34439 and CVE-2021-34503: Critical (CVSS – 7.8) remote code execution flaw in Microsoft Windows Media Foundation.
- CVE-2021-34494: Critical (CVSS – 8.8) vulnerability in Windows DNS server.
- CVE-2021-34450: Critical (CVSS – 8.5) RCE flaw in Windows Hyper-V.
- CVE-2021-34458: Critical (CVSS – 9.9) remote code execution vulnerability in the Windows Kernel.
- CVE-2021-33740: Critical (CVSS – 7.8) RCE flaw in Windows Media.
RCE fixes took the lion’s share this time, as most of the addressed vulnerabilities were of that type. The rest concerned issues of elevation of privilege, information disclosure, denial of service, security bypass, and spoofing.
As always, you are advised to apply the security patch as soon as possible, but not before you backup your data. Remember, if an OS update goes wrong, you may end up with a corrupted filesystem, and many things can derail the process - like a power outage, for example. Due to the high number of zero-days and critical flaws addressed this month, the requirement to backup your data shouldn’t be an excuse for delaying the patch application.