Microsoft Edge Experimenting With a ‘Super Duper Secure Mode’ on Beta
- MS Edge engineers are now experimenting with JIT, disabling the performance-enhancer to address security problems.
- This has some impact on browsing speed, but it’s not something the majority of users would notice.
- Additionally, security mitigations that were previously incompatible with JIT will now be enabled.
Microsoft’s Edge web browser may soon get a new security-enhancing mode named ‘Super Duper Secure,’ and it’s basically the deactivation of the JIT (Just-In-Time) inside V8, the browser’s JavaScript engine. This is precisely the component that malicious actors like to target because it provides them with powerful exploit primitives, and there’s always a bug in there to exploit - and doing so is almost always pretty straightforward.
As Johnathan Norman of the Edge’s Vulnerability Research lab states, JavaScript engine exploitation has been following the same three-step pattern for years now, and little has changed on that front.
- Fake an object
- Get AddrOf Primitive
- Achieve arbitrary write
In cybersecurity, though, having a simple or obvious problem doesn’t mean it’s easy to fix. In the case of JavaScript engines, actors enjoy a steady stream of bugs anyway, so even if security teams deliver patches frequently, there’s always some margin for action. So, what difference does disabling JIT makes then?
“Just-In-Time Compilation” was introduced over a decade ago to help with performance by executing code while compiling it at run time without having to do this beforehand. The obvious problem that arises from this is that it can be abused by malicious JS code. In fact, over half of all “in the wild” exploits are JIT bugs, which is a big red flag for the otherwise helpful system. Disabling JIT automatically addresses half of all bugs adversaries can target and security teams must fix.
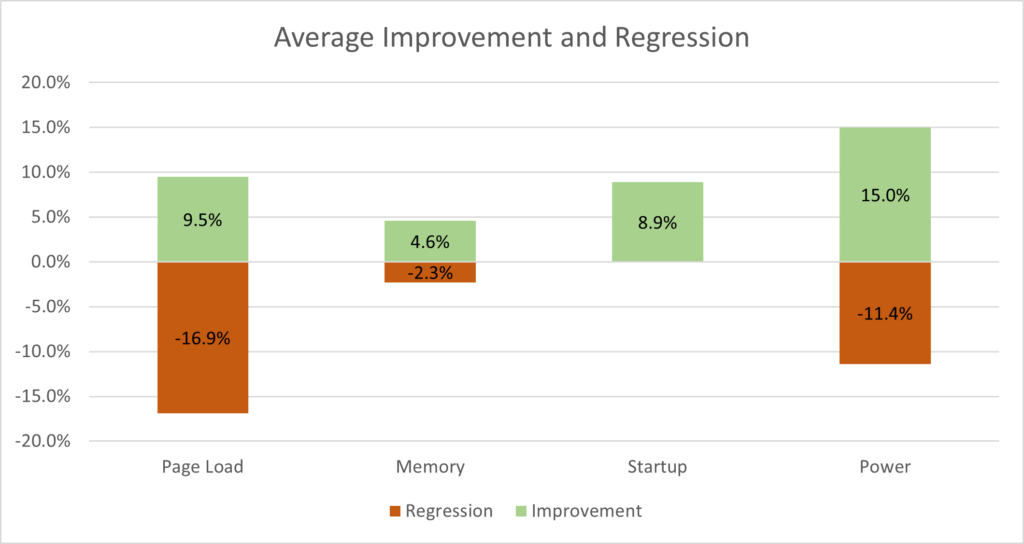
But if JIT is there to help with browsing performance, won’t this make things slow down? You see, computer hardware, internet connection speeds, and web browser engine optimization have all gone a long way since JIT was introduced back in 2008. Microsoft run hundreds of tests to determine if disabling JIT would have noticeable effects on the performance of Edge, and here’s what they came up with:
So, yes, there are some drops in page load speed, worse memory usage, and higher power consumption, but these changes aren’t big enough to be noticed by most users. This, of course, depends on what they’re doing online, as JS-intensive pages will suffer a bigger hit. All in all, it’s a trade for security, and it doesn’t only concern JIT itself.
You see, the existence of JIT prevented the Edge team from implementing other exploit mitigations such as ACG, CET, and CFG protection in the renderer process, which will now land on the beta and dev branches of the web browser in the context of the experiment. If all goes well, we may see ‘Super Duper Secure Mode’ on the stable version of the web browser soon.